SonicWall seeing a Cambrian explosion of side-channel attacks

SonicWall is seeing a boom in malware authors exploring the potential of memory side-channel attacks, following the publication of the Meltdown vulnerability at the start of the year.
Due to the patches for Meltdown resulting in potentially large performance hits, or needing to purchase new chips when Meltdown-safe CPUs appear, SonicWall CEO Bill Conner told ZDNet a new type of solution was needed.
"You need to solve this in a different way because new chips aren't going to be there for a while, and I don't know many people that are up for 30 to 40 percent hit on processor [performance]," he said. "It's a very expensive proposition."
"[It's] a very different time to correction in the market, and business issues around the security risk profile on that."
Using its real-time deep memory inspection engine, CTO John Gmuender said the company was seeing a lot of side-channel proof of concepts "flying about".
See also: What is malware? Everything you need to know about viruses, trojans and malicious software
"Those malware writers are no different than any other software engineer, they launch many different variants of malware everyday, but they are not rewriting the code from scratch every time," he said. "You can assume they are hard at work ... finding the unique ways to use it in combination with a set of other things.
"The interesting thing is we uniquely have an environment that can see this happening, the attempts happening, and we were somewhat surprised that there was so much of it."
According to Gmuender, the company's malware analysis framework is able to track memory allocations and do analysis when the malware controller is suspended, allowing for the detection of side-channel attacks, which led it to being "somewhat surprised" at the number of attempts it was seeing.
"Essentially, the best weapons are decrypted into memory, executed, and then they wipe it from memory so that you can't see those or use that in the future," he told ZDNet. "We've seen that that code can be so small, where this happens all in less than 100 nanoseconds."
"We did a lot of analysis ... and machine learning we found this was a more common technique, a very difficult one to do in an analysis environment -- which is log activity while it is executing then try to look at it post-execution ... [and] it's producing a lot more detections than we had using existing technology."
On Tuesday the company released its 2018 SonicWall Cyber Threat Report, which said the company expects to see "password-stealers and infostealers" based on vulnerabilities such as Spectre and Meltdown.
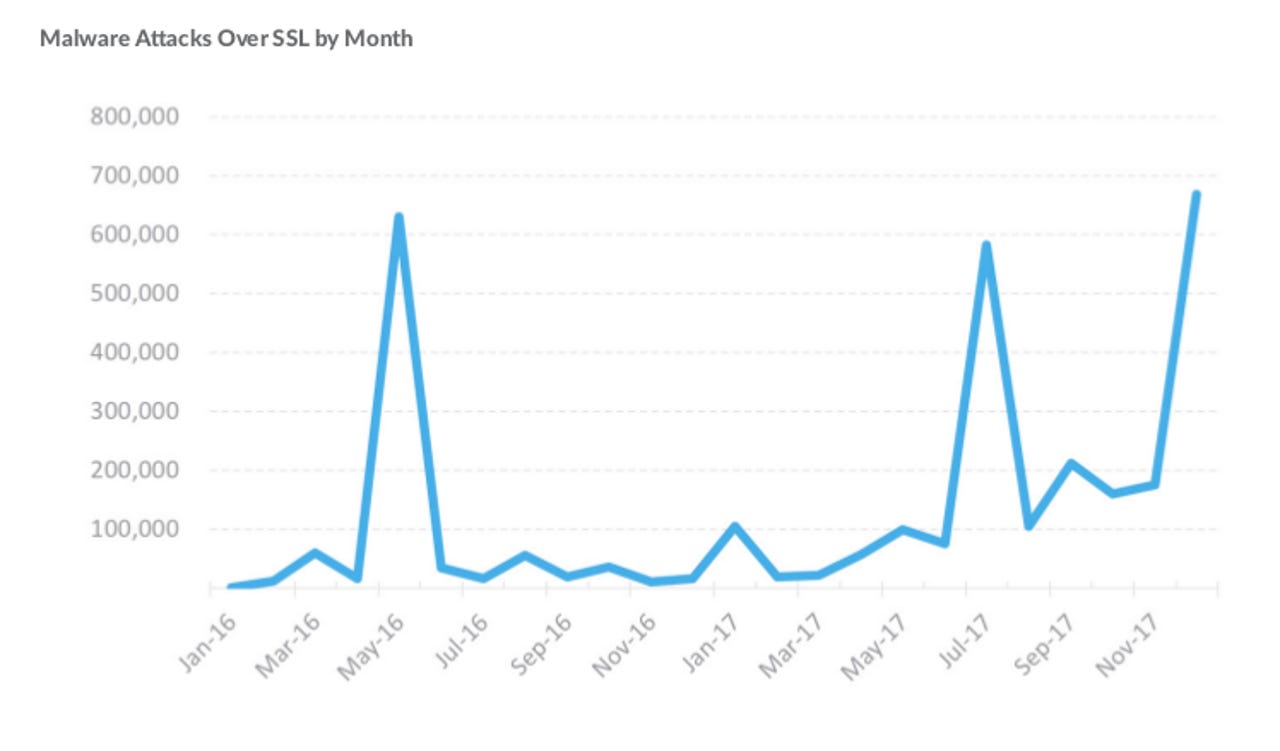
Not surprising for a firewall company, the report said the use of SSL was helping to hide malware propogation from those without deep packet inspection hardware.
