Government reveals draft digital identity framework

The Australian government has unveiled the public draft of its Trusted Digital Identity Framework for how citizens' digital identity information must be managed, which it said would sit alongside its Govpass digital platform.
The 14 draft documents include the Trust Framework Structure and Overview; Trust Framework Accreditation Process; Privacy Assessment; Core Privacy Requirements; Core Protective Security Requirements; Core User Experience Requirements; Core Risk Management Requirements; Core Fraud Control Requirements; Digital Identity Proofing Standard; Digital Authentication Credential Standard; Information Security Documentation Guide; and Risk Management Guide.
"The framework sets out a nationally consistent approach to how digital identity will be managed," Assistant Minister for Digital Transformation Angus Taylor said on Thursday.
"This includes documents outlining how providers will be accredited, privacy, security, risk, and fraud management requirements, as well as standards for usability and accessibility. The framework sits alongside the Digital Transformation Agency's Govpass technology platform, which is currently in private beta."
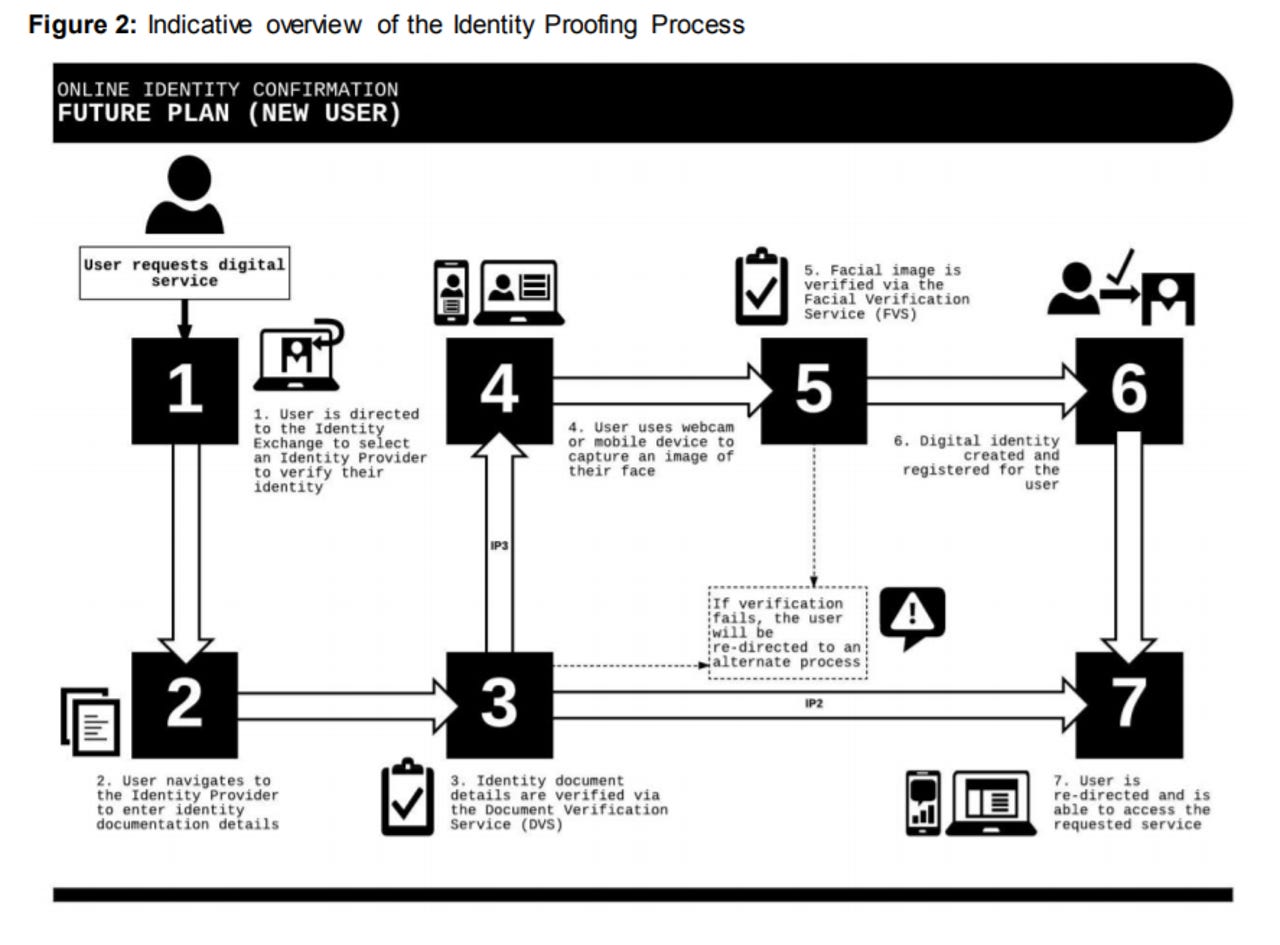
According to the Trusted Digital Identity Framework Structure and Overview [PDF], accreditation for the "identity federation" will be based on a trust framework rather than traditional service level agreements (SLAs) in order to provide more transparency and scale.
"The Digital Transformation Agency (DTA), in collaboration with other government agencies and key private sector bodies, is leading the development of a national federated identity ecosystem (the 'identity federation'). Implementation and operation of the identity federation is underpinned by the Trusted Digital Identity Framework," the document explains.
"It provides the required structure and controls to deliver confidence to participants that all accredited providers in the identity federation have met their accreditation obligations and as such may be considered trustworthy."
