Samsung and Google provide more details on Knox contribution to Android L

While the material design features of Android L captured most of the attention at Google I/O, the Samsung contribution of Knox is important to the enterprise audience considering future Android devices. Yesterday, Google and Samsung posted more details on Knox integration coming in Android L.
Internet of Things
Google and Samsung designed enterprise APIs focused on device and data security, support for IT management, and mobile application management. Similar to what we see in BlackBerry 10, data separation is one of the core functions where personal and corporate applications will remain separated.
Through this managed profile, IT administrators will be able to remotely deploy apps focused on the corporation business. Having a smartphone with this type of data and application management, along with some IT control, should help alleviate some of the concerns with BYOD security.
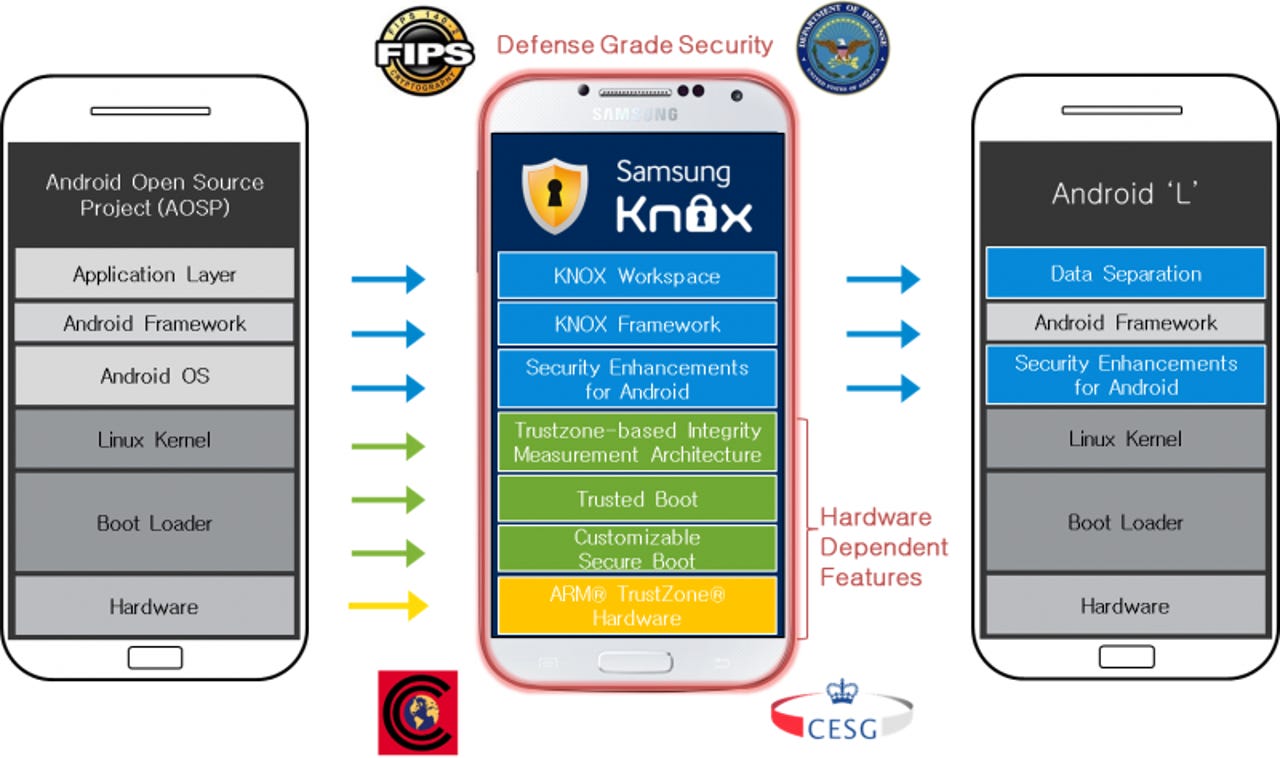
Even though Samsung is sharing many of the Knox functions with Google on Android L, they will still offer a superior security solution on Samsung devices. This is due to several features requiring deep hardware integration that can only be managed directly by Samsung. As listed on the Samsung Knox blog, the following will remain specific to Samsung:
- TrustZone-based Integrity Measurement Architecture (TIMA)
- Real-time Kernel Protection
- Client Certificate Management (CCM)
- Trusted Boot-based Key store
- Remote attestation
- Trusted Boot
- Biometric authentication
- KNOX Smart Card Support
- Government-certified KNOX components
- Common Criteria
- STIG standards (FIPS certified crypto library, FIPS VPN, audit, etc.)
With the continued work on Knox, Samsung is showing that they are serious about security and want to be the provider for businesses looking for secure solutions.