One password cracked and your business is history

One thing that always makes me feel a bit uneasy when I blog or tweet is exposing myself to spearphising vectors. One such vector I've mentioned a few times is the fact that I use Google Apps.
One thing that would make a hack attempt more difficult is that I use Google's two-factor authentication. Whenever I log in to the website a one-time code gets texted to my phone. That gives me some comfort at least.
Most people think of their email as the last stop in the security chain. Need to recover a forgotten password for a service? No problem, just get it emailed through. With a nice, tough, two-factor system in place that's a pretty secure setup, right?
Um, no.
Hackery
The problem with that arrangement is, regardless of whatever cloud setup you have, securing the email is too far down your infrastructure chain to protect against someone redirecting your email server somewhere else. "Above" your email server is your domain registrar that points people at your DNS service. The DNS service then points people at your email server.
If a hacker gets into your account at either the registrar or the DNS service level they can redirect your incoming emails from your server and into their server.
Say a hacker suspects or knows that you use a given service and they want to access it. The hacker goes into your registrar account, redirects the email and visits the target service's website. They click "forgot password", guess your username (usually not hard, or they may know it) and the forgot password email goes into their server and not yours. They can then log onto the service at their leisure. They can -- and also should if they're being properly nefarious -- also lock you out.
I'm seeing this as a particular problem for spearphishing attacks rather than general attacks, although it's plausible that you could automate this system.
This problem particular worries me because of this: imagine it's ten years ago and your boss asks you as your IT manager to "get a domain name". You go online to a domain register, and set-up a new account. Ten years ago, was your idea of a strong password the string "p4ssw0rd"? Have you been back and changed it?
Even in the process of writing this article I personally discovered the most important domain I had wasn't with the registrar I thought it was, and that the password to access the account was weak.
I'd be bold enough to say that the majority of readers reading this with a domain aged of around the 2003-era have a weak password on their registrar and are actively at risk from having their domain co-opted using this method.
It doesn't matter if your email server has two-factor security and is hardened to the n-th degree. If someone can just own your domain with a password like "p4ssw0rd" and redirect your mail server, what's the point? I've tried not to say "a chain is only as strong as its weakest link" in this article, but there, I have done now.
This situation is totally ridiculous. Domain name registars are so important in the cloud that without them there would be no cloud, yet they don't behave in the way such companies should. I went onto GoDaddy's website and tried to log into my account with the incorrect password 15 times and it kept letting me try again and again. After five attempts it presented a CAPTCHA test. You would expect any infrastructure service to simply outright lock the account way before that.
Similarly, how many registrars require minimum password strength? Forced password expiration? Two-factor authentication? Very few.
Solving the problem
The first most obvious thing to do is go back to your domain registrar and any DNS services that you use and put strong passwords on. A site I use is www.strongpasswordgenerator.com. This makes it very easy to come up with sufficiently complex passwords. You also need to manually track the need to expire and redo that password periodically, because the registrar likely won't do that for you.
The second thing to do is consider applying two-factor style security further up the chain. However services that do this might be harder to come by.
Twitter friend Luke Carrier suggested Name.com as a registrar that has a two-factor option. I tried their two-factor system and it works as advertised and was very easy to set-up. They use Symantec's VIP access system. This is the classic two-factor approach of having a device that shows a one-time use code that changes every 30 seconds or so. You can either use an app on your phone, or you can buy a physical tag from the company.
