What Google does when a government requests your data

It's time to face facts: Google wants your data, but governments around the world want it more.
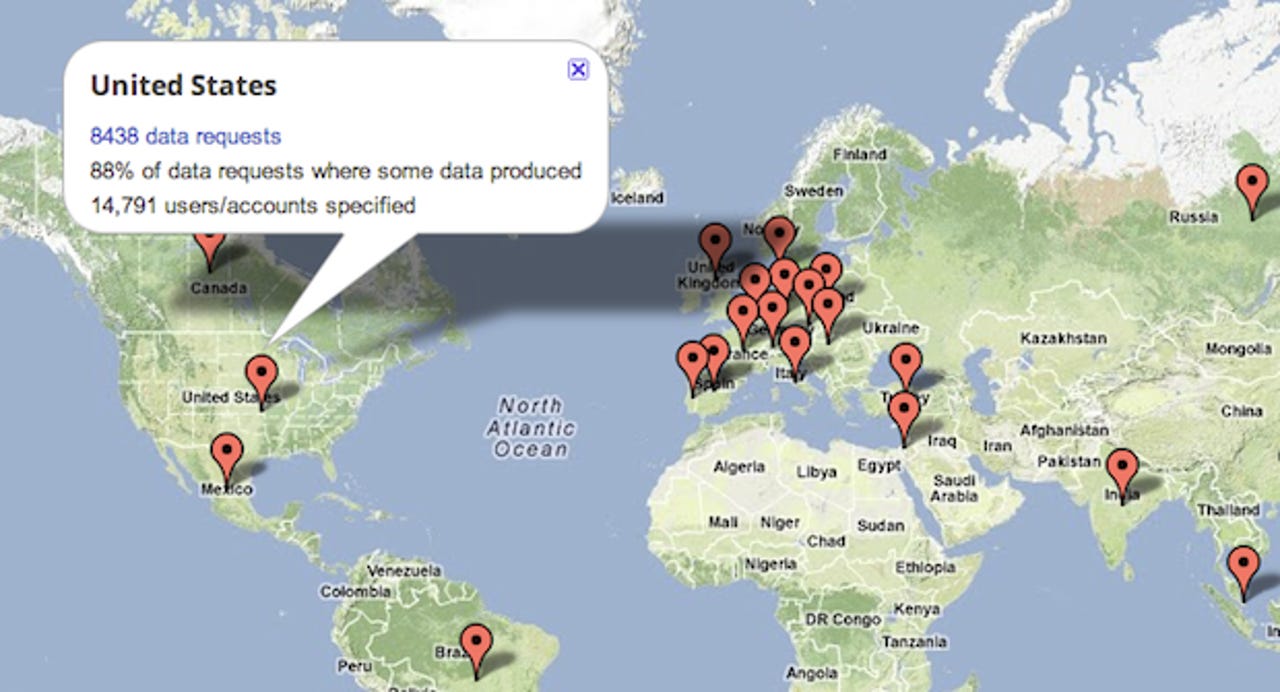
Google has as much, if not more, data on you than your own government does. Google, as a private company with its own interests, is not fully subject to the Fourth Amendment under US law, which guards against "unreasonable searches and seizures." Google is no different than Microsoft, Facebook, Yahoo, Apple, or any other major technology company that makes money from your information.
All of the aforementioned companies are subject to legal requests by US authorities, and other governments around the world. But it is in their own interests to hold onto your data and not turn it over to governments and other authorities--especially those with less-than-respectable track records on user privacy or human rights.
And that's why they sometimes fight.
Today, Google chief legal officer David Drummond took to Google's blog to state exactly that. In a rare move of transparency by a technology company, Drummond also explained the process in which user data is given to governments and law-enforcement agencies--not easily, it turns out, and more often than not with considerable conflict.
"We're a law-abiding company, and we don't want our services to be used in harmful ways," Drummond wrote. "But it's just as important that laws protect you against overly broad requests for your personal information," he added, noting that the company will "continue our long-standing strict process" for handling user data requests.
What does Google do when it receives a request?
In the blog post, Drummond said Google will "scrutinize the request carefully" to ensure that it meets a legal standard and its own internal policies. The request must be generally "made in writing, signed by an authorized official of the requesting agency, and issued under an appropriate law."
An "appropriate law," however, is particularly interesting wording. If Google has a presence in a country where that government is requesting data under the law of that jurisdiction, Google may have to comply; at the very least, it will listen. For instance, if a libel case is brought up from a UK court, Google must honor that request because it has a physical presence in that country.
But legal action in countries such as Zimbabwe, North Korea, or Myanmar (Burma)? It's a little easier for Google to flat-out refuse it.
Google can decide to ask the requesting authority to "narrow the request" if it is overly broad. It can also simply flat-out refuse the request, but this carries legal dangers.
The search giant said that if "your account has been closed," then it can't notify you. However, in some cases, "we sometimes fight to give users notice of a data request by seeking to lift gag orders or unseal search warrants."
Still, in many cases, Google cannot tell a user whose data is being requested that their government or a foreign law-enforcement agency is requesting it. Gag orders are often issued by requesting governments--to avoid legal action by the user in question, or to prevent the data from being deleted, or in cases where a group of people may be under the same or similar requests and the requesting agency don't want others to find out. This tends to occur during sensitive investigations relating to children, fraud, or terrorism.
Google may hand over data on user accounts--which may include IP addresses, metadata, and other personal data--but search queries are a "no," Drummond noted, thanks to a 2006 legal ruling in which the company fought the US Department of Justice over its overly broad request of user data, including search queries.
What kind of data is requested?
