Apple Mac in-app purchases hacked; everything free like on iOS

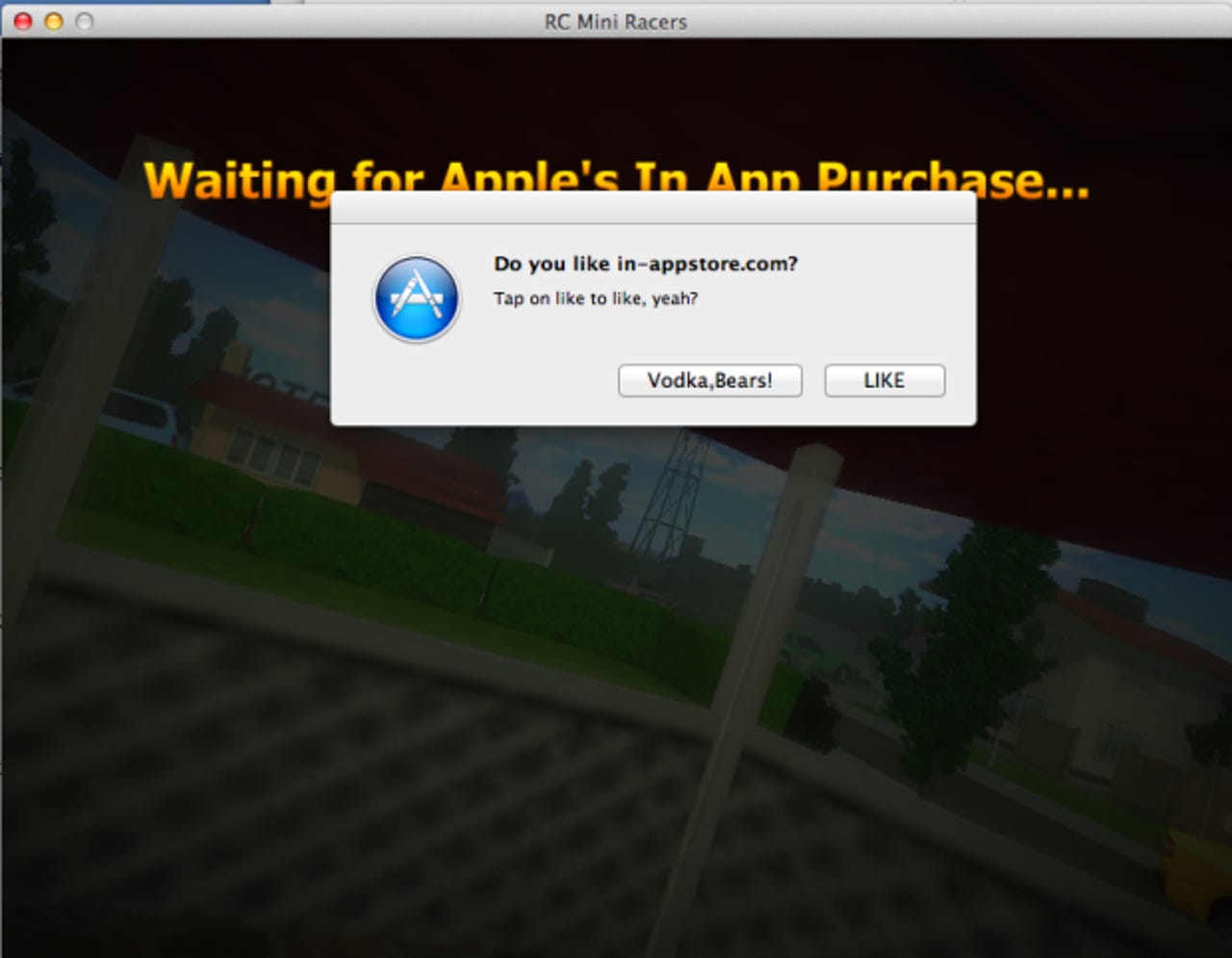
Last week Russian developer Alexey Borodin hacked Apple's In-App Purchase program for all devices running iOS 3.0 or later, allowing iPhone, iPad, and iPod touch users to circumvent the payment process and essentially steal in-app content. Apple today announced a temporary fix and that it would patch the holes with the release of iOS 6. While Cupertino was distracted, Borodin came in and pulled off the same scheme on the Mac.
That's right. Borodin's new hack allows Mac users to circumvent the payment process and essentially steal in-app content, just like his previous one did for iOS. The new "In-Appstore for OS X" service uses a similar method to fake transactions made to Apple's servers, according to "Getting started to receive your in-app for free on OS X."
To use this "trick" yourself, you need to perform the following steps (for the record, I do not recommend doing this, especially given that you have to hand over your login credentials, and I do not condone it either, as it is stealing):
- Install CA certificate and in-appstore.com certificate
- Change DNS record in Wi-Fi settings
- Running Grim Receiper application (to save your original AppStore receipts)
Until Apple stepped in, iOS developers had no way of protecting their apps, and this looks to be the same situation for Mac app developers. Using store receipts doesn't work as Borodin's service simply needed a single donated receipt, which it could then use to authenticate anyone's purchase requests. His circumvention technique relies on installing certificates (for a fake in-app purchase server and a custom DNS server), changing DNS settings to allow the authentication of "purchases," and finally emulating the receipt verification server.
The only difference this time around (apart from the different store), is that Borodin has developed an app called "Grim Receiper." It must be run on the local machine, and as far as I can tell its main purpose is to collect receipts for reuse. "That's the tool to keep your original receipts in safe place (locally, of course) during you are using in-appstore.com," says Borodin.
Affected iOS apps treated Borodin's server as an official communication because of how Apple authenticates a purchase. The same thing goes for Mac apps. The problem is that Apple does not tie a given purchase directly to a customer or device, meaning a single purchased receipt can be used again and again.
It's not yet clear if Cupertino is transmitting its customers' Apple IDs and passwords in clear text just like it was for iOS (Apple assumed it would only ever be communicating with its own server). If so, whoever operates in-appstore.com could easily be gathering everyone's iTunes login credentials (as well as unique device-identifying data) in the same type of man-in-the-middle attack that was used for iOS.
When Apple first tried (and failed) to stop Borodin, the company managed to disable his PayPal account. Borodin started taking donations via BitCoin, and for this Mac app hack he's doing the same: "Help the project by bitcoin 15GCBL7gHbf2p8bapozSrZhNaXdrKUWRFF. Thanks."
The good news this time around, as The Next Web notes, is that in-app purchasing is much more common in iOS apps than it is in Mac apps. Still, hopefully Apple fixes this issue more quickly on the Mac than on iOS. Given that the upcoming OS X 10.8 Mountain Lion is set to be released later this month, Apple could potentially offer a fix for this issue very quickly. Just like on iOS though, developers will have to be given some guidance so they can change the code on their end.
See also:
- Apple iOS in-app purchases hacked; everything is free (video)
- Apple investigating iOS in-app purchase hack
- Apple tries to block iOS in-app purchase hack, fails
- Apple adds unique identifiers to fight iOS in-app purchase hack
- Apple to block in-app purchase hack in iOS 6, offers interim fix
- Cross-platform Trojan attacks Windows, Intel Macs, Linux
- Over 600,000 Macs infected with Flashback Trojan