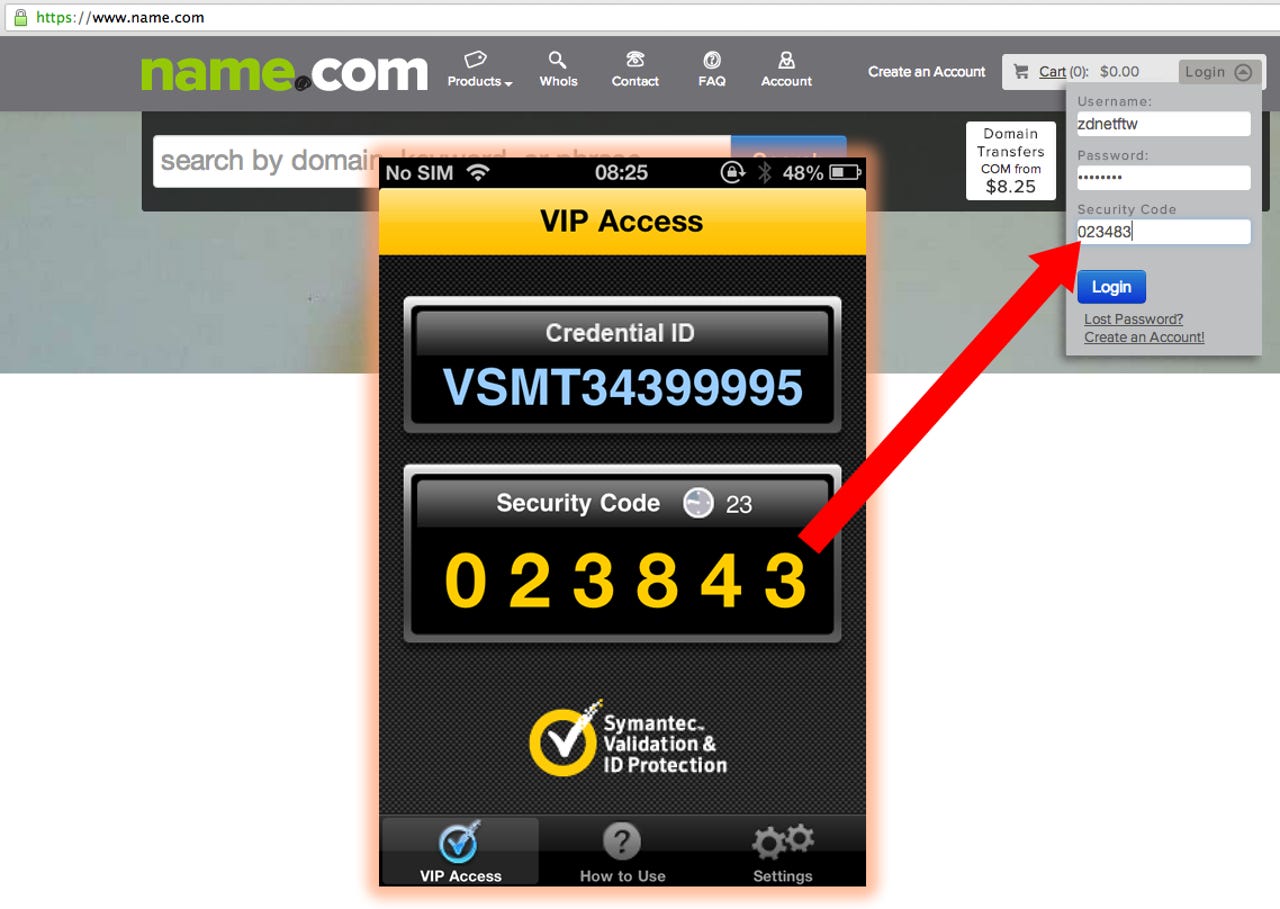
I had a fish around for third-party DNS services that also offer two-factor. I found DNSimple that offers a service through Authly I tried this, and it too works as advertised.
I'm not looking to recommend services in this piece, just raise awareness of the issue. Let me know if you know of any registrar, DNS, or hosting services that use two-factor (comments, contact form, or Twitter), and I'll post a footnote on this article.
However, If I were making recommendations, I would err towards choosing services that were using two-factor systems based on market leaders, such as Symantec and Vasco.
Conclusion
This realisation certainly came as a surprise to me, and the small handful of people I consulted whilst writing this piece did have weak passwords on either their registrar account and/or their DNS service.
Stay safe.
What do you think? Post a comment, or talk to me on Twitter: @mbrit.