Breach at Macquarie Uni, hackers claim 1 million plain text passwords exposed

Macquarie University has had one of its sites breached and defaced over the weekend in an apparent show to demonstrate that its servers' security are not being maintained to a sufficient standard.
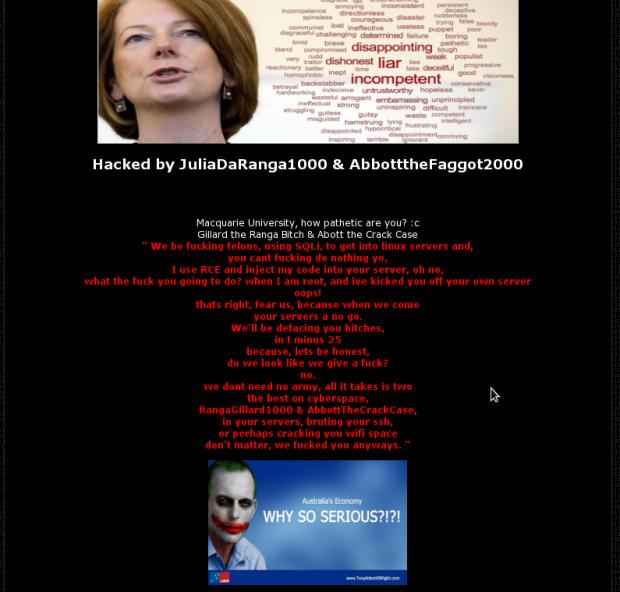
On Friday, one of Macquarie University's web applications, designed to assist international students in applying to study, was breached and defaced by two hackers going by the names of "JuliaDaRanga1000" and "AbbotttheFaggot2000." The defacement makes a number of disparaging remarks about the university's security, mocking what they call a complete lack of security.
"Macquarie University, let me ask you this, who the f*** do you hire for security? Oh, wait, there is none," the two hackers wrote on the site.
"When your administration panel is accessible publicly, what do you think will happen? Once again, as I said, anyone could have done it. It just took some investigating. Don't dub me as an elite hacker, because I simply am not.
"Oh well, you make mistakes, you suffer, you learn. That's how it is for everyone, and your day has come.
"PS Your Oracle database was a piece of s***."
Below that, the hackers dumped the names of the tables in its database. Some of the named tables include TBLAPPLICANTCOREDETAILS_AUD and TBLACADEMICRECORDS_AUD, presumably the details of applicants and academic records.
The hackers focused on one table in particular, named TBLUSER, dumping the first row of data to reveal what fields were available. These included fields that appeared to be for each user's first and last name, email address, and password.
The hackers also uploaded a ColdFusion page that was intended to allow anyone to issue their own SQL statements to interrogate the database at will, and verify for themselves that it was vulnerable, and that user passwords were being stored in plain text. An earlier count of the number of entries in the table shows that if the hackers are to be believed, just over 1 million records were present, dating back to roughly 2007.
ZDNet was unable to confirm what code was used to provide access to the database, but the filename matches a known backdoor that forms part of the fuzzdb project that has the same aim of opening databases to web access. This backdoor only works on ColdFusion 8 and below or unpatched versions of ColdFusion.
Macquarie University told ZDNet that its exposure was limited only to 2600 accounts and that for these, the passwords were encrypted. The university claims that the 1 million records the hackers referred to were not related to the university. It declined to further comment on what those accounts were for or the specifics of the vulnerabilities exploited.
Although the page allowing direct access to the database was removed over the weekend, the defaced site remained up until Monday morning. It is not known who removed the page.
While the hackers' motives remain unknown, one of them claims to have attempted to warn the university of its security issues two years ago.
"I came to your uni. I asked, 'hey guys, do you have anyone monitoring security?' 'are you guys sure that you are secure?'; you neglected me. Shouldn't have. I tried to tell you, you ignored me. F*** you. Trust me; this only took me 20 minutes."
Although the site has been taken offline, Zone-H has since mirrored its defaced state, and Google's listing of the site on its search engine shows some of the defacement text at the time of writing.
A spokesperson for Macquarie University told ZDNet that the site has only been operational for a few weeks, and that it had engaged a third party to host and maintain it offsite on the university's behalf.
"This provider contacted us at 6 a.m. this morning (Monday, December 3) to advise that both site and database appeared to have been compromised; that they had brought the both down immediately, and had commenced an investigation into what had occurred."
The spokesperson also said that the system is isolated, and that no other Macquarie University systems were affected.
"The third-party provider is currently of the view that the system may have been breached via an administrative URL not being correctly secured, and that this probably occurred no earlier than Monday, November 26."
The university is now conducting its own independent investigation, stating that it will "draw on all resources at its disposal to ensure the integrity of its information and that of its community."
In the meantime, the application will remain down until it is confident that the vulnerability has been isolated.
The university has declined to comment on whether it will inform or involve the NSW Privacy Commissioner regarding the breach, however the NSW Privacy Commissioner's office has informed ZDNet that it has received no official notice from the university as of this morning.
Due to the lack of breach notification laws, as well as the uncertainty of whether the leaked information could be used to personally identify an individual, the university is not required by law to report the breach. It is, however, a practice highly encouraged by state and federal privacy commissioners.
Updated at 9.49am: added comment from the NSW Privacy Commissioner.
Updated at 12.18pm: added further comment from Macquarie University.