Microsoft: 92% of vulnerable Exchange servers are now patched, mitigated

Microsoft says that 92% of Exchange servers vulnerable to a set of critical vulnerabilities have now been patched or mitigations have been applied.
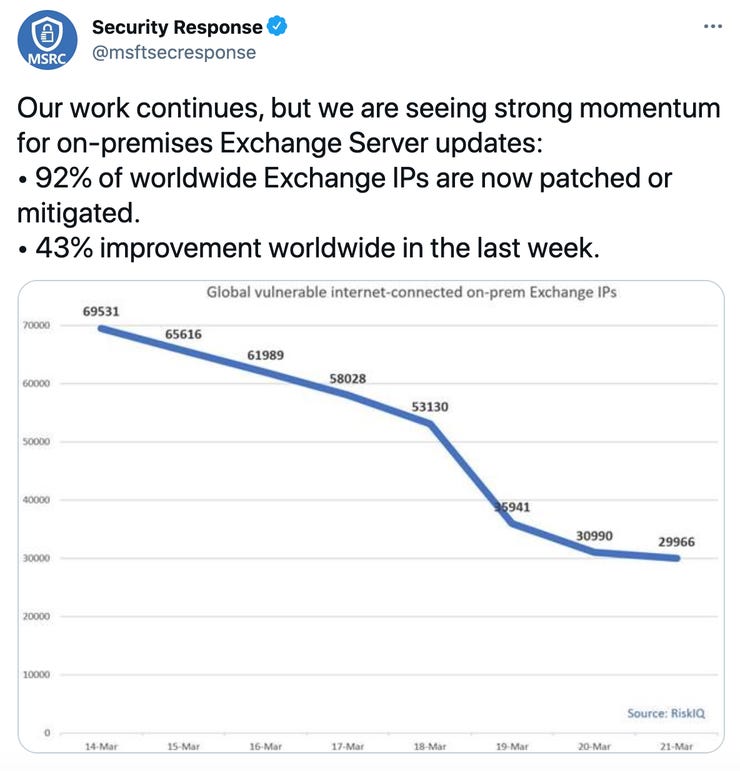
The Redmond giant's Security Response team said there is "strong momentum" in patches or mitigation tools being applied to internet-facing, on-prem servers and the latest data shows a 43% improvement worldwide in comparison to last week.
Microsoft cited telemetry from RiskIQ, which is working with the tech giant to manage the fallout of the security incident, in a tweet posted on Monday.
Microsoft released emergency patches for Microsoft Exchange Server 2013, Exchange Server 2016, and Exchange Server 2019 on March 2. At the time, the company said that four zero-day vulnerabilities which could lead to data theft and overall server hijacking were being actively exploited in "limited, targeted attacks."
However, it was not long before multiple advanced persistent threat (APT) groups began to join in Exchange Server-based campaigns and it is estimated that thousands of systems belonging to organizations worldwide have been compromised.
Alongside the emergency patches, Microsoft has also published a mitigation guide and created a one-click mitigation tool including a URL rewrite for one of the vulnerabilities to stop an attack chain from forming.
In addition, Microsoft Defender Antivirus has been upgraded to include automatic mitigation capabilities for the zero-day vulnerabilities.
The issue with these vulnerabilities, however, is that applying a patch or mitigations will not remove existing infections. F-Secure says "tens of thousands" of servers have already been breached and others "[are] being hacked faster than we can count."
While patches and mitigations are being applied at a fast rate, IT administrators must check their systems for indicators of compromise (IoCs) and perform security audits to see if their servers have been exploited prior to security updates being applied.
Previous and related coverage
- Everything you need to know about the Microsoft Exchange Server hack
- Microsoft Defender Antivirus now automatically mitigates Exchange Server vulnerabilities
- Microsoft Exchange Server attacks: 'They're being hacked faster than we can count', says security company
Have a tip? Get in touch securely via WhatsApp | Signal at +447713 025 499, or over at Keybase: charlie0