Research: 76% of phishing sites hosted on compromised servers
The research also indicates that not only are legitimate sites (unknowingly) providing hosting services to scammers, but also that 19% of the vulnerable sites that they've analyzed were recompromised within six months.
This efficient exploitation approach using "evil searches" is in fact so efficient, that the majority of large scale SQL injection attacks that took place in 2008 were performing automatic search engine reconnaissance and later on exploiting the affected sites.
The trend has proven itself with cases where for instance the web sites of U.K's Crime Reduction Portal, a Police Academy in India, government servers across the world and even a Chinese bank were all hosting phishing pages through the exploitation of their web servers.
- Go through related phishing tactics and trends - Microsoft study debunks phishing profitability; Phishers increasingly scamming other phishers; DIY phishing kits introducing new features; Phishers apply quality assurance, start validating credit card numbers; Lack of phishing attacks data sharing puts $300M at stake annually
However, the long tail effect that they manage to successfully achieve through the automatic syndication of the very latest web application vulnerabilities within their botnets will continue resulting in such disturbing reports claiming that 500,000 web sites were successfully SQL injected in 2008 alone.
The bottom line - if you don't take care of your web application based vulnerabilities, someone else will. And yes, they will come back six months later to find out whether the web servers still remain vulnerable.
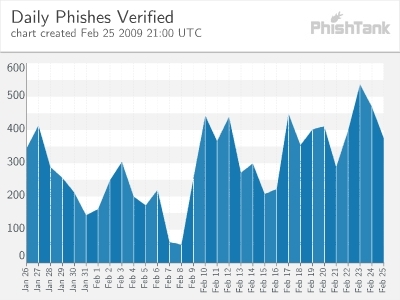
Image courtesy of PhishTank's February Statistics.