Linux trailed Windows in patching zero-days in 2012, report says

Vulnerabilities in the Linux kernel fixed in 2012 went unpatched for more than two years on average, more than twice as long as it took to fix unpatched flaws in current Windows OSes, according security firm Trustwave.
Zero-day flaws — software vulnerabilities for which no patch is available — in the Linux kernel that were patched last year took an average of 857 days to be closed, Trustwave found. In comparison zero-day flaws in current Windows OSes patched last year were fixed in 375 days.
The gap in time between the patches being issued can partly be explained by the differing structures of open-source project communities and proprietary software vendors, according to John Yeo, director of TrustWave SpiderLabs for EMEA.
"In part it's related to the distributed nature of Linux development," he said.
"When you're talking about a vendor who's wholly and solely responsible for that particular product, it's somewhat easier for them to roll out a patch because it is very standardised.
"Whereas you might have different components or modules within the Linux kernel and many different people from an open source perspective who might be responsible for putting together a fix.
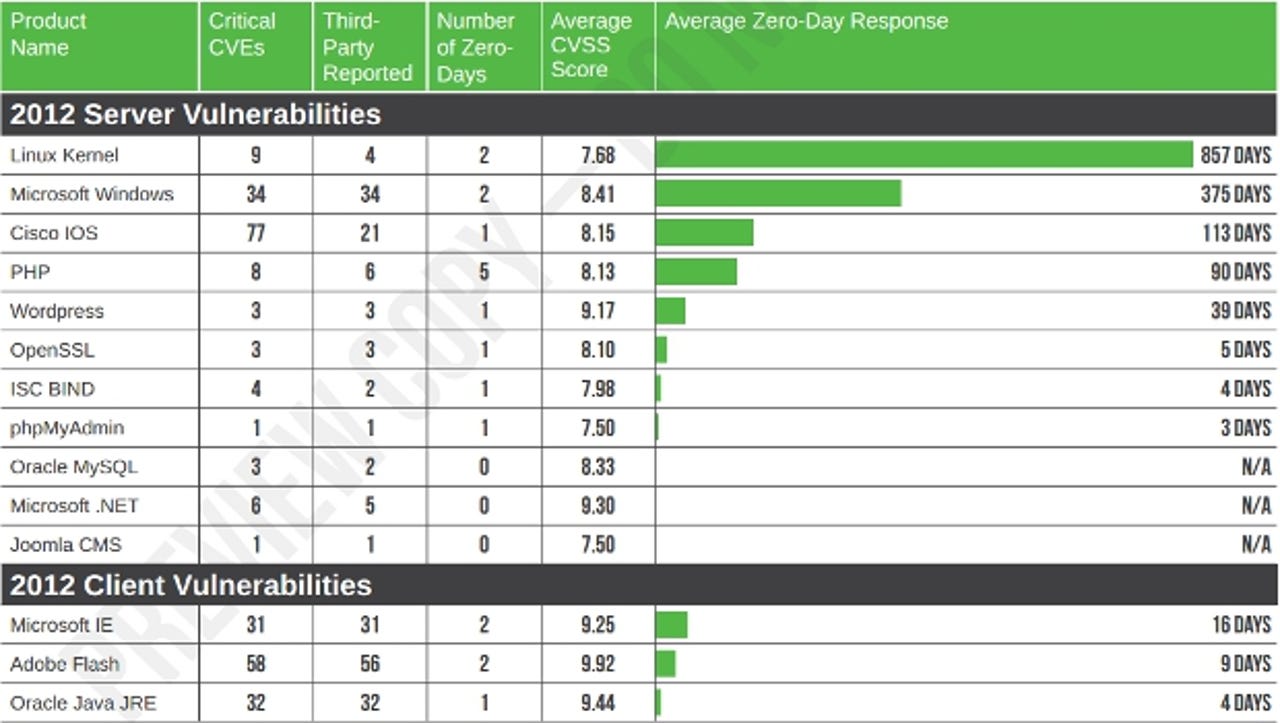
However the data shouldn't be interpreted as a claim that an OS built off the Linux kernel is necessarily less secure than using a Windows OS, as not every distro of Linux would necessarily be affected by every exploit, said Yeo.
"With the Linux kernel some of these CVEs (Common Vulnerabilities and Exposures) won't necessarily apply to one particular distribution," he said.
Matthias Kirschner, fellowship co-ordinator with the Free Software Foundation Europe, said there are many factors that can influence how long it can take to fix a zero day.
"Measuring zero day exploits is a bit difficult. How long did the developers already know about the exploit before it became public? That also influences how long it takes to fix it. If someone knows it before, eg because he implemented the exploit on purpose, it is easier to fix it — the solution might already be waiting for committing," he said.
"Free software can be developed in a very open collaborative development model, as well as it can be developed by one person in secret, without accepting any patches from others. That's why we recommend to differ between the software model, the development model, and the business model."
The zero-day vulnerabilities patched last year that were used to calculate the average time to patching are as follows:
Microsoft Windows
- CVE-2010-5082 detailed by independent researcher on Sept. 14, 2010 and not fixed until February 14, 2012. Affected Microsoft Windows Server 2008 SP2, R2, and R2 SP1.
- CVE-2012-0181 fixes an issue alluded to on exploitdb site on Nov. 21, 2011, fixed July 10, 2012. Affected Microsoft Windows XP SP2 and SP3, Windows Server 2003 SP2, Windows Vista SP2, Windows Server 2008 SP2, R2, and R2 SP1, Windows 7 Gold and SP1.
Linux kernel
- CVE-2012-2100 is a correction to the fix detailed in CVE-2009-4307, which did not fully work on the common x86 platform. Trustwave considered this a zero-day due to availability of exploit information from the time of the original patch.
- CVE-2012-2319 is a follow-up to CVE-2009-4020; issues in the HFS file system were detailed and patched on Dec. 3, 2009, but HFSPlus was left vulnerable until May 4, 2012.
The Trustwave report says the number of critical vulnerabilities, as determined by the Common Vulnerability Scoring System (CVSS) assessment of factors like potential impact and exploitability, identified in the Linux kernel was lower than in Windows last year, with nine in Linux compared to 34 in Windows. The overall seriousness of vulnerabilities was also lower in Linux than Windows, with Linux having an average CVSS score of 7.68 for its vulnerabilities, compared to 8.41 for Microsoft.