Whoops: Google indexes more than 86,000 HP 'public' printers

Google has indexed tens of thousands of HP printers, which are publicly available from anyone with an Internet connection, but could also be attacked by hackers with malicious—albeit hilarious—intents.
Granted, the search engine indexed the printers without knowing necessarily what they are or that they're probably meant to be network-internal only. The onus of blame should probably fall on the hapless IT person who set up the printer that way rather on the search engine. (Trying the same result in Bing displays no results at the time of writing.)
If you type in the following on Google:
inurl:hp/device/this.LCDispatcher?nav=hp.Print
The search result lists this:
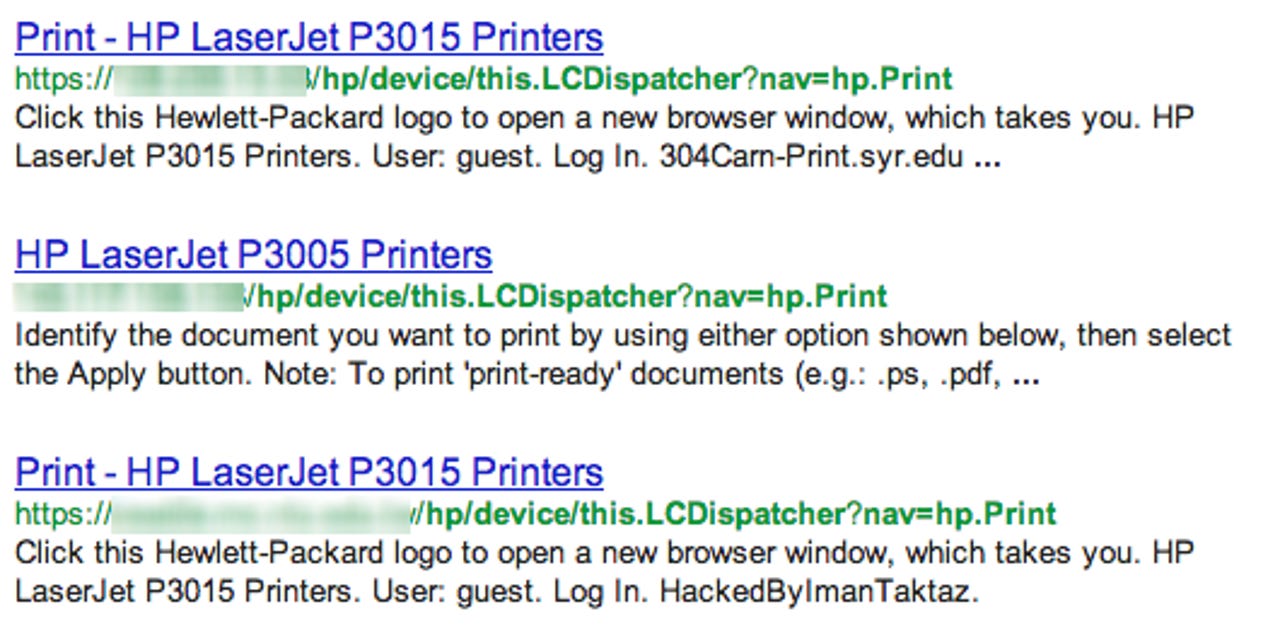
That's just a snapshot of more than 86,000 publicly available HP printers, which can be used by anyone to print their documents. Looking through some of the IP addresses and domain names, these publicly available printers are hosted by dozens of universities, such as the University of Washington, including many outside the United States.
On the face of it, it sounds almost pointless—you won't be there to be able to pick them up—but all it takes is one malicious script written by a clever hacker and you'll be replacing the paper tray every five minutes, and using up the toner supplies faster than you've ever known.
Perhaps more worryingly, many of these printers do not have passwords enabled and can be directly accessed from outside their company's firewall, such as this one—which shall remain nameless and anonymous, for obvious reasons—not least to save this one prominent company from embarrassment.
The best practice here is to set up the printer within the firewall and enable VPN access, so documents and files can be printed remotely but over a secure channel. And, it almost goes without saying: stick a password on there so at least if it is accessible over the Internet it can't be maliciously accessed or screwed around with.