Secure application hosting

I have seen many diagrams of how to securely expose applications to the Internet. I even created a few of my own in a research note on the demise of the so-called demilitarized zone. To be clear, my argument was mainly one of nomenclature; why would you call a network segment a DMZ when it is the most highly protected portion of your architecture? Rather than call it a Highly Militarized Zone, HMZ, I suggested at the time (2001) that it be termed a Transaction Zone. Lately I have heard these architectures referred to as Secure Transaction Zones which is a pretty good term if slightly redundant.
Thanks to the need to demonstrate regulatory compliance there are a lot of organizations looking to outsource non-core applications to hosting providers that can accommodate the alphabet soup of HIPAAGLBSOXFFEICPCI1386. Today I am launching a monthly series of webinars in which I will invite various security companies to present. The goal is to be educational and expose attendees to new ways of countering threats. I think of it as taking the podcasts to the next level by making them live. I have yet to figure out how to record these webinars so you have to attend real time if you want to hear today's webinar with a company here in Michigan that I have watched for almost five years. Matthias Horch, one of the founders of Secure-24 is presenting. He is a brilliant engineer and has devised a service delivery model that has led to them becoming a leader in secure application hosting.
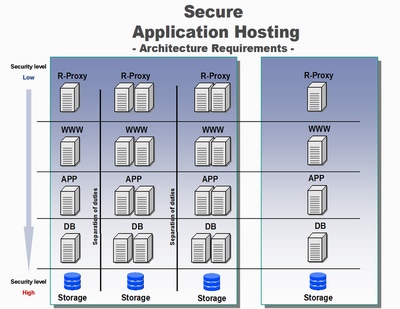
Here is one slide from his presentation. It depicts the layers needed to host an application (reverse proxy, web server, application server, data base server and off site storage) and also host the development and staging stack of servers and even the fail-over site.
Register now for the free webinar starting at noon Eastern today.