GoDaddy hosting customers victim to massive hack

[Updated 1:17 PM] Earlier this week I blogged about the case of Turkish hackers defacing a record number of websites. 38,500 sites were defaced in a single day by hacker iSKORPiTX who used an automated mechanism to attack what appeared to be an exploit in a sloppy implementation of ASP code (more than 21,000 sites listed here). But when I dug a little deeper (and courtesy of reader Toadlife's link), it appears that the exact same type of hack by the same hacker using the same exploit may have happened over a year ago to a GoDaddy ASP hosting customer in April of 2005. When I randomly sampled and inspected 40 of the defaced sites in the massive list, nearly everyone one of them were being hosted by GoDaddy hosting services.
More than a year ago in April 2005, a user going by the handle "buhusky" posted this question on the lockergnome.com forums. In it he asks:
Within one week of signing up for a $10 GoDaddy Deluxe Windows IIS hosting account I noticed a file in an "SSFM" subdirectory on my FTP / website. I did not create the directory or the file. The file itself read "HACKED BY iSKORPiTX" and had a Turkish flag and some other language on it. GoDaddy claimed that the SSFM subdirectory was required by their servers (so I couldn't just delete it & be done with it) and, in regards to the hack itself, said:
"Thank you for contacting Hosting Support.
This email is in regards to the issue that you escalated on xx xxxxx 2005. The ssfm hack is not something we can really defend against. It is a vulnerability in the Microsoft IIS webserving system. As Microsoft uses closed source software, we are dependant on them for a fix to this issue. They have not, as of yet, issued a patch for this vulnerability. Rest assured that your passwords have not been compromised. The attacker does not need these to insert his file into the account as it is done through a hole in the IIS system (and this is the only directory that they would have access to).
If you have any other questions or concerns please feel free to contact our customer support team.
Sincerely,
Advanced Support"
A Google search did not reveal anything useful. Anybody know what SSFM is for, or have any more info that could help me shed a light on this? Other than this I have been happy with the company in the brief time I've used them.
I contacted user buhusky to get more details about this incident but so far haven't managed to find him. Since this is a fairly serious matter that the vulnerability and compromise may have been reported over a year ago but the finger was pointed at Microsoft and nothing was done at GoDaddy, I contacted GoDaddy media relations. Even though IIS 6.0 (version used on the hacked sites) is very solid and has never had any critical vulnerabilities let alone unpatched ones, I emailed Microsoft to confirm if such an "unpatched vulnerability" in Microsoft IIS 6.0 allegedly referenced by GoDaddy support existed. Microsoft is still doing the verification of the ssfm ASP code found here in support forums talking about GoDaddy ASP hosting. [Update: Microsoft officially responded that the SSMF hack is not a Microsoft flaw]
Soon after emailing GoDaddy, I received an email from a GoDaddy public relations person and managed to talk with her on the phone. I forwarded this information to her and asked her to investigate if the quotation of GoDaddy "Hosting Support" was authentic and if they are aware of the massive hacking incident. She said she didn't know of any hacking incidents but would promptly look in to the matter.
A few hours later I was called back and told that the quotation could not be confirmed and that "no customer home pages were compromised". I asked GoDaddy's representative about the style and wording of the quote and if it was consistent with GoDaddy support but was told that "anyone can type something to look like a GoDaddy email". When I asked if they could confirm the massive hacking incident again, I was told that "no customer homepages were compromised and no files were added". But since that doesn't really answer my question if anything was hacked, I asked the question about 10 more times in different variations but got the same irrelevant answer over and over again. By that point it seemed like I was getting no where so I sent an email to this GoDaddy public relations person and asked if any files such as the specific URLs in the massive defacement list were modified by hacker iSKORPiTX. So far I haven't gotten a response to the email yet.
Here is a link to a mirrored archive of a hacked page which is a snapshot in time of what the hack actually looked like since the defaced page has been removed by now. Zone-H.org keeps a mirror archive of all the defacements as a permanent record. Roberto Preatoni who is founder of Zone-H told me that he personally remembers the massive defacement stayed up for over 2 days.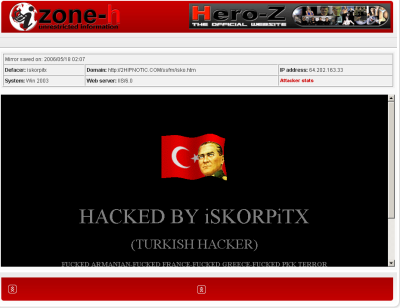
Based on Zone-H's record which is always verified to be accurate, tens of thousands of GoDaddy customers were defaced. Without some kind of investigation, we can't be certain if GoDaddy knew what and when but if the forum thread from April 2005 is authentic and accurate, then we have a big problem that nothing was done in over a year which resulted in the biggest mass web defacement ever. As a customer of GoDaddy hosting myself, I want to know the truth. I'll follow up with Microsoft's response to this incident and if GoDaddy gets back to me. Developing!