Follow the money: The ROI Scareware, Spyware, click fraud, pharma spam

Massive banking exploits and easy to deploy threats will be more prevalent in 2010, but the real cash cows will remain scareware, spyware, click fraud, advance-fee fraud and pharma, according to Cisco's annual security report.
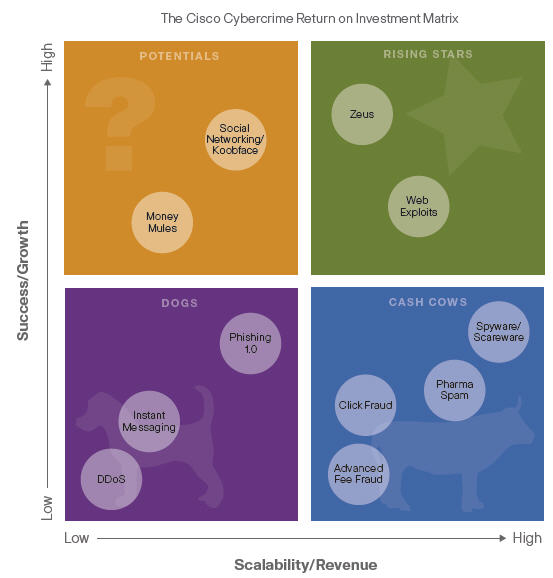
The report, which largely highlights the security threats to social networking, features an interesting matrix dubbed the cybercrime return on investment. If you ever wonder why threats are growing so rapidly all you have to do is follow the dough.
Cisco based its matrix on Boston Consulting's growth-share matrix with a twist. Here's a look:
Judging from this chart you can expect scareware, clickfraud and pharma spam to stick around for a while. Why ditch a moneymaker just for variety?
What remains to be seen is whether social networking threats become cash cows. Wouldn't it be ironic if criminals found a better way to monitor social networks than the actual sites themselves?
Among other key items in the report:
- Cisco deems the Zeus.A Trojan, which delivers malware via targeted phishing and drive-by downloads, as the most audacious criminal operation.
- Koobface, which appeared on Facebook in 2008 and Twitter in 2009, is the most notable criminal innovation. Koobface lures users into clicking a link for a YouTube video that launches the worm. More than 3 million computers have been infected by variants of this malware.
- Social media is an emerging spam vehicle, but the old pharma spam still works well. The Annual Security Report estimates that in 2010, spam volume will likely rise 30 to 40 percent worldwide over 2009 levels.
- Cisco cooked up "the Cisco Global ARMS Race Index" which measures “Adversary Resource Market Share” (ARMS) and provides a way to track the overall level of compromised resources worldwide—the networks and machines currently under “adversarial control.” It's a Richter Scale for security.