Infamous Regin malware linked to spy tools used by NSA, Five Eyes intelligence

Last month, Der Spiegel published the source code of a malicious program dubbed QWERTY, which is a keylogger allegedly used in cyberespionage operations (.PDF) by a number of governments. Colloquially known as Five Eyes, the governments of the US, Britain, Canada, Australia and New Zealand are believed to be users of the spyware kit.
The keylogger plugin was built for the modular WARRIORPRIDE malware framework, the existence of which was revealed due to Snowden's released cache of confidential US intelligence documents. The simple plugin is designed to intercept all keyboard keys pressed by users and recorded for later scrutiny.
Regin, on the other hand, was discovered by Symantec last year and said to "display a degree of technical competence rarely seen and has been used in spying operations against governments, infrastructure operators, businesses, researchers, and private individuals." The backdoor Trojan has been in the wild since 2008 at the least, but due to a high level of stealth stayed off the radar until recently.
Featured
After acquiring a copy of the malicious files, security firm Kaspersky's experts Costin Raiu and Igor analyzed them and revealed that Regin is strikingly similar to the QWERTY keylogger program which is used by the NSA and the Five Eyes intelligence alliance.
"Looking at the code closely, we conclude that the "QWERTY" malware is identical in functionality to the Regin 50251 plugin," the duo say.
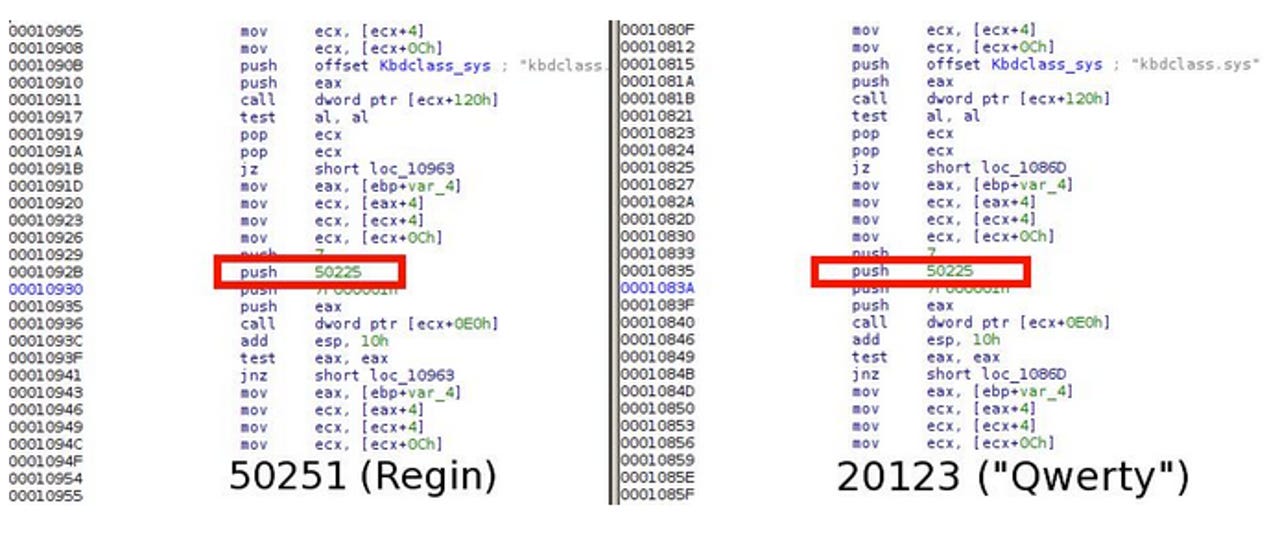
Throughout the team's analysis, they say the QWERTY module pack contains three binaries and accompanying configuration files. One particular file, 20123.sys -- the kernel mode part of the keylogger -- is particularly interesting as its source code can also be found in a Regin module, the 50251 plugin. Kaspersky says a "significant part" of code is shared between both malware strains, mainly belonging to the function that accesses the system keyboard driver.
In addition, the majority of the QWERTY components call plugins from the same pack, and one piece of code found in the spyware kit references plugins which exist in the Regin platform. The team states:
"One particular part of code is used in both the "Qwerty" 20123 module and the Regin's 50251 counterpart, and it addresses the plugin 50225 that can be found in the virtual filesystems of Regin. The Regin's plugin 50225 is responsible for kernel-mode hooking.
This is a solid proof that the Qwerty plugin can only operate as part of the Regin platform, leveraging the kernel hooking functions from plugin 50225."
Raiu and Soumenkov say their analysis indicates QWERTY is a plugin designed to work part of the Regin platform. Rather than operating as a stand-alone module, the keylogger relies on kernel hooking functions which are provided by the Regin module 50225.
"Considering the extreme complexity of the Regin platform and little chance that it can be duplicated by somebody without having access to its sourcecodes, we conclude the QWERTY malware developers and the Regin developers are the same or working together," the team says.
Read on: In the world of security
- Most US businesses vulnerable to insider threats
- Over 90 percent of data breaches in first half of 2014 were preventable
- Bluster, bravado and breaches: Today's 'terrorist' players in cybersecurity
- Mobile malware on the rise worldwide, ransomware hits the spotlight
- Verizon rushes fix for email account open season security flaw
- Microsoft Outlook hacked following Gmail block in China
- High volume DDoS attacks rise in Q3 2014
- Hackers for hire: Anonymous, quick, and not necessarily illegal
- UK hires hackers, convicts to defend corporate networks
- ZeuS variant strikes 150 banks worldwide
Read on: Fixes and Flaws