ImageShack hacked by anti-full disclosure movement
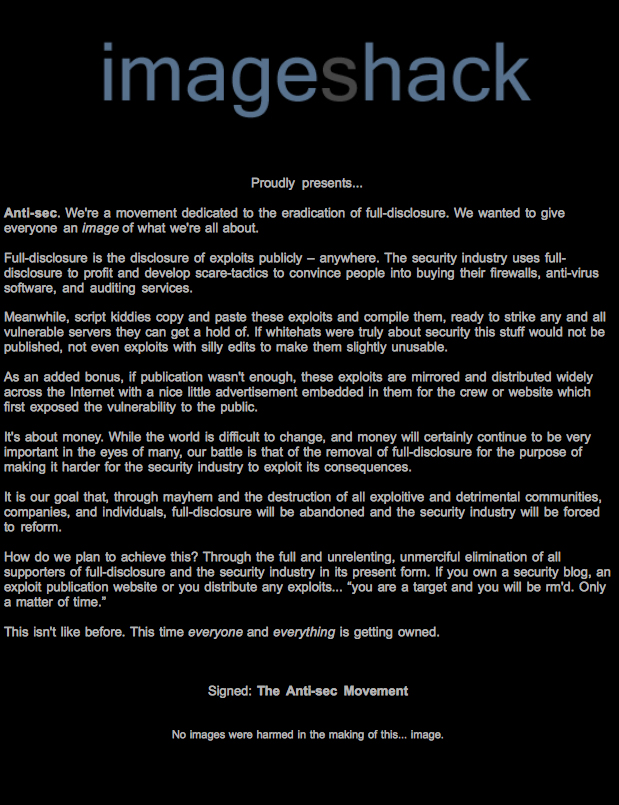
The anti-sec group responsible for the compromise describes itself as a "movement dedicated to the eradication of full-disclosure", has also threatened web sites and communities publishing exploits in a full-disclosure fashion.
The message left in the form of an image reads:
"Full-disclosure is the disclosure of exploits publicly - anywhere. The security industry uses full-disclosure to profit and develop scare-tactics to convince people into buying their firewalls, anti-virus software, and auditing services.
Meanwhile, script kiddies copy and paste these exploits and compile them, ready to strike any and all vulnerable servers they can get a hold of. If whitehats were truly about security this stuff would not be published, not even exploits with silly edits to make them slightly unusable."
Whereas this radical -- and illegal -- approach of spreading a philosophy aims to put the spotlight on the full disclosure debate for yet another time, things have greatly changed during the past couple of years, potentially rendering their efforts pointless, at least from the perspective of using zero day exploits for committing cybercrime. The very notion that the well known exploits-repository web sites are the original point of publication for a particular exploit is naive. Case in point - the recent thought to be "zero day" Video ActiveX Control flaw, has been reported to Microsoft over an year ago, but it became an inseparable part of a Chinese-based malware campaign earlier this month.
Moreover, not only did vulnerability markets and market approaches to software vulnerability disclosure greatly improved, but also, the active OTC (over-the-counter) market for vulnerabilities has once again proved that what's a zero day flaw for some, is last month's zero day used by a particular cybercriminal in targeted malware attacks.
The anti-sec group also makes a statement in respect to the "script kiddies who copy and paste these exploits and compile them, ready to strike any and all vulnerable servers they can get a hold of." Shouldn't this also be the practice of the people responsible for the security of a particular web property as well, and if exploitation is possible, a patch or alternative mitigation strategy applied as soon as possible? Who's to blame in this case, the lack of self-awareness on behalf of the affected sites ending up as the "low hanging fruit", or the site providing the service that inevitably improves the effectiveness of ethical penetration testing tools if used at the first place?
What do you think? Is this one of those black and white situations where full-disclosure should be replaced with responsible disclosure, or is full-disclosure in fact serving the community, especially considering the fact that cybercriminals are efficiently infecting hosts by exploiting already patched and outdated flaws and do not necessarily need a zero day to do so?
Talkback.