Tech
How did OpenSSL's home page get defaced?
They got hacked through the hypervisor, but it's not the hypervisor's fault. Blame their hosting service.

Several days ago, the home page for OpenSSL, the cryptography library used by almost everyone who isn't Microsoft, was hacked and replaced with this:
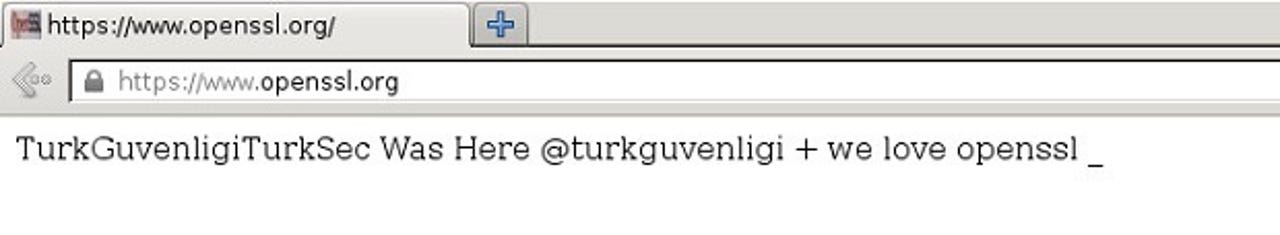
The extent of the attack was just what you see: the home page was defaced. Nothing else on the site was modified. Even so, how could such a security-conscious organization be so victimized?
OpenSSL has done their post-mortem and the report is in:
The OpenSSL server is a virtual server which shares a hypervisor with other customers of the same ISP. Our investigation found that the attack was made through insecure passwords at the hosting provider, leading to control of the hypervisor management console, which then was used to manipulate our virtual server.
Sounds like their hosting provider has reason to be embarrassed. That would be Indit Hosting of Sweden. Just to be clear, in case it's not clear from the description: there was no vulnerability exploited in the attack. Indit Hosting simply didn't follow best practice for passwords.
Does your hosting service use strong passwords? It might be worth asking.