Operation Shady RAT: five things to know

On Tuesday in the US, Vanity Fair published a scoop explaining that cyber criminals have spent more than five years cautiously working to obtain data from more than 70 government agencies, corporations and non-profit groups.
(Credit: McAfee)
The campaign, named "Operation Shady RAT" — RAT as in "remote access tool" — was discovered by Dmitri Alperovitch, vice president of threat research at security firm McAfee.
While most of the targets have removed the malware, the operation persists. The good news: McAfee gained access to a command-and-control server used by the attackers, and has been watching silently (US law enforcement officials are working to shut down the operation).
Late yesterday, McAfee published a 14-page report (PDF) summarising its findings.
Here are five things you need to know:
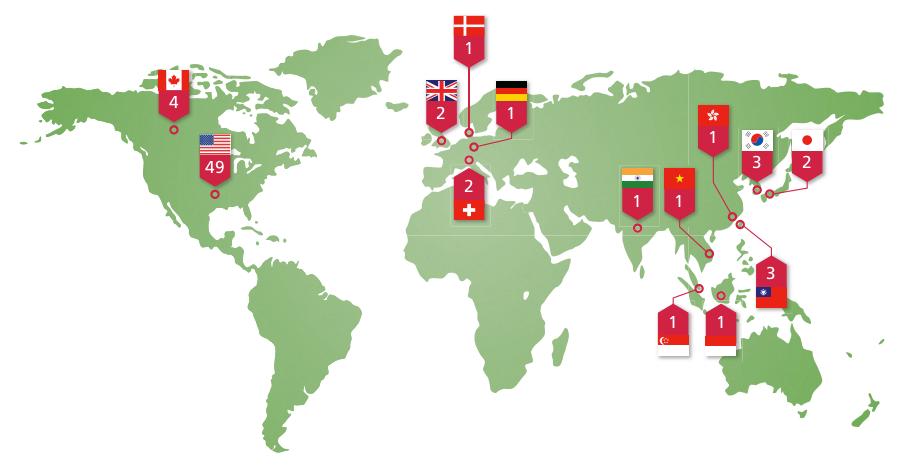
- 72 organisations were compromised. Among them: the US, Canadian, South Korean, Vietnamese, Taiwanese and Indian governments; the United Nations; industrial and energy corporations; electronics and IT firms; news media; defence contractors; real estate firms; sports groups and think tanks.
- It's not just North America and Europe. Sure, 49 of the targets were American, but Asian interests tallied 13 targets. Why? Political motivation: targets that include Olympic committees and political non-profit organisations show that the group was not "interested only in economic gains", Alperovitch writes in the report.
- When the coast was determined to be clear, the attackers struck. There were only eight intrusions in 2006, when the logs began, but the pace of activity jumped 260 per cent the following years, striking 29 targets. It jumped to 36 victims in 2008 and 38 in 2009, before slowing down, likely because of the availability of countermeasures for these kinds of intrusions.
- This was a single operation by a single group. It's not for the reason you think: "the key to these intrusions is that the adversary is motivated by a massive hunger for secrets and intellectual property; this is different from the immediate financial gratification that drives much of cybercrime, another serious but more manageable threat."
- "The only organisations that are exempt from this threat are those that don't have anything valuable or interesting worth stealing." Alperovitch said that he divides Fortune Global 2000 firms into two categories: those that know they've been compromised and those that don't yet know.
In closing, Alperovitch offers a sobering sense of scope for these kinds of cyber attacks, which he notes have occurred "relentlessly for the past decade", but have only recently gained press.
The loss [of this data] represents a massive economic threat not just to individual companies and industries, but also to entire countries that face the prospect of decreased economic growth in a suddenly more competitive landscape and the loss of jobs in industries that lose out to unscrupulous competitors in another part of the world, not to mention the national security impact of the loss of sensitive intelligence or defence information.
Via ZDNet US