FireEye, Kaspersky hit with zero-day flaw claims

Researchers have revealed the existence of zero-day vulnerabilities within Kaspersky and FireEye's systems which could compromise customer safety.
Over the holiday weekend, security researcher Tavis Ormandy disclosed the existence of a vulnerability which impacts on Kaspersky products. Ormandy, known in the past for publicly revealing security flaws in Sophos and ESET antivirus products, said the vulnerability is "about as bad as it gets." In a tweet, the researcher said:
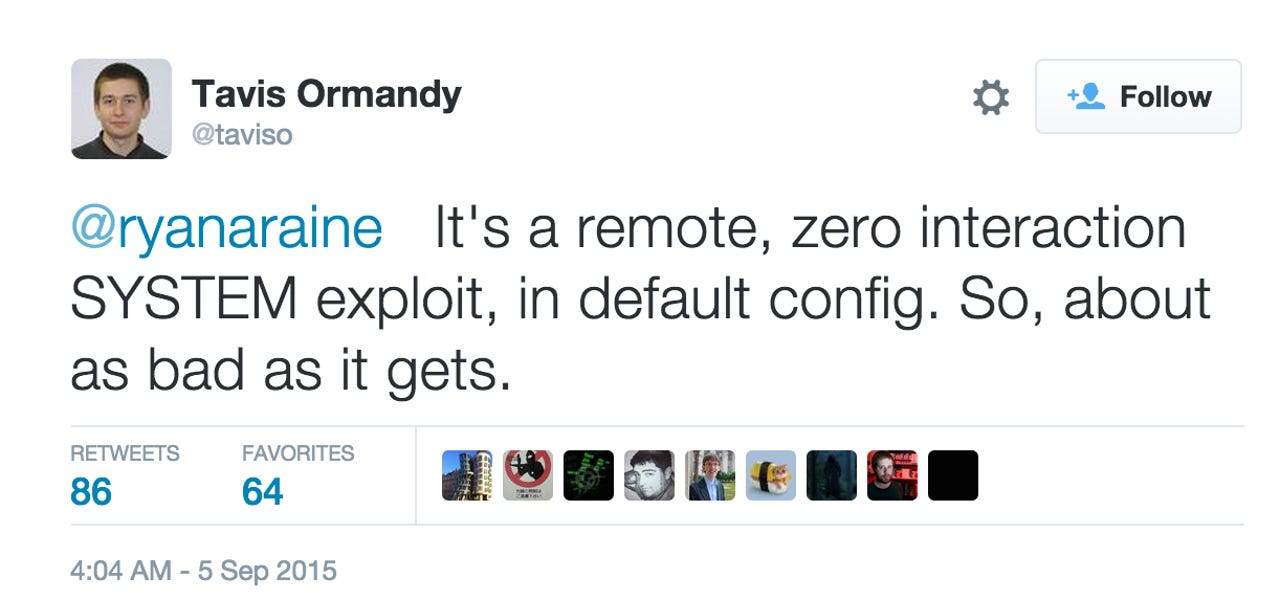
Following the disclosure of the bug, Kaspersky rolled out a global fix in less than 24 hours. As a reward of sorts, Ormandy sent the company a number of other vulnerabilities to investigate, which he termed "obviously exploitable."
In a statement, Kaspersky said:
"We would like to thank Mr. Tavis Ormandy for reporting to us a buffer overflow vulnerability, which our specialists fixed within 24 hours of its disclosure. A fix has already been distributed via automatic updates to all our clients and customers."
Featured
Ormandy's disclosures were made at the same time another researcher's findings, Kristian Erik Hermansen, were posted online. Hermansen publicly disclosed a zero-day vulnerability within cyberforensics firm FireEye's security product, complete with proof-of-concept code.
Within the disclosure, Hermansen said:
"Just one of many handfuls of FireEye / Mandiant 0day. Been sitting on this for more than 18 months with no fix from those security "experts" at FireEye.
Pretty sure Mandiant staff coded this and other bugs into the products. Even more sad, FireEye has no external security researcher reporting process.
FireEye appliance, unauthorized remote root file system access. Oh cool, web server runs as root! Now that's excellent security from a _security_ vendor :) Why would you trust these people to have this device on your network?!?!?"
According to the researcher, there are three other flaws within FireEye's products for sale. The vulnerabilities are an authenticated user command injection zero-day flaw, an unauthenticated remote root command injection and a login bypass zero-day vulnerability.
In an interview with CSO, Hermansen said while working with another researcher, Ron Perris, the two discovered 30 flaws in FireEye's product which included multiple root access issues. However, FireEye "balked" at every opportunity the researcher took to report vulnerabilities over 18 months -- leading to the eventual public disclosure.
"No one should be trusting these devices on their network if FireEye can't be bothered to fix the problems. As a security company, their standards should be higher," Hermansen told the publication.
In a statement, FireEye said:
"We appreciate the efforts of security researchers like Kristian Hermansen and Ron Perris to find potential security issues and help us improve our products, but always encourage responsible disclosure. FireEye has a documented policy for researchers to responsibly disclose and inform us of potential security issues.
We have reached out to the researchers regarding these potential security issues in order to quickly determine, and potentially remediate, any impacts to the security of our platform and our customers."
Top 5 security practices in staying safe online: From the experts
Read on: Top picks