Microsoft study debunks profitability of the underground economy
A newly released paper presented by Cormac Herley and Dinei Florencio at this year's Workshop on the Economics of Information Security 2009 entitled "Nobody Sells Gold for the Price of Silver: Dishonesty, Uncertainty and the Underground Economy" debunks the often taken for granted profitability of the underground economy comparing it to that of a Market for Lemons, where the seller knows more about the product than the buyer.
Earlier this year, the same researchers also debunked the profitability of phishing (Microsoft study debunks phishing profitability) in general, using the Tragedy of the Commons as an analogy for their findings.
I beg to differ with the conclusions drawn in both papers, and here's why:
According to the executive summary:
"Stolen credentials are traded in bulk for pennies on the dollar. It is suggested that large sums move on these markets. We argue that this makes very little sense. Using basic arguments from Economics we show that the IRC markets studied represent classic examples of Lemon Markets. The ever present rippers who cheat other participants ensure that the market cannot operate effectively. Their presence represents a tax on every transaction conducted in the market. Those who form gangs and alliances avoid this tax, enjoy a lower cost basis and higher profit."
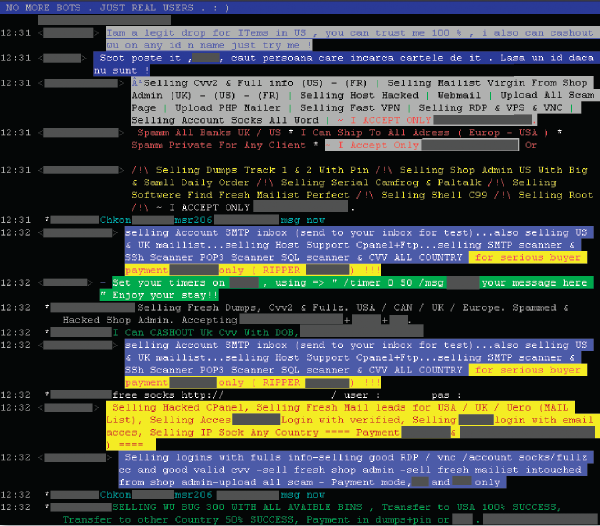
Trading with stolen credit card information over IRC is so Web 1.0, it encompasses a tiny percentage of these trades, the majority of which happen in closed invite-only portals next to the plain simple private communications with the vendor itself lacking a fancy online store for the stolen goods. Therefore, generalization based on a single, largely outdated distribution and advertising channel for stolen goods undermines the majority of conclusions made.
The researchers also find no sense in statements such as :
"For example, Symantec finds the asking price for a CCN varies between $0.5 and$12, even when the available balance is several thousand dollars. This makes very little sense. Why would anyone sell for 50 cents an asset that is worth $2000? If turning the CCN into cash requires skill that the seller does not possess it would surely be a skill worth learning."
They would not only because they would still break-even (earn profit) if they do so, but also, because depending on their position within they underground marketplace, they may in fact be willing to earn less, but forward the responsibility (and potential imprisonment if detected) to the buyers of credit card details while attempting to cash out the money.
Based on personal observations of numerous monetization approaches throughout the past several years, there's a majority within the underground ecosystem that whereas may indeed look like a hardcore cybercriminal cashing-out money from each and every phished and Zeus-ed (banker-malwared infected host) on his own, is in fact reselling access and the accounting data to the organized cybercrime syndicates with experience in obtaining the cash. If these cybecriminals were to "learn the skill" of how to do, they would inevitably be earning more, however, the money made is proportional with the increased risk of getting caught based on their lack of experience, so reselling the data to experienced parties as fast as possible, remains their only option.
Next -->
And since the value of the asset (stolen credit cards) is decreasing, the average seller is willing to ignore profit maximization for the sake of earning revenue, and a positive return on investment by using a simple logic in regard to the time value of money - a dollar today is worth more than a dollar earned tomorrow. What does this mean? It means that knowingly or unknowingly, perhaps even left without a choice since the details of a stolen credit card details today will worth nothing in , cybercriminals take advantage of the time preference.
