Windows firewall dodged by 'hot-patching' spies using Intel AMT, says Microsoft

Microsoft has demonstrated how hacking group Platinum abuses Intel's AMT Serial-over-LAN for invisible communications.
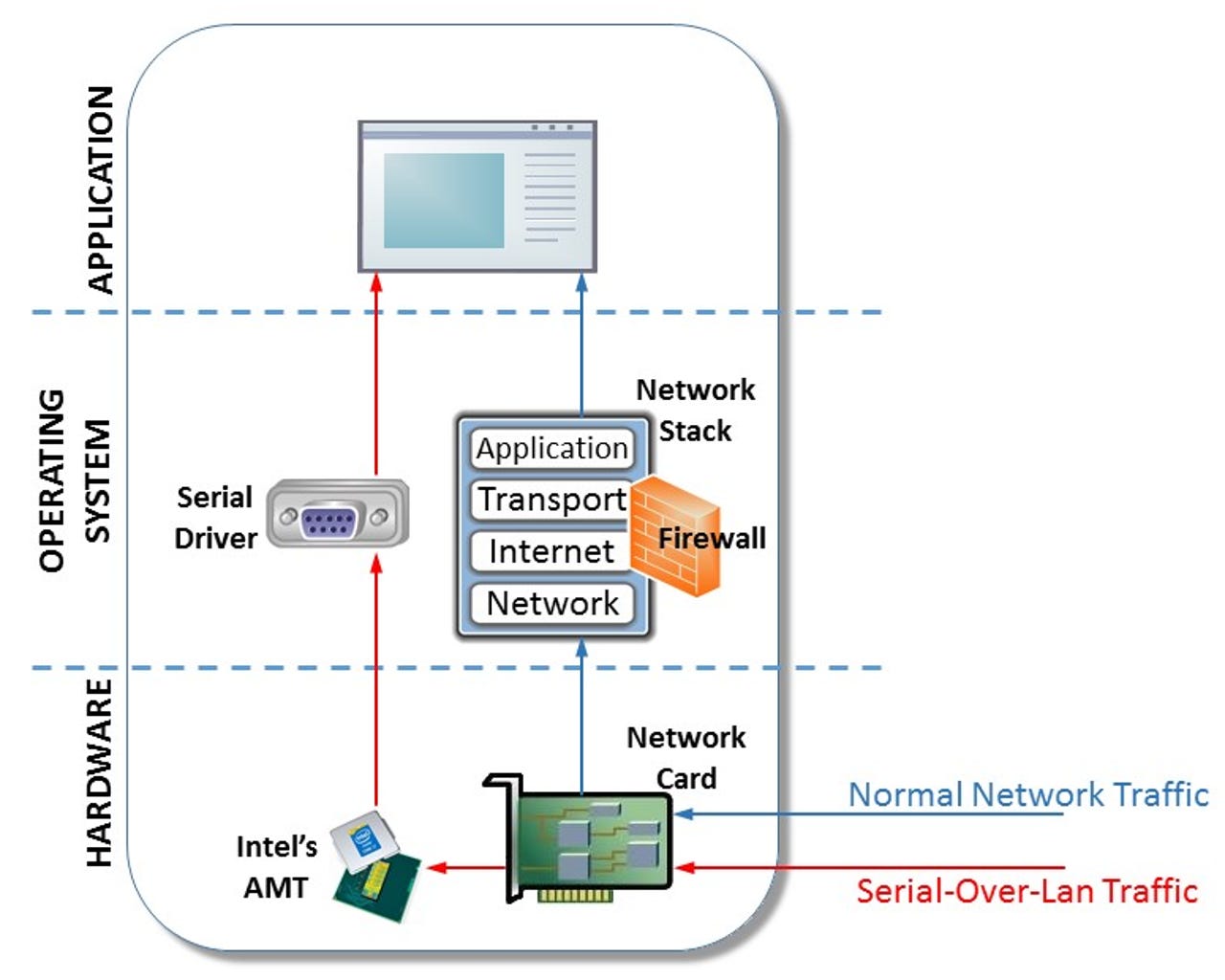
Microsoft has discovered a group of advanced hackers it calls Platinum using Intel's Active Management Technology (AMT) Serial-over-LAN (SOL) to conceal communications from the firewall.
AMT is included in Intel's network chipset to support remote management capabilities. One of its features, AMT-SOL, creates a virtual serial port that can be used to send and receive data from an authenticated management console.
It's a powerful tool that can, for example, be used to scroll the mouse or navigate Windows even when a PC's network drivers are disabled, so long as the device is still physically connected to the network.
Microsoft's malware researchers found that Platinum recently adopted AMT-SOL as part of a file-transfer tool to make its communications "invisible" to a host's firewall and network monitoring applications.
As Microsoft explains, the malware abuses AMT Serial-over-LAN's method of communicating with the management console. Instead of communications passing through the host's networking stack, where a firewall could block this traffic, SOL traffic is diverted to the AMT chipset and virtual serial driver.
Intel and Microsoft confirmed the malware doesn't exploit a vulnerability in AMT SOL, but rather it misuses the feature within already compromised networks. The feature also requires the attacker to already have administrative privileges on targeted systems.
It's the first time Microsoft has observed any hackers using AMT SOL in this way and it's only been observed on a handful of computers.
The sparing use of this malware is consistent with Platinum's advanced attacker profile. The group has been in action at least 2009, and typically spearphishes targets, which have mostly been ISPs, government agencies and defense organizations in southeast Asia.
The group has used 'hot patching', or patching actively running processes, to cloak custom backdoors already planted in PCs. They also have a number of keyloggers and data stealers in their toolkit and have used several zero-day exploits against targets.
Microsoft notes that SOL functionality requires that AMT has been provisioned on a device, while a SOL session also requires a username and password.
So, either Platinum has already acquired these credentials to start a session, or Platinum itself provisioned AMT on targeted systems after gaining administrative privileges for that system and using host-based provisioning.
"The most straightforward is host-based provisioning (HBP), which can be done from within the host Windows OS itself and requires administrator permissions. During the provisioning process, Platinum could select whichever username and password they wish," Microsoft notes.
Linux machines with Intel's chips may also be exposed to this malware. Microsoft notes the technique used by Platinum is OS independent. Microsoft's Windows Defender ATP can alert networks admins to malicious attempts at using AMT SOL but only for Windows PCs.
More on Microsoft and Windows security
- Blue screen of death saved Windows XP from WannaCry ransomware, say security researchers
- Despite security risks, older Windows versions plague thousands of businesses
- Apple, Windows tech support scams: US cracks down on fake security alerts
- Microsoft finally fixes 'critical' Windows security flaw after patch delay
- A simple file naming bug can crash Windows 8.1 and earlier
- CIA's Windows XP to Windows 10 malware: WikiLeaks reveals Athena