Slow clap: Internal certificates can hijack gTLDs

Domain name squatting could become more than an inconvenience due to an oversight on how internal site certificates can be used on generic top level domains (gTLDs) without necessarily being the owner of the gTLD.
As discussed in an advisory (PDF) issued by the Internet Corporation for Assigned Names and Numbers' (ICANN) Security and Stability Advisory Committee (SSAC) on Friday, a common practice by certificate authorities (CAs) is to issue digital certificates, even when the organisation requesting them provides a non-fully qualified domain name.
These "internal name" certificates are meant to be used for domains on private networks, such as server1.company.corp, that were never intended to be public facing. While this affords companies a convenient way to securely reference servers within their network, the internal name of their domains can potentially collide with gTLDs that either already exist or are being applied for.
This theoretically affords an attacker the ability to apply for a site certificate for a gTLD before it is approved, then once the target gTLD passes approval, the attacker has a signed certificate that can be used to conduct man-in-the-middle attacks.
"If an attacker obtains a certificate before the new TLD is delegated, he/she could surreptitiously redirect a user from the original site to the attacker site, present his certificate, and the victim would get the Transport Layer Security/SSL (TLS/SSL) lock icon," the advisory read.
Testing the theory, a SSAC researcher applied for an internal name certificate for www.site, and although the CA asked the requester to confirm it was for internal use only, approved its issuance. Armed with a certificate, the researcher then set up www.site, and found that several modern browsers recognised the certificate as though it had been issued for the gTLD and not an internal server.
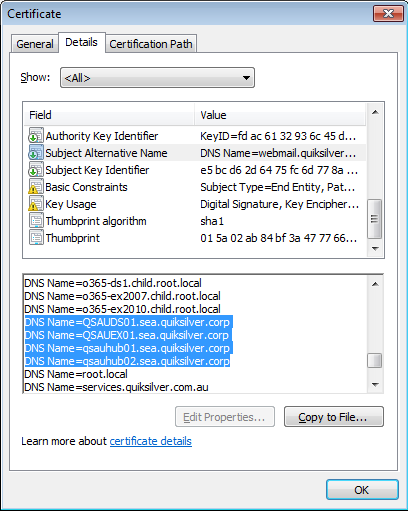
The problem is not confined to new domains, and is potentially already a problem. As part of its research, SSAC noted that as well as listing valid entries for its business, Australian clothing retailer Quiksilver's certificate lists internal names ending in .corp — a gTLD that has recently been applied for.
Looking through the Electronic Frontiers Foundation's SSL (Secure Sockets Layer) Observatory project data from 2010, there are at least 157 CAs that have issued internal name certificates. As internal name certificates are not always publicly visible (as they are for internal systems only), SSAC noted that "there is no way of knowing how many of those certificates exist unless certificate authorities voluntarily disclose them".
SSAC has been working with a number of affected parties, including the CA/Browser forum. The latter industry forum has requested that its member CAs stop issuing internal name certificates by November 1, 2015, and inform any further applicants that the practice of issuing certificates for internal systems has been deprecated. Members are also requested to revoke any unexpired and affected certificates on October 1, 2016.
While SSAC commended the CA/Browser forum for this initiative, it wrote in its advisory that this still represents a problem, as gTLDs will still be vulnerable over the next three years until October 1, 2016.