Apple to patch JailbreakMe.com flaw this week

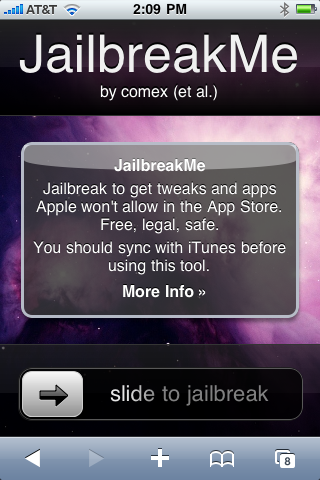
The patch will be distributed via Apple's software update mechanism and will be available for iPhone, iPad and iPod Touch devices.
The exploit, which combines a bug in the way Apple's mobile operating system processes CFF fonts with a privilege escalation vulnerability to escape the sandbox, allows the automated jailbreaking of iPhone/iPad/iPod Touch devices from a specially created Web site.
As the image above shows, a device simply needs to use MobileSafari to surf to a Web site, then push the slider to the right to begin the jailbreaking/expoitation process.
Now that the information on the security hole is publicly available, there is a strong likelihood of malicious copycat attacks.
Here's the skinny on the CFF font vulnerability, via the U.S. Computer Emergency Response Team:
FreeType is a font engine that can open and process font files. FreeType 2 includes the ability to handle a number of font types, including Compact Font Format (CFF). FreeType is used by a number of applications, including PDF readers, web browsers, and other applications. FreeType 2 contains a flaw in the handling of some CFF opcodes, which can result in stack corruption. This can allow arbitrary code execution.
By causing an application that uses FreeType to parse a specially-crafted CFF font, a remote, unauthenticated attacker may be able to execute arbitrary code on a vulnerable system. This can occur as the result of opening a PDF document or viewing a web page.
Apple's security team has been scrambling to figure out the issue and come up with a fix and I'm told the patch is on schedule for release this week.