The Trusted Digital Identity Framework Core Privacy Requirements [PDF] outlines privacy requirements that must be fulfilled under the trust framework, including privacy governance; privacy impact assessments; data breach response management; privacy policy; notice of collection of personal information; collection and use limitations; consent prior to collecting information; cross-border and contractor disclosure; government identifiers; access, correction, and dashboard; quality of personal information; handling privacy complaints; and destruction and de-identification of information.
For instance, companies handling such data must have a "privacy champion" with overall responsibility and accountability for privacy; conduct annual privacy audits; report "serious" data breaches to the affected individuals, the Office of the Australian Information Commissioner (OAIC), the Trust Framework Accreditation Authority, and the Australian Signals Directorate (ASD); have a policy outlining whether and where it may disclose the information overseas; publish an annual transparency report; and provide users with access to their own metadata in a "yet to be determined timeframe" via a dashboard.
Identity service providers are also not permitted to collect sensitive information such as facial images unless consent is gained and the information is destroyed once used to verify an individual's identity; and provide a complaints service to users.
The Trusted Digital Identity Framework Core Protective Security Requirements [PDF] covers the minimum security controls that applicants must provide for an identity system.
These include network, operating system, database, and internal user access security; IT asset protection; strategies to mitigate cybersecurity incidents; physical and environmental security; using approved cryptographic algorithms, protocols, and modules; protective security awareness and training for employees; vulnerability and threat assessment; continuous monitoring and event logging; and incident response management.
"The applicant must undertake an active role in protecting their identity service, underlying business processes, and information assets from exposure to malicious software and scripts, including but not limited to: Implementing controls to prevent and restrict the proliferation of virus and trojan software," it adds.
"Equipment that supports the identity service must be protected from physical and environmental security ... all forms of media and storage devices which support the identity service must be controlled and physically protected."
Applicants must also have an Information Technology Security Manager (ITSM) and an Information Technology Security Officer (ITSO); use services with real-time alerts and availability monitoring; only use ASD-approved security products; forecast capacity requirements to avoid system overload; and undergo an annual independent assessment.
The standards for collecting biometric data and using facial images for matching are set out under the Trusted Digital Identity Framework Digital Identity Proofing Standard [PDF] (IdP).
An IdP is required to encrypt facial images using ASD-approved cryptographic algorithms; immediately delete facial images; "use liveness detection checks" in the facial verification service (FVS) to ensure the facial image is a real person; and ensure the person presenting a facial image is the legitimate owner of the documents being checked.
"The IdP must not store facial images or biometric data collected and matched using the FVS [or] disclose facial images to the Identity Exchange or other third parties," it added.
The Trusted Digital Identity Framework Core Risk Management Requirements [PDF] then covers the risk-mitigation responsibilities providers must implement; the Trusted Digital Identity Framework Core Fraud Control Requirements [PDF] defines the controls for preventing, detecting, reporting, investigating, and supporting the victims of fraud; and the Trusted Digital Identity Framework Core User Experience Requirements [PDF] ensures an applicant's identity system is "simple and easy for all to use".
The government is accepting feedback on its 14 draft documents until December 8.
Cloud services provider Vault Systems was last week announced to be the platform for the Govpass digital identity solution, after the Digital Transformation Agency (DTA) last month outlined the process for applying for a Govpass -- with the system to match users' facial images with their Medicare card, driver's licence, and birth certificate details.
"Privacy and protection of personal information is at the heart of the DTA's work on digital identity. Building trust in how the government stores personal data is not something we compromise on," DTA CEO Gavin Slater said.
"Vault's open standards cloud has been the perfect solution for Govpass, providing a level of security and sovereignty that is a critical to making the process of proving who you are to government simple, safe, and secure."
Vault Systems, Sliced Tech, and Macquarie Government all meet the ASD's requirements on storing highly classified government information.
DTA CDO Peter Alexander last month told the House of Representatives Standing Committee on Tax and Revenue that the Australian Taxation Office, the Department of Human Services, and Australia Post would be responsible for Govpass, as they "hold a lot of identity data already".
Taylor last week said the government would be taking its time to develop and deploy Govpass, rather than rushing the process, however.
"I have made it one of my highest priorities to get digital identity right. Now importantly, I said 'right'," he said.
"If we had rushed this, I think we would have inhibited digital take-up for years to come."
The federal government in May provided the Govpass program with AU$22.7 million during the 2017-18 financial year to complete its next stage of development.
"Govpass will provide a trusted digital identity framework for use by people needing to provide secure proof of identity to use government services online," the government said.
"In the future, this is expected to expand to be used by businesses. Govpass will link to existing document and facial verification services to establish identity."
Related Coverage
Trump administration releases rules on disclosing security flaws
The White House's cybersecurity coordinator said the rules are "vital" to ensuring a balance between public disclosure and retaining flaws for intelligence operations.
Australian IoT tick is to certify a device can be secure, not that it is: IoTAA
Since there is no such thing as an always secure device, Internet of Things Alliance Australia has said a certification tick will ensure a device can be secure if used in recommended ways.
DHS, FBI describe North Korea's use of FALLCHILL malware
The North Korean government has likely been using the malware since 2016 to target the aerospace, telecommunications, and finance industries, the US government says.
iPhone's Face ID can be hacked, but here's why nobody needs to panic (TechRepublic)
A Vietnamese company was recently able to trick Apple's facial recognition security feature, but security experts don't believe there's a big risk for business users.