Backdooring Windows Media files (and assorted Microsoft security problems)

Petko D. Petkov's ongoing research into malicious rigging of media files is now taking aim at Microsoft's ubiquitous Windows Media Player (WMP) software.
The latest discovery revolves around manipulating ".asx" files to display a Web page within the standalone media player.
[The] page will be opened within the Media Player surroundings, not a standalone browser. This in particular is very interesting behavior, which I experimented with for a bit. I found that a fully patched windows XP SP2 with IE6 or IE7 and Windows Media Player 9 (default) will open any page of your choice in less restrictive Internet Explorer environment even if your default browser is Firefox, Opera or anything else you have in place. Let me translate this for you. It means that even if you are running Firefox and you think that you are secure, by simply opening a media file, you expose yourself to all IE vulnerabilities there might be.
On my Windows XP SP2 box with WMP 11, Petkov's proof-of-concept exploits triggered a warning dialog:
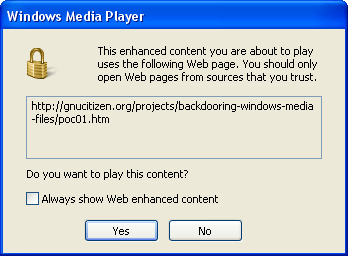
Clicking 'Yes' launches the media player with the attacker's Web page displayed in the "now playing" window:
In addition to Petkov's disclosure, there are several Microsoft product vulnerabilities that remain unpatched.
These include:
- A "moderately critical" vulnerability in the MFC42 and MFC71 libraries offered natively in Windows. The flaw (technical details here) is caused due to a boundary error in the "FindFile()" function of the CFileFind class in mfc42.dll and mfc42u.dll. This can be exploited to cause a heap-based buffer overflow by passing an overly long argument to the affected function. Successful exploitation may allow execution of arbitrary code. The vulnerability is confirmed on a fully-patched Windows XP SP2 including mfc42.dll version 6.2.4131.0 and mfc42u.dll version 6.2.8071.0.
- Multiple "highly critical" vulnerabilities in Microsoft Visual Studio. These can can be exploited by malicious people to overwrite arbitrary files or potentially compromise a vulnerable system. Proof-of-concept exploits are publicly available.