Here are some of the characteristics of Lemon markets applied to the underground economy in the study, and the reasons why I find the conclusions drawn largely flawed:
- Asymmetry of information, in which no buyers can accurately assess the value of a product through examination before sale is made and all sellers can more accurately assess the value of a product prior to sale - Where do I begin? Buyers with well known and proven reputation, combined with a multitude of positive feedback by happy sellers command the market, and these people would not only include screenshots of their web malware exploitation kits, but will also come up with videos, in fact even issue demo accounts to potential buyers. The practice of issuing demo accounts or providing screenshots from within a particular service while it's attacking has proven pretty successful so far, at least judging from the hundreds of "happy cybercriminals" recommending others to do business with a particular vendor of a particular product/service. The value of the asset, whether a web malware kit or stolen credit cards is verifiable. In the web malware kit, either a trusted and well known administrator will get a free copy of it, test it and post positive feedback resulting in sales for the author, or the buyer will assess its value based on the modularity of the kit, and exploits used and the unique differentiation factors compared to other kits. In the stolen credit card case, either the reputation of the seller, or the small number of valid credit cards provided as a proof for the validity of the bulk order will result in a transaction. However, the singly most valuable boost for such an advertising campaign remains the moment when the malware kit is used in the wild and receives publicity thanks to a security vendor that has detected it as the kit used in a major successful malware attack.
- Sellers have no credible quality disclosure technology - Data speaks for itself. A screenshot demonstrating the conversion rate from traffic to infected hosts based on multiple browsers speaks for itself. Combined with a credible reputation from the seller and the countless number of happy clients, or sometimes a plain simple confirmation from a forum/community administrator that the seller is a well known cybercriminal and can be trusted can close the deal. The quality disclosure within the underground market place sometimes comes in the form of simple CHANGELOGS, to-do lists compared with the current features, or plain simple screenshot of a particular kit in action. As far as credit cards are concerned, valid samples of this commodity good are offered to potential buyers. Take for instance the ubiquitous Zeus crimeware kit and the fact that third-party developers are continuously improving its features, and keeping an account for the new features.
- Either there exist a continuum of seller qualities or the average seller type is sufficiently low - The research further implies that "The evidence certainly indicates that the average seller quality in the Underground Economy is extremely low, and cheating and dishonesty are rampant." Even if we take the truthfulness of this statement for granted, it would make the big picture even worse. Picture the currently booming cybercrime economy with massive malware generation that's entirely relying on low quality releases. What if, they actually start bothering for the quality of their products? Scammers or the so called rippers are present at the invite-only and closed communities, and they will always be, no doubt about it. In fact two years ago, it would have been nearly surreal to think that coders of popular crimeware kits like Zeus, or web malware exploitation ones would become victims of software piracy within the underground economy, inevitably shifting the trade of these products from a black market to a grey market where the manufacturer (author of crimeware) is no longer able to run a business model since ironically, there's no intellectual property law enforcement in a highly illegal market. Numerous authors, have however, not only attempted to forward responsibility for fraudulent activity to the customers by including disclaimers within their products, but also, issue licenses and copyright noticed which if in reality even get enforced would incriminate them as the actual owners of the crimeware kit. One thing remains for sure - when doing business no one is shooting into the dark, reputation, positive feedback, actual screenshots and demonstrations issued for a trusted seller is closing a deal.
- Deficiency of effective public quality assurances (by reputation or regulation and/or of effective guarantees / warranties - Quality assurance has been improving, and is in fact an inseparable part of the underground ecosystem. From quality assurance in malware campaigns, in the form of managed crypting in order to achieve a lower detection rate, to the automatic multiple-firewall bypass verification for a particular malware sample, cybercriminals are in fact constantly creating new market niches, and setting new benchmarks for the rest of the participants to catch-up with.
Next -->
Stolen credit cards are not the cornerstone of the underground economy, which like other economies is shifting from generating most of its revenue from products to generating it from services, or value-added ones. Cybercrime-as-a-Service is become the efficient response to the previously known inefficient models.
For instance, managed spam services, segmentation and localization of the harvested emails for better targeting, managed translation and social engineering services allowing Chinese spammers to disseminate a campaign in multiple languages next to performing targeted attacks by spamming banker malware, all indicate the sophistication of the underground economy and its clear obsession with quality assurance, which in the long term will come in the form of standardization courtesy of the managed service providers.
The bottom line - is in fact no one selling gold for the price of silver? That would have been true if the gold wasn't originally obtained for the price of iron, or stolen from other trading partners, allowing the new owner to earn a profit despite the lower selling price.
And even if the underground economy's profitability is greatly overhyped, a statement with I don't agree, the direct costs of cybercrime related incidents are pretty evident to everyone. And that's just the tip of the iceberg, since in the underground economy, the market capitalization is irrelevant to the fact that millions of end users and companies are suffering direct costs related the services and products -- including the supposedly low quality ones -- currently in circulation.
What do you think? TalkBack.