Meet Gauss: The latest cyber-espionage tool

Gauss, a new "cyber-espionage toolkit, has emerged in the Middle East and is capable of stealing sensitive data such as browser passwords, online banking accounts, cookies and system configurations, according to Kaspersky Lab. Gauss appears to have come from the same nation-state factories that produced Stuxnet.
According to Kaspersky, Gauss has unique characteristics relative to other malware. Kaspersky said it found Gauss following the discovery of Flame. The International Telecommunications Union has started an effort to identify emerging cyberthreats and mitigate them before they spread.
In a nutshell, Gauss launched around September 2011 and was discovered in June. Gauss, which resembles Flame, had its command and control infrastructure shut down in July, but the malware is dormant waiting for servers to become active. Kaspersky noted in an FAQ:
There is enough evidence that this is closely related to Flame and Stuxnet, which are nation-state sponsored attacks. We have evidence that Gauss was created by the same "factory" (or factories) that produced Stuxnet, Duqu and Flame.
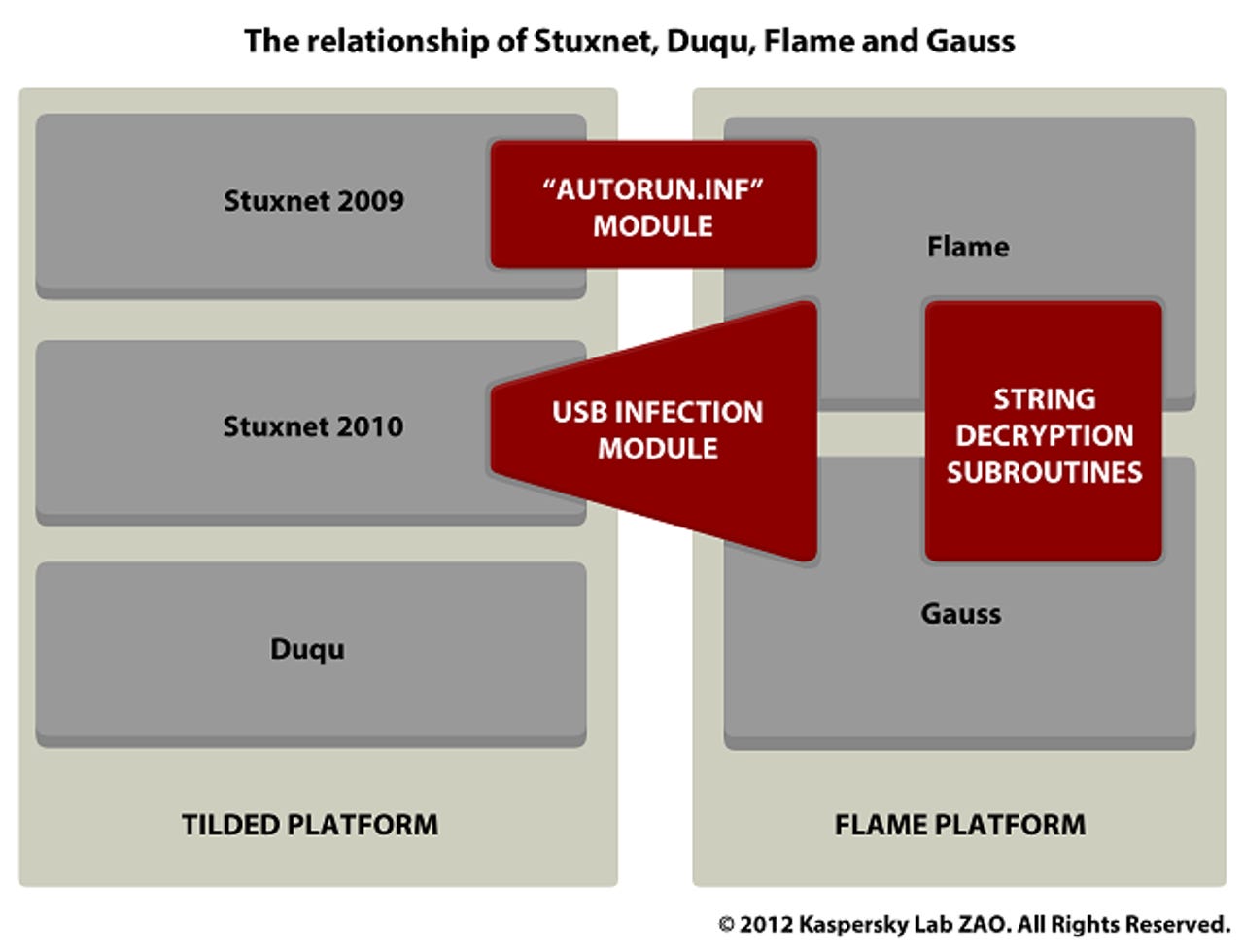
Among Gauss' key features:
- Gauss collects data on machines and sends it to attackers. This data includes network interface information, computer drive details and BIOS characteristics.
- The malware can infect USB thumb drives using the vulnerabilities found in Stuxnet and Flame.
- Gauss can disinfect drives under certain circumstances and then uses removable media to store collected data in a hidden file.
- The malware also installs a special font called Palida Narrow.
Since May 2012, Gauss has infected more than 2,500 machines, mostly in Lebanon. Kaspersky said that the total number of Gauss victims is likely to be in the "tens of thousands." That number is lower than Stuxnet, but higher than Flame and Duqu attacks.
So far, Gauss has swiped data from the Bank of Beirut, EBLF, BlomBank, ByblosBank, FransaBank and Credit Libanais. Citibank and PayPal users are also targeted.
Why Gauss? The malware's main module was named after German mathematician Johann Carl Friedrich Gauss. Other components are also named after well-known mathematicians.
A few key slides from Kaspersky's Gauss report: