USB flash drives masquerading as keyboards mean more BYOD security headaches

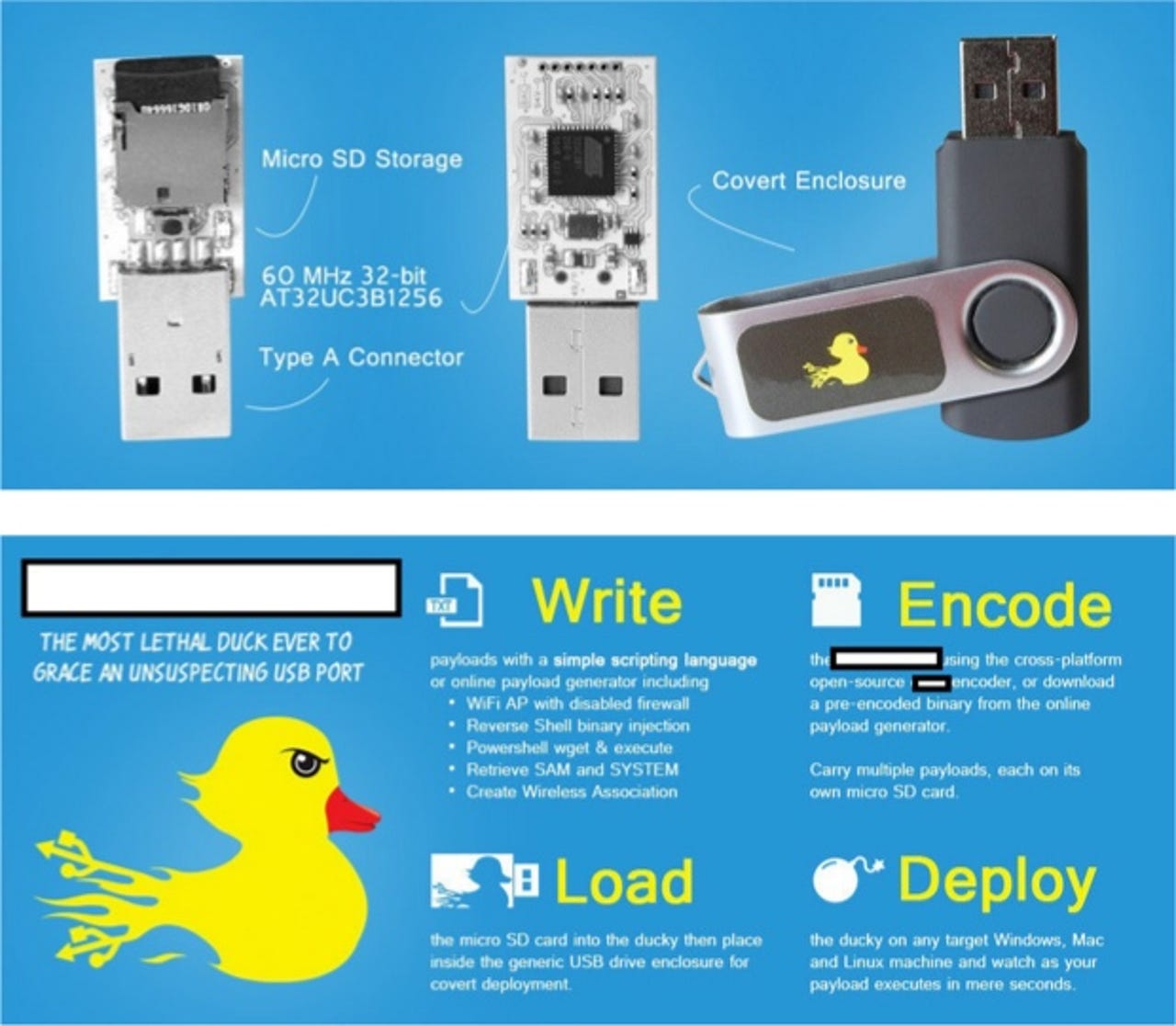
You should be already aware of the data theft risks that USB flash drives pose to your company – even a seemingly lowly 2GB drive can hold a lot of precious data – but a new threat has emerged which makes them even more dangerous.
Writing on the Webroot blog, security expert Dancho Danchev highlights the dangers facing corporations, both small and large, from low-cost USB flash drives that are capable of bypassing Microsoft's AutoRun protection measures present on Windows 7 and Windows 8.
The flash drives get around Microsoft's security mechanisms by tricking the operating system into thinking that the memory stick is not a memory stick but instead a 'Human Interface Device,' such as a keyboard.
Within 50 seconds of first plugging one of these devices into a PC, the malicious scripts or files contained on it will be run and the system is compromised. This load time is cut down substantially on subsequent mountings of the device. Without a physical inspection of the device, it's almost impossible to tell it apart from a benign flash drive.
And the price is cheap, with a modified 128MB USB stick costing $54, and a 8GB version costing only $64.
The barrier to system infiltration is low, you just need to know where to find them (no, I'm not telling you, so don't bother asking).
Think you're safe because you use OS X or Linux? Think again! There are devices being marketed that claim to be able to get infiltrate these operating systems too.
So where does this leave organizations who have adopted BYOD? In a bad place, that's where.
Currently there are no security patches for this problem, and given the low-level nature of the access, it remains to be seen whether this is even possible.
Then there's security software. While endpoint security can go some way to protecting against this sort of threat, this is a new threat and one that current security tools are not ready to deal with.
That leaves physical security. This includes:
- Physically protecting USB ports.
- Strict audit of USB hardware.
- Using tamper-proof USB devices, such as IronKey USB flash drives.
- Confiscation for inspection, and then destruction of unauthorized hardware.
All this might seem extreme, but at present this is all that companies have got to protect themselves against this low-cost, high-risk threat.