Wildfire ransomware code cracked: Victims can now unlock encrypted files for free

Wildfire ransomware has plagued victims in The Netherlands and Belgium
Victims of the Wildfire ransomware can get their encrypted files back without paying hackers for the privilege, after the No More Ransom initiative released a free decryption tool.
No More Ransom runs a web portal that provides keys for unlocking files encrypted by various strains of ransomware, including Shade, Coinvault, Rannoh, Rakhn and, most recently, Wildfire.
Aimed at helping ransomware victims retrieve their data, No More Ransom is a collaborative project between Europol, the Dutch National Police, Intel Security, and Kaspersky Lab.
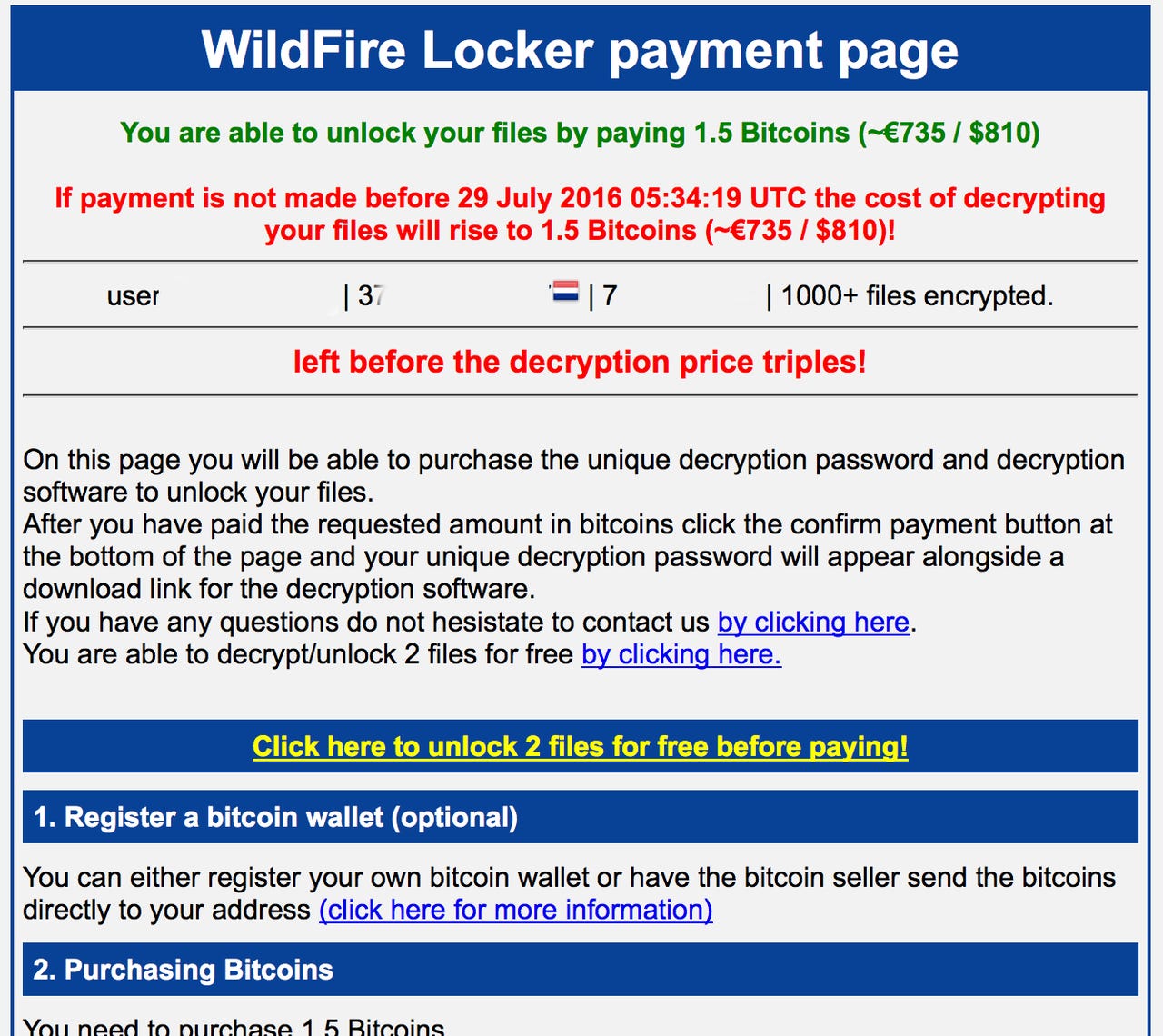
Wildfire victims are served with a ransom note demanding payment of 1.5 Bitcoins -- the cryptocurrency favored by cybercriminals -- in exchange for unlocking the encrypted files. However, cybersecurity researchers from McAfee Labs, part of Intel Security, point out that the hackers behind Wildfire are open to negotiation, often accepting 0.5 Bitcoins as a payment.
Most victims of the ransomware are located in the Netherlands and Belgium, with the malicious software spread through phishing emails aimed at Dutch speakers. The email claims to be from a transport company and suggests that the target has missed a parcel delivery -- encouraging them to fill in a form to rearrange delivery for another date. It's this form which drops Wildfire ransomware onto the victim's system and locks it down.
A spam email used to infect victims with Wildfire.
Researchers note that those behind Wildfire have "clearly put a lot of effort into making their spam mails look credible and very specific" - even adding the addresses of real businesses in The Netherlands - arousing suspicion that there are Dutch speaking actors involved in the ransomware campaign.
Working in partnership with law enforcement agencies, cybersecurity researchers were able to examine Wildfire's control server panel, which showed that in a one month period the ransomware infected 5,309 systems and generated a revenue of 136 Bitcoins (€70,332).
Researchers suggest that the malicious code -- which contains instructions not to infect Russian-speaking countries -- means Wildfire operates as part of a ransomware-as-service franchise, with software likely to be leased out by developers in Eastern Europe.
Whoever is behind Wildfire, victims no longer need to pay a ransom in order to get their files back,with the decryptor tool now available to download for free from the No More Ransom site. The tool contains 1,600 keys for Wildfire, and No More Ransom says more will be added in the near future.
READ MORE ON CYBERCRIME
- Encryption ransomware now 'tried and trusted' attacker business model
- Easy to carry out, difficult to fight against: Why ransomware is booming in 2016
- Pay up or else: Ransomware is the hot hacking trend of 2016 (CNET)
- How to mitigate ransomware, DDoS attacks, and other cyber extortion threats (TechRepublic)