"Based on data from the subset of SonicWall firewalls using DPI-SSL, an average of 4.2 percent of all file-based malware propagation attempts used SSL/TLS encryption in 2017," the report said. "SonicWall Capture Labs found, on average, 60 file-based malware propagation attempts per SonicWall firewall each day."
Gmuender told ZDNet the company was also seeing an increase in file dropping malware using TLS, as the number of sites switching to SSL continues to increase, which goes against user expectations that SSL sites are safer.
In the ransomware space, the report states that 2017 saw 184 million ransomware attacks, down dramatically on the 638 million detected a year prior, and bitcoin addresses attached to ransomware saw few or zero transactions.
"Comparing this year's ransomware attacks that were tied to a single bitcoin wallet (or a handful, like WannaCry's three known wallet addresses), SonicWall has seen fewer transactions than that of the previous year's attacks," the report said.
Despite the lower number of attacks, the report stated that the number of ransomware variants had doubled to 2,855 for the year.
With the rise of cryptocurrencies, the report said mining malware will increase, particularly on Windows and Android.
"If your machine is unprotected enough to get malware miners on it, it's also unprotected enough to get the rest, and there is so much hidden, you would quickly not just be the owner of a computer that has mining malware on it, but lots more," Gmuender said.
"It's bad, but it is probably less bad than having your hard disk wiped out with no backup."
SonicWall was spun out of Dell Technologies in November 2016, and remains controlled by Francisco Partners and hedge fund Elliott Management after the pair picked up Dell Software Group for over $2 billion.
Francisco Partners purchased Comodo's certificate authority in November 2017 for an undisclosed amount, where Conner serves as its chair.
Related Coverage
SonicWall, SentinelOne partner for SMB network and endpoint protection
The two companies will deliver automated breach detection, prevention, and remediation to the small to medium-sized business segment.
SonicWall reports 638 million instances of ransomware in 2016
The network security firm said ransomware was the payload of choice for malicious email campaigns and exploit kits in 2016, with Locky claiming the title as the most popular payload globally.
Hidden 'backdoor' in Dell security software gives hackers full access
The critical flaw gives an attacker 'full control' of all connected devices.
Why ransomware attacks were so powerful in 2017 (TechRepublic)
Ransomware attacks targeting businesses is up 90%, and the monthly rate of ransomware attacks has increased tenfold in the past two years. Malwarebytes CEO Marcin Kleczynski explains why.
New ransomware headache as crooks dump bitcoin for rival cryptocurrencies
The switch to new digital currencies will make life more difficult, according to one police chief.