Latest NSA leak details PRISM's bigger picture

New "top secret" slides released by The Washington Post on Saturday shed further light on the U.S. National Security Agency's (NSA) PRISM program, which was first publicly disclosed through a series of leaks by former government contractor turned whistleblower Edward Snowden earlier this month.
The additional four slides expand on the original leaks released by the publication The Guardian. They further back claims of widespread borderline illegal mass surveillance by Snowden, whose airside location at a Moscow airport caused a stand-off between the two former Cold War superpowers on a new diplomatic front.
The original disclosure blew the lid on government surveillance and the scope in which the U.S. government worked with the U.K. intelligence network, and stirred further anger over alleged secret interpretations of the Patriot Act and the Foreign Intelligence Surveillance Act (FISA).
Further leaks by The Guardian showed that the program is court approved by the secret Foreign Intelligence Surveillance Court (FISC), set up under FISA in 1978, but individual warrants are not necessary, even for requesting full access to a person's collected data.
While this latest disclosure expands what is known about the PRISM program, only eight of the total 40 or more slides have been published so far.
Over the weekend, the Post published further details of the mass collection of email, video and voice chat, photos, file transfers, and other online social networking content on foreign nationals by the NSA in conjunction with the Federal Bureau of Investigation (FBI).
According to one freshly leaked slide, there were 117,675 "active surveillance targets" in PRISM's database, but this figure does not detail which kinds of users these were, or among them how many Americans had their data collected inadvertently by the program.
Another slide detailed the PRISM "tasking process," which shows how an NSA analyst would acquire and search for new intelligence on a surveillance target.
These tasking requests are initiated by the NSA analyst, who will determine a new target and have this authorized by their supervisor, which under Section 702 of FISA will seek to ensure there is a 51 percent likelihood that the target is not a U.S. person, and are overseas at the time of data collection.
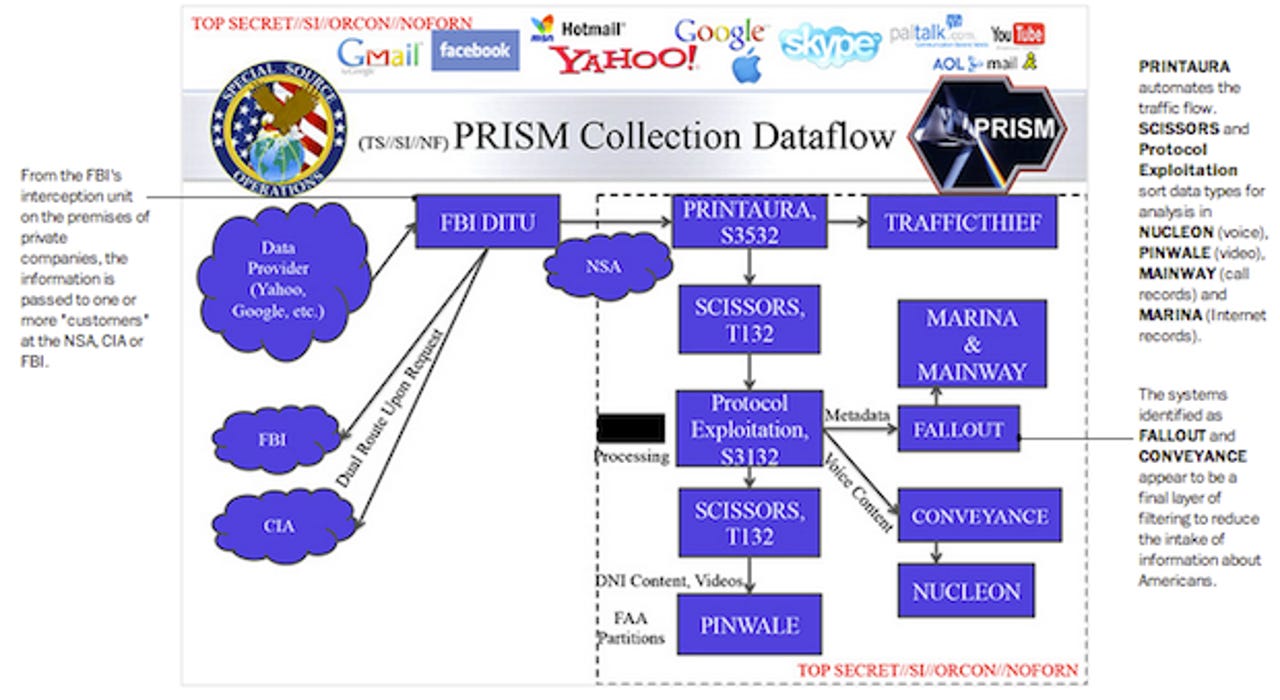
Annotations by the Post suggest that PRINTAURA "sorts and dispatches the data stream" into different categories of data from the FBI's Data Interception Technology Unit (DITU) — understood to be the Tier 1 company wiretaps.
The data collected from these wiretaps are then sorted into data types for further analysis by SCISSORS and Protocol Exploitation. The NSA is then able to determine what is U.S. citizen data, in line with the leaked "minimization procedures," which then filters through two further systems — FALLOUT system for metadata, and CONVEYANCE for voice content — to reduce the intake of intelligence on Americans.
Once this has been completed, foreign intelligence that filtered as much U.S. persons only data out as possible will pass into databased dubbed NUCLEON for voice, PINWALE for video, MAINWAY for call data, and MARINA for Internet records.
While the slides annotated by the Post claim that the FBI "uses government equipment on private company property" to receive such data, in another infographic-like post, the publication specifically states that a tasking request "is routed to equipment installed at each company."
The FBI's DITU is understood to maintain this equipment, in which the data it collects is then passed to the NSA.
In a ZDNet article earlier in June, we suggested that the aforementioned companies were likely not actively working or engaged with the NSA as was suggested — and subsequently rolled back on by the media. But the "private company property" were likely the Tier 1 network companies that provide the high-bandwidth lines behind the named seven technology companies' datacenter operations.
This also ties in with the Upstream program, in which, as later leaks pointed out, physical prism-like "beam splitters" would be used to split the fiber optic beams, where one stream would go to the destination while the other was copied and sent to an NSA datacenter.
This data copying and snatching would prove that the named seven technology companies were not in fact handing data over to the NSA, voluntarily or forcibly, without an appropriate warrant.
The named seven companies — AOL, Apple, Facebook, Google (and YouTube), Microsoft (and Skype), Paltalk, and Yahoo — scrambled immediately after the first disclosure to counter the claims mistakenly made by some that they gave the NSA "direct access" to their systems.
Many of those companies are also currently engaged with the Obama administration in a bid to lift the lid on the exact number of National Security Letters, or so-called "gagging orders," they receive from the U.S. government under Section 505 of the Patriot Act — a statute expanded under the new 2001 provisions.
The Post's earlier claim that the NSA had "direct access" to the companies was not repeated in the latest disclosure, and instead erred on the side of caution.
The publication also notes that a tasking request can be sent to "an NSA access point that taps into the Internet's main gateway switches."