Fast-Fluxing SQL injection attacks executed from the Asprox botnet
The botnet masters behind the Asprox botnet have recently started SQL injecting fast-fluxed malicious domains in order to enjoy a decent tactical advantage in an attempt to increase the survivability of the malicious campaign. I first assessed the Asprox botnet in January, and again in April when it started scaling and diversifying its campaigns from fake Windows updates, to fake Yahoo ecards, as well as executable news items. A botnet crunching out phishing emails and spam as usual? Depends on the momentum. Automating the process of SQL injecting a large number of sites is one thing, SQL injecting fast-fluxed domains is entirely another. Secureworks comments on the introduction of the SQL injection tool within the botnet :
"As of yesterday, we observed the Asprox botnet pushing an update to the infected systems, a binary with the filename msscntr32.exe. The executable is installed as a system service with the name "Microsoft Security Center Extension", but in reality it is a SQL-injection attack tool. When launched, the attack tool will search Google for .asp pages which contain various terms, and will then launch SQL injection attacks against the websites returned by the search. The attack is designed to inject an iframe into the website source which will force visitors to download a javascript file from the domain direct84.com. This file in turn redirects to another site, where additional malicious javascript can be found. Currently the secondary site appears to be down, however it is likely that when successful, the site attempts to exploit the visitor's web browser in order to install additional copies of either Danmec, Asprox and/or the SQL attack tool."
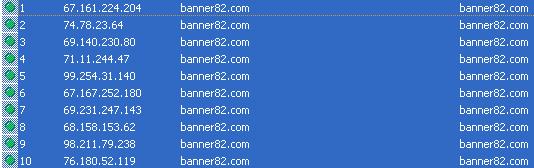
Now comes the fast-flux. The latest massive SQL injection attack courtesy of the Asprox botnet, is this time using the banner82 .com domain which continues to be in a fast-flux mode, namely, it's simultaneously hosted at ten different malware infected IPs, with the IPs constantly changing. Let's illustrate this by taking a look at the changing IPs responding to the same domain within a period of 24 hours :
Fast-flux has been extensively researched by the Honeynet Project, whose research into the topic greatly illustrates single and double-fluxed networks, with the Storm Worm acting as a personal benchmark for the true dynamic nature of fast-flux networks. Fast-flux was embraced by the malicious parties around the middle of 2007, when managed fast-flux providers appeared, and more spam and phishing domains were set in a fast-flux mode. Fast-fluxing SQL injected domains is, however, a new tactic, so you have a botnet of infected hosts that automatically scan and inject malicious domains within vulnerable sites, and the malicious domains themselves part of a fast-flux network provided by the botnet's infected population, that are also hosting and sending the phishing campaigns.
What is the objective of the latest SQL injection attack launched by the Asprox botnet? It's infecting new hosts to be added to the botnet. Banner82 .com has a tiny iFrame that's attempting to load dll64 .com /cgi-bin/index.cgi?admin where the NeoSploit malware exploitation kit is serving MDAC ActiveX code execution (CVE-2006-0003) exploit.
Here are sample fast-fluxing DNS servers used by banner82 .com, as well as a sample internal fast-flux structure used by the botnet:
exportpe .net ns1.exportpe .net ns2.exportpe .net ns3.exportpe .net ns4.exportpe .net ns5.exportpe .net ns6.exportpe .net ns7.exportpe .net ns8.exportpe .net
cookie68 .com ns1.cookie68 .com ns3.cookie68 .com ns4.cookie68 .com ns4.cookie68 .com ns6.cookie68 .com ns7.cookie68 .com ns8.cookie68 .com
ns1.ns2.ns4.ns1.ns7.ns8.ns1.ns4.ns6.ns3 .aspx88.com ns1.ns2.ns4.ns6.ns7.ns7.ns3.ns2.ns5.ns1 .aspx88.com ns1.ns2.ns5.ns1.ns7.ns8.ns2.ns5.ns4.ns3 .aspx88.com ns1.ns1.ns5.ns2.ns7.ns8.ns1 .bank11.net ns1.ns1.ns5.ns2.ns8.ns7.ns4 .bank11.net
The screenshots speak for themselves, and for the infrastructure they've managed to build using the malware infected hosts to send scams, host the scam domains, infect new hosts, scan for vulnerable sites, SQL inject them and host the live exploit URls within. And with the introduction of fast-flux whose infrastructure is provided by the botnet's infected population, and automating the SQL injection process, the Asprox botnet is slowly turning into a self-sustaining cybercrime platform.
Go through a related assessment if you're interested in knowing more about the geographic locations of the infected hosts used in a sample SQL injection attacks, as well as related comments on the use of botnets to launch SQL injection attacks.