Should security concerns slow BYOD trend? Probably.

Writing a BYOD/Consumerization column doesn't necessarily make me a full-fledged proponent of the practice. My opinion is that you can do anything you want as long as you're willing to accept the risk. That includes snake hunting, parachuting, out-of-bounds skiing and bringing your own device. All have their benefits, all have their risks and all have negative outcomes should something go wrong. And it only has to go slightly wrong for those negative effects to outweigh any possible benefits gained.
Though many would disagree, I don't promote FUD*. I think that for any real progress to be made in the world, you have to have risk takers--those who're willing to do what no one else is. Without those kinds of people, we wouldn't have many of the technological, medical or agricultural advances made in the past 200 years.
Risk taking is part of business. However, you have to temper risk with return. Ask any energized entrepreneur about risk and he'll surely recite the "Without great risks, there are no great rewards" adage. It is true. But we're not talking about blazing new trails here, we're talking about BYOD vs. corporate-owned devices. That's a very different story than one that describes how the world's great business risk takers are also the big success stories.
This is about carrying on business--day-to-day operations, where risk isn't a good thing. Businesses spend billions to install backup systems, RAID arrays, SANs, disaster recovery and every kind of redundance and "airbag" you can think of to lower that daily risk to business operations.
True?
Undeniably true.
Does BYOD add to the risk of those daily operations?
It does.
How you deal with that risk determines how severe those disruptions will be when they happen.
BYOD brings risk because you're allowing user-owned devices within your network. You're allowing users to attach to corporate assets, to access corporate documents and to interact with users inside and outside of your network with those non-corporate owned (controlled) devices.
To allow these devices, you employ a mobile device management (MDM) or mobile application management (MAM) suite to lower your risks. Good job. But that suite is only part of the answer. It won't solve all of the security risks associated with BYOD. For example, it doesn't resolve an mobile OS-related security problems nor does it completely insulate you from malicious, ignorant or stupid users. If you know anything about computer support, people are never guilty of changing anything, installing anything or deleting anything essential to the operation of any computing device in their care.
A good application or device management suite does protect your network from jailbroken devices, from thousands of known malware programs and from standard risks via encrypted connections/communications back to the mother ship (the corporate network).
Your MDM or MAM is a great first line of defense against a lot of threats. But the weak links are still the user and the user's device. A user-owned device is an open door to accidental or intentional security breaches. If you don't believe me, ask any security professional.
To add to the problem is the fact that you don't fully control the user's device. They own it. You might want to control what the user does with it while connecting to your network and accessing your assets but you don't have full control of the device.
Full device control means that you can determine:
- When the device is updated.
- Which Apps the user can download and use.
- Which App providers are allowed.
- The type of device used.
- When to apply App updates.
- Which App versions are allowed.
I think you get the idea that you really don't have control of a user's device nor should you. It's a personal device. For this reason, some companies are using MAM, which fully controls specific corporate-owned applications. Those applications are under full control of the company, including their security, maintenance and life cycle. To remove a user's access, you simple uninstall the App, leaving the device generally untouched.
MAM is a good compromise for most users and companies alike. It allows the user to use their phones and devices freely as their own but also allows for a high level of security within the corporate-owned Apps.
The only flaw that I can see with MAM is that you can't prevent interaction with the underlying operating system. That interaction could compromise an App and, in turn, compromise what's on the other end of the App, which is your corporate network. And no operating system is safe from these threats. Android threats have mushroomed at an alarming rate. See the Kaspersky graphic below depicting the rise in Android threats.
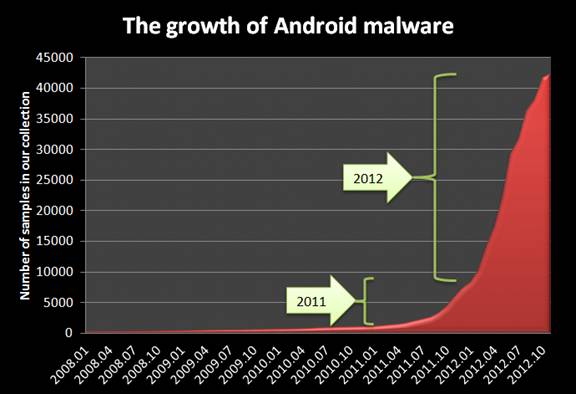
As far as new malware threats and exploits, Android is the new Windows. There was a time when Android and Linux supporters assumed that the operating systems were not vulnerable to such malicious software.
All of this data and opinion boils down to one question for you and your BYOD program: How much risk are you willing to accept? An additional question added by MDM and MAM vendors is, "How will you mitigate that risk?" The answers aren't so easy nor as visually appealing as the threats.
Corporate-owned devices don't guarantee a trouble-free or threat-free environment either. However, the difference is that level of control that I wrote earlier. Corporate-owned devices carry that extreme level of control. The only weak link in the corporate-owned device scenario is that the user is on the other end of the device--a necessary evil.
You can't fully remove all risk because of those end users. You can minimize the risk but you can't get rid of it. Any amount of risk you're willing to accept comes down to the amount of money you're willing to spend to prevent, avert and mitigate.
It seems that the costs are very close for either BYOD or for corporate-owned devices. In other words, few find BYOD a money-saving practice. But the risks and costs associated with those risks might slow your BYOD program's momentum. And it probably should.
What do you think? Do you think that companies should take a second look at the security risks of adopting BYOD programs? Or do you think that this security thing is overblown FUD? Talk back and let me know.
*FUD - Fear, uncertainty and doubt.