Arguably, the most important and privacy-sensitive Google service for customers is Gmail. Google explains that the data it reluctantly gives to requesting authorities differs depending on the type of request it receives.
For instance:
Subpoena:
Subscriber registration information (e.g., name, account creation information, associated email addresses, phone number)
Sign-in IP addresses and associated time stamps
Court order:
Non-content information (such as non-content email header information)
Information obtainable with a subpoena
Search warrant:
Email content
Information obtainable with a subpoena or court order.
Google said it will e-mail users if their data has been requested, so long as a gagging order does not prevent it from doing so. "Just because we receive a request doesn't necessarily mean that we did--or will--disclose any of the requested information," the FAQ said. But, "we can't give you legal advice," Google said, so "you may want to consult a lawyer."
US vs. non-US requests
Because Google is a US-based company, the firm falls squarely under US law, which makes it difficult for it to ignore a request from its home government.
The company explained that under one particular strand of US law, requests for "stored data" can be made, but that requests can also fall under different areas of law--including the Patriot Act, among others. Because Google is effectively a data-storage company, in that it stores your data online so you can access it at any point in any location, most of its requests fall under a specific "stored data" law.
"By far the most common is the subpoena, followed by search warrants. A federal statute called the Electronic Communications Privacy Act," the same law that General David Petraeus was busted for during the "Gmail-affair-gate" controversy, "known as ECPA, regulates how a government agency can use these types of legal process to compel companies like Google to disclose information about users. This law was passed in 1986, before the web as we know it today even existed. It has failed to keep pace with how people use the Internet today."
While ECPA can allow a government agency to compel the disclosure of certain kinds of data with a subpoena or an ECPA court order, "Google requires an ECPA search warrant for contents of Gmail and other services based on the Fourth Amendment to the US Constitution, which prohibits unreasonable search and seizure."
Google works with the Digital Due Process Coalition, a group that "[seeks] updates to this important law so it guarantees the level of privacy that you should reasonably expect when using our services."
EU law makes it difficult--though not impossible--for Google to hand over data to non-EU countries.
If Google was based in the European Union (EU), however, the situation would be slightly difficult. It's not easy for a European-based firm to hand over data to a country's government that doesn't have the same strict data-protection rules as the 27 member-state bloc of the European Union.
However, in some "emergency cases," the search giant will "voluntarily disclose user information to government agencies when we believe that doing so is necessary to prevent death or serious physical harm to someone." If a US or foreign law-enforcement agency tells Google that a case involves "kidnapping or bomb threats," for example, Google said the "law allows us to make these exceptions" and help authorities if the request is valid and an immediate threat to life exists.
How Google responds to foreign, non-US governments
But outside the US, Google doesn't really have the same level of requirement to hand over data to foreign governments or law-enforcement agencies--particularly if Google doesn't have a physical presence in the country of that requesting state.
Mutual Legal Assistance (MLA) allows a government to seek help from a foreign government where that person or company resides, because they have no jurisdictional power.
In this case, it means a foreign government--like the UK, France, or Germany, for example--would have to put in an "MLA request" to the US Department of Justice requesting help. The government agency would then knock on Google's big-data door as it has jurisdictional power.
MLA treaties exist between most countries in the world, but not all. This means it can keep some countries at a distance in order to protect other governments from harming their own citizens, such as in Syria, for example.
"If US law is implicated in the investigation, a US agency may open its own investigation and provide non-US investigators with evidence gathered. Google may also disclose data in response to emergency disclosure requests when we believe that doing so is necessary to prevent death or serious physical harm to someone," the FAQ noted.
If a non-US agency goes through a diplomatic channel such as an MLA request, "Google would produce the same information as if the request originated directly from a US agency."
However, Google will still occasionally hand over data under "emergency requests" to foreign governments on a "voluntary basis." Also, the company may provide user data to foreign, non-US governments if that government's request is "consistent with international norms," which allows Google to flat-out deny countries that may use that data to crack down on dissidents or political activists--ahem, China.
But MLA isn't the only option for foreign governments
"There are many ways that other countries can obtain information from companies like Google outside of the [mutual legal assistance] process, including joint investigations between US and local law enforcement, emergency disclosure requests, and others."
The "others" bit is interesting, however. Some foreign governments have laws that could force Google, and other companies based in the US and around the world, into performing actions in which it must do locally, rather than where it's headquartered in the US. For instance, the UK government could invoke the Terrorism Act or the Regulation of Investigatory Powers Act (RIPA) against Google UK, which could force the UK-based subsidiary into handing over local data, and prevent it from telling its parent company.
It could also work in reverse, with the US government forcing a Google subsidiary in the UK or Europe to hand over data belonging to an EU citizen--in spite of strong European data-protection laws--back to the US without that person's knowledge. But, Google will "sometimes fight to give users notice of a data request by seeking to lift gag orders or unseal search warrants." With some areas of US law, that would still be nigh on impossible.
These cases are hypothetical, but entirely possible--and if they do happen, very rare.
The bottom line
Google has done something extraordinary here. Through leaked documents and law-enforcement guides, it has been previously disclosed how some companies--Facebook comes to mind--deals with requests from law-enforcement agencies.
But it's very rare for a company as large as Google to openly admit that not only does data get requested by governments around the world, but that it actively gives that data away where it is all but forced to by local and international law. Google's pioneered the Transparency Report for many years, whereas Microsoft recently found itself in the firing line over Skype sans transparency.
The move should be applauded. That said, the company can only do so much. It can say "how," but not "why."
Speaking to NPR, Drummond said that Google still can't disclose "whether fraud cases generate more requests than, say, national security." He added: "The problem is, in the vast majority of cases, we don't know. Right? And the government isn't required to tell us what they're investigating."