Android and Facebook attract more malware attacks

Android smartphones and Facebook are attracting more attention from malware writers, according to the AVG Community Powered Threat Report Q1 2011, which is a sort of "online neighborhood watch". In the PC market, there has been "an explosion in Blackhole Exploit Kits", which are mainly used to attack sercurity flaws in Oracle's Java and Adobe Reader.
The AVG Community Powered Threat Report for 2011's first quarter says the biggest increase has been in what it calls Facebook PUS (Potentially Unwanted Sites). These typically use links to videos with a titles like "OMG, you won’t believe what this teen did on camera". They lure people into filling in surveys and at worst can lead to $9.95 per month being billed to their mobile phone accounts. The report says they use click-jacking (a transparent GIF overlaid over the top of a button) to dupe victims into telling their Facebook friends that they "like" this video, and that they should try it.
Android malware is also soaring, according to the report.
"As our experience tells us, hackers will be where people are, and as more and more people are purchasing an Android powered smart phone, it is not surprising to find the number of malware soaring in geographic where Android takes market share. The open source nature of the OS as well as the open-garden approach in allowing users to install software on the mobile device open the door for hackers to write their malicious code. The fragmentation of the Android platform means that, even if Google fixes a vulnerability, not all users can or will update their OS."
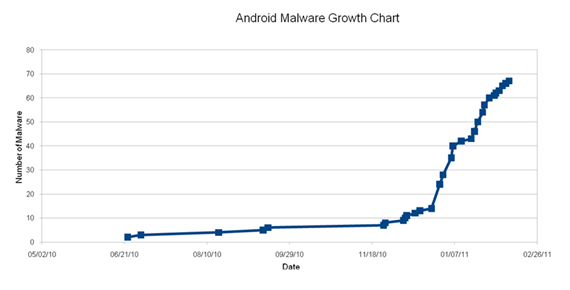
Later, the report says:
"Smart Phone and Android in particular, pose a great risk for users, since mobile devices are constantly connected and substantially less protected than a personal computer as users shrug off mobile security solutions and carelessly broadcast financial, account and other personal data such as their exact location while on the go. Smart Phones and Tablets are typically not equipped with the same security measures as PC & laptops."
AVG has a particular interest in this because it markets software for Android smartphones, as well as anti-virus programs for PCs.
In the PC market, the relatively new Blackhole Exploit Kit was by far the "top toolkit" (86.68 percent) and accounted for 44.20 percent of web threats. In February, more than 600 servers, mostly based in Latvia, were used in a UK-oriented attack that "peaked at a massive 800k detections per day".
A separate account of this Blackhole attack (PDF) attempts to exploit flaws in Microsoft Help Center (CVE-2010-1885), MDAC (CVE-2006-0003), five flaws in Java, and two buffer overflows in Adobe Reader. Java flaws may also affect other operating systems, and the Blackhole admin panel claims 32,826 hits and 14 "loads" on Mac OS X. This compares with 238,699 hits and 16,000 loads on Windows XP, so it's not a big deal, but indicates that "the kit developers are at least thinking about Apple", the report says.
Blackhole may be used to launch a screen that pretends to find malware and promotes rogue spyware or a fake anti-virus product such as AntiMalware GO. Users are then asked to pay $49.95 to $69.95 for a product that will "remove" their PC's non-existent malware. As AVG points out, if you launch 900,000 attacks with a 1% success rate, you can make $450,000 per day.
Blackhole (44.20 percent), rogue scanners (28.61 percent) and rogue spyware scanners (2.76 percent) accounted for the majority of the Top 10 Web Threats in the first quarter, on AVG's numbers.
About 99% of the Windows PCs monitored by Microsoft -- those that have Windows Update turned on and therefore run the Malicious Software Removal Tool every month -- are basically malware free. Running free anti-malware software and Secunia's free Personal Software Inspector -- which checks for patched flaws in insecure third-party software such as Java, Adobe Reader, Apple iTunes and Safari etc -- greatly reduces the risk. Running a recent version of IE, or using the sandboxed and more secure Google Chrome, reduces the risk even further.
The success of Blackhole implies that a lot of people don't bother to install security patches -- MDAC is more than four years old -- and/or are too naïve to cope with the "social engineering" element used to exploit security flaws that require their active co-operation. Fortunately, I didn't see Blackhole, having uninstalled Java some years ago, after an earlier attack, as well as all of Apple's software. I also replaced Adobe Reader with Foxit, which could well be vulnerable to some of the same attacks, but I've yet to experience any.