RiskSense working on AI to predict if vulnerabilities will turn into ransomware

Cybersecurity firm RiskSense, which has been at the forefront of diagnosing persistent threats for many years, on Tuesday announced a dashboard to warn companies how much they may be at risk from various kinds of ransomware.
The service, available as an update to the company's subscription-based SaaS software, is a visual monitor that shows various data, such as the number of vulnerabilities found across an enterprise's systems. It can be used not only to assess the situation but to plan a sequence of steps to remediate the matter. The dashboard is based on signals coming from typical enterprise security monitors such as those sold by Rapid7.
CEO and co-founder Dr. Srinivas Mukkamala told ZDNet the intention at some point is to fold into the product neural network capabilities for additional kinds of analysis such as regression analysis. That may let the company predict with some degree of useful precision how long it will be before a given vulnerability actually becomes "weaponized," meaning, turned into a threat in the wild.
For the moment, the dashboard is being rolled out to clients with a focus on detecting and classifying vulnerabilities: are systems at risk of ransomware, given that ransomware spreads mainly as a lack of attention to vulnerable systems.
Also: Ransomware: Prepare for hackers launching even more destructive malware attacks
"This is not an interesting problem," observed Mukkamala in a conversation by phone. "It boils down to basic hygiene: the majority of ransomware relies on vulnerabilities" and how to exploit them before they are patched.
The dashboard combines signals, on the one hand, from the sensors such as Rapid7 about what vulnerabilities exist in a computer system, with a variety of data about exploits in the wild. It uses those various pieces of information to reduce the list of roughly 25,000 known exploits in the world to a short list of 100 ransomware exploits for which a chief security officer should monitor.
"The way we look at it is as an expert system," says Mukkamala, using a traditional term from the AI literature for software programs that include a great deal of domain expertise. "What are my signals?" he asks, rhetorically. "First, a strong signal would be end-point vendors detecting it and blocking it, a second is Microsoft paying attention and raising the criticality, a third is people in the dark web chatting, and the fourth signal is pen testers [people who perform professional penetration testing to gauge systems weaknesses] are interested and are exploring it."
The dashboard had its genesis in a report put out in September by RiskSense that organized ransomware by family of malware, and by vendor and product, and provided lots of other ways to organize one's thinking. One thing that prompted the report was dissatisfaction with mainstream reporting on the phenomenon, said RiskSense's vice president in charge of products and marketing, John Dasher, in an interview with ZDNet.
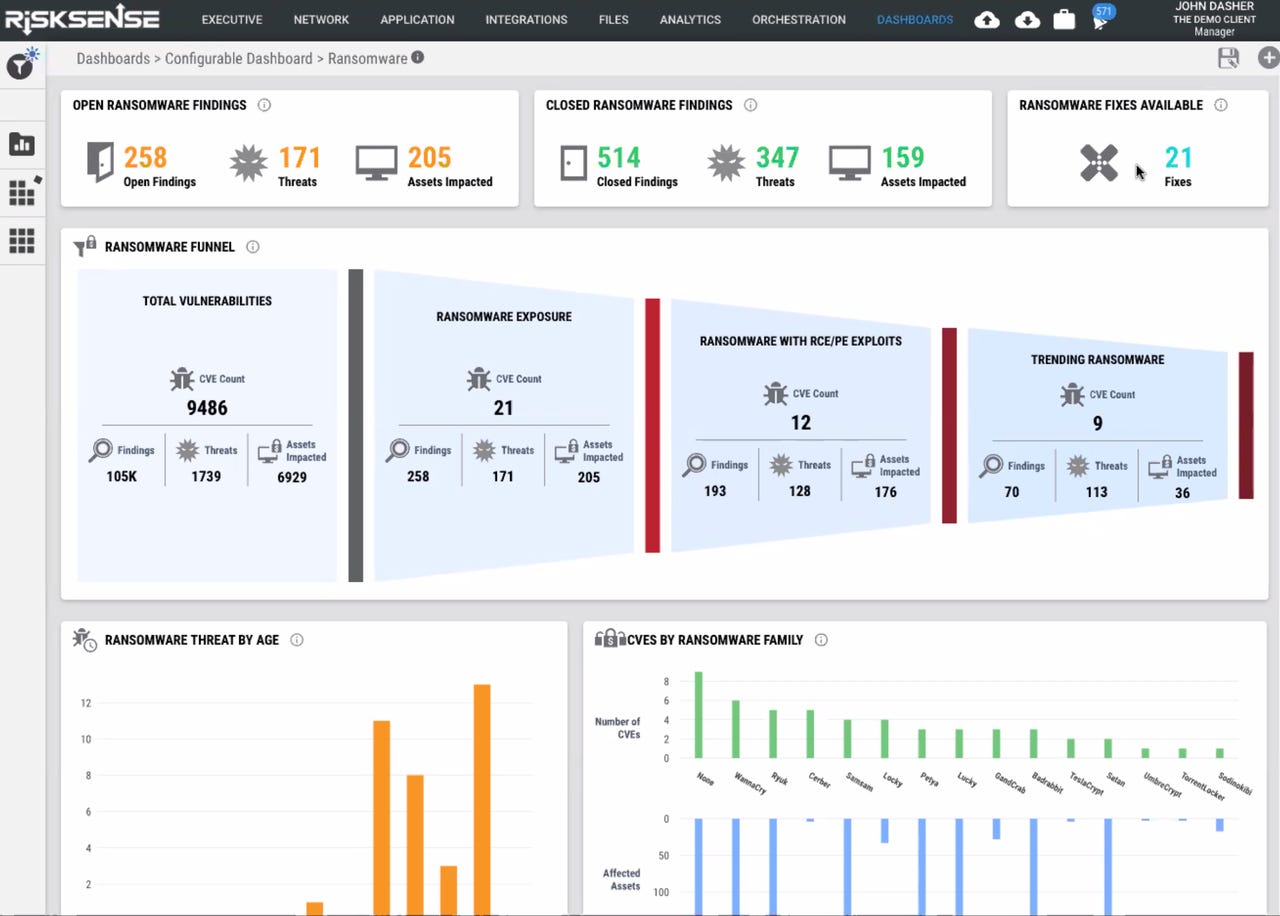
RiskSense's dashboard view of system vulnerabilities.
"We had seen more and more coverage in the news [of ransomware], and it was usually high level coverage, with occasional references to the family of exploit, but there was not a lot of detail, especially if you're a practitioner," said Dasher.
The response was quite positive to the report, said Dasher, however, "people came back and said, Please serve it up to us in a product." Hence, the dashboard.
