Many Apache websites running old, vulnerable software

Very few Apache web servers are running the current, fully-patched version of the software, according to research by Netcraft. Some very popular sites are running very old, vulnerable and unsupported versions.
Netcraft is known most for their continuous surveys of publicly-accessible web servers on the Internet. Apache's share of such servers has been taking a nosedive over the last two years, according to the latest report on that survey, although it still dominates among active sites and the busiest sites, where Apache runs more than 50% of those surveyed.
The latest version of the Apache Stable Release is 2.4.7, released November 25, 2013. Very few sites are running this version. In fact, less than 1 percent of sites are reporting that they run any version in the 2.4 branch, despite Apache urging users to do so. In fact, Apache servers are overwhelmingly running the "Legacy Release," i.e. the 2.2 branch, the latest version of which is 2.2.26, released November 18, 2013.
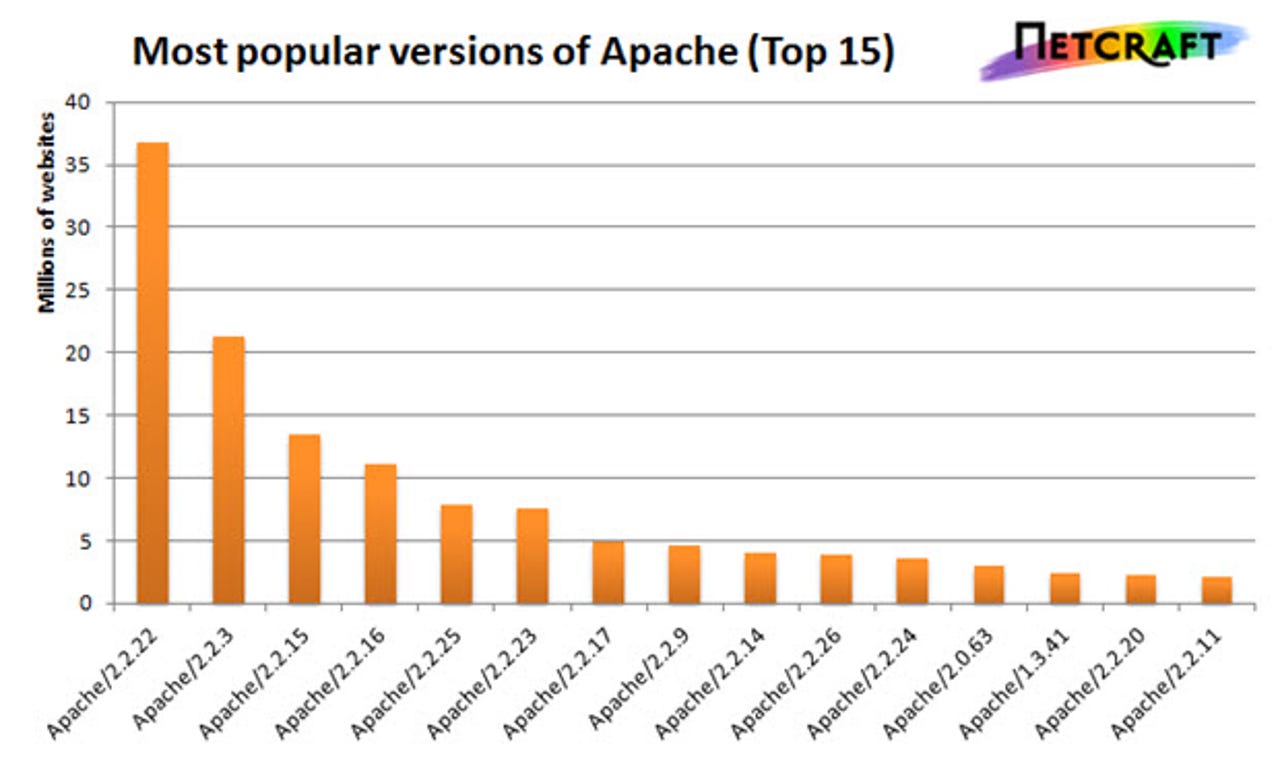
Even version 1.3.x, at roughly 6 million sites, is far more popular than the Stable Release. The most popular such site is Weather Underground, which runs Apache 1.3.42. Weather Underground has an Alexa ranking of 172 in the US and 615 worldwide, so it's a very popular site.
As Netcraft notes, over half of Apache web sites hide the version number, although further tests may indicate the version. By the same token, some servers with a vulnerable version number may not be vulnerable to some of that version's flaws; for example, Red Hat Linux provides a backporting feature by which fixes for later versions may be applied to an earlier version.
But, as best as we can tell, the 2.2.x branch is dominant. It is still distributed by many third parties, such as Red Hat. And many sites for which security is a prominent concern, such as OpenSSL, run old versions. OpenSSL.org runs Apache 2.2.22 on Ubuntu Linux.