It's the right time for such a tool, said Dasher, given that the increase in ransomware has made the phenomenon a board-level problem. That means chief security officers now have to answer to directors of the company about risks where once those CSOs toiled in obscurity within the bowels of IT.
Also: New York state wants to ban government agencies from paying ransomware demands
"We now see CSOs at board meetings, and they are being asked questions about ransomware," said Dasher, "so the other side of this is the business leadership view and how do you articulate your exposure to it."
However, as mentioned earlier, there is a frontier of deeper analysis that must urgently be developed. Today's classification is performed by older machine learning techniques, known as "support vector machines." SVMs were the popular machine learning approach in the 1990s, and Mukkamala introduced their use to cybersecurity in the first years of this century. It formed the core of his PhD and he holds a patent on the design of a system built on SVMs for the purpose of detecting threats.
SVMs work reliably for classification. And unlike most deep learning forms of neural networks, they can learn from very few data samples. "One of the fundamental things in favor of them, when I first picked up SVMs, was that they had been very well studied for drug prediction and cancer research and such," recalled Mukkamala. "My dad was a gastroenterologist, and I figured, if it can work for cancer, it should work well for cybersecurity."
Also: Ransomware attacks are causing more downtime than ever before
But SVMs, as good as they are, don't offer the power of regression analysis that is needed to see how a vulnerability mutates into a live threat in the wild. Mukkamala realizes that. RiskSense is hard at work, he said, to bring neural networks to regression analysis.
"What no one has done is regression" in the field of security, Mukkamala said. "A lot of people in security still talk classification, but you very rarely see us talk about something like whether a given exploit will be weaponized in the next six months."
"People will say, it will happen in the next 12 months, but, I'm sorry, that's hog shit, anything can happen in 12 months."
Last year's BlueKeep vulnerability is a perfect example of the uncertainty, he said. "It was the most talked about one [vulnerability], but it didn't have an exploit for close to 90 days," he recalled. In fact, RiskSense were the ones who wrote the exploit, to prove it could be done.
How can a machine tell if something like BlueKeep will be weaponized? RiskSense is working on a system that computes three different signals, said Mukkamala. The industry as a whole, he noted, "are scanning code at a machine level, then we are actually paying bug bounties to go find certain types of software vulnerabilities, and then there is also traditional pen testing dollars spent on software that's been released."
Also: BlueKeep exploit to get a fix for its BSOD problem
By combining those three signals, the goal is to "train the model to behave like a pen tester," said Mukkamala, "to predict real risk, to do the real regression." RiskSense hopes to have some results to talk about in a matter of months, he said, and the company will probably apply for a patent on technology to gauge individual application risk.
Such techniques, he said, are needed to match the evolution of ransomware, which is spreading beyond the operating system level. "They are going beyond the OS to use JBoss and Elastic and Adobe products," said Mukkamala of malware authors. "If we don't explore new methods" for tracking that evolution, "then we are looking backwards."