Forefront Threat Management Gateway 2010

Microsoft's ISA server has grown a loyal following over the years, from a shaky start with Microsoft Proxy server, through Internet Security and Acceleration (ISA) Server 2000, 2004 and most recently 2006. The recently released Forefront Threat Management Gateway 2010 (TMG) is the latest offspring in this lineage.
This is a very different product, though: it's 64-bit only, with built-in URL and anti-malware scanning, outbound SSL inspection and a real intrusion detection and prevention system.
Easy to configure
Some IT security professionals turn up their noses at a firewall from Microsoft, seeing it as a 'small business product', certainly not ready for the real world. ISA's reputation has, however, deservedly grown over the years, proving it to be a comprehensive, secure and scalable application-layer firewall. The last point is probably the most important one: old-school firewalls attempt to inspect network traffic based on port numbers, but threats today can hide in any protocol, on any port. Thus, an effective firewall needs to look inside network packets and understand protocols so that malicious traffic can be identified — something that ISA did very well. Forefront TMG continues that tradition with even deeper inspection of HTTP and now HTTPS traffic.
The other unique feature of ISA server has always been ease of use. A misconfigured firewall is arguably more dangerous than no firewall at all, and Forefront TMG goes all out, providing easy-to-use wizards for configuring most options. Large implementations can have many firewall rules; a new feature allows similar rules to be grouped together, making it easier to navigate them.
The invisible SSL tunnel
The problem traditional firewalls have is that they can't see inside an HTTPS tunnel that's established between the client browser and a website on the internet. This is something the black hat community often takes advantage of; after all, a "secure" website is simply a site/part of a site that provides an SSL certificate issued by a Certificate Authority to the client browser. Most users never look at those certificates, even if they take notice of the padlock icon. So malware can be downloaded to a client computer, bypassing the oblivious firewall.
TMG, however, has x-ray vision, enabling it to look inside SSL encrypted traffic, a feature known as HTTPS Outbound Inspection. It does this by pretending to the client that it's a secure webserver on the internet, intercepting the SSL traffic, decrypting it, inspecting it for malware and company policy violations (after all, is https://www.porn.com any better than http://www.porn.com?).
Certain client computers and particular destination sites can be excluded from scanning and users can be notified that the session is being inspected by TMG if they have the firewall client installed.
Before considering implementing this powerful feature, involve the legal department: if banking sites, for instance, aren't excluded from scanning, IT will have access to user names and passwords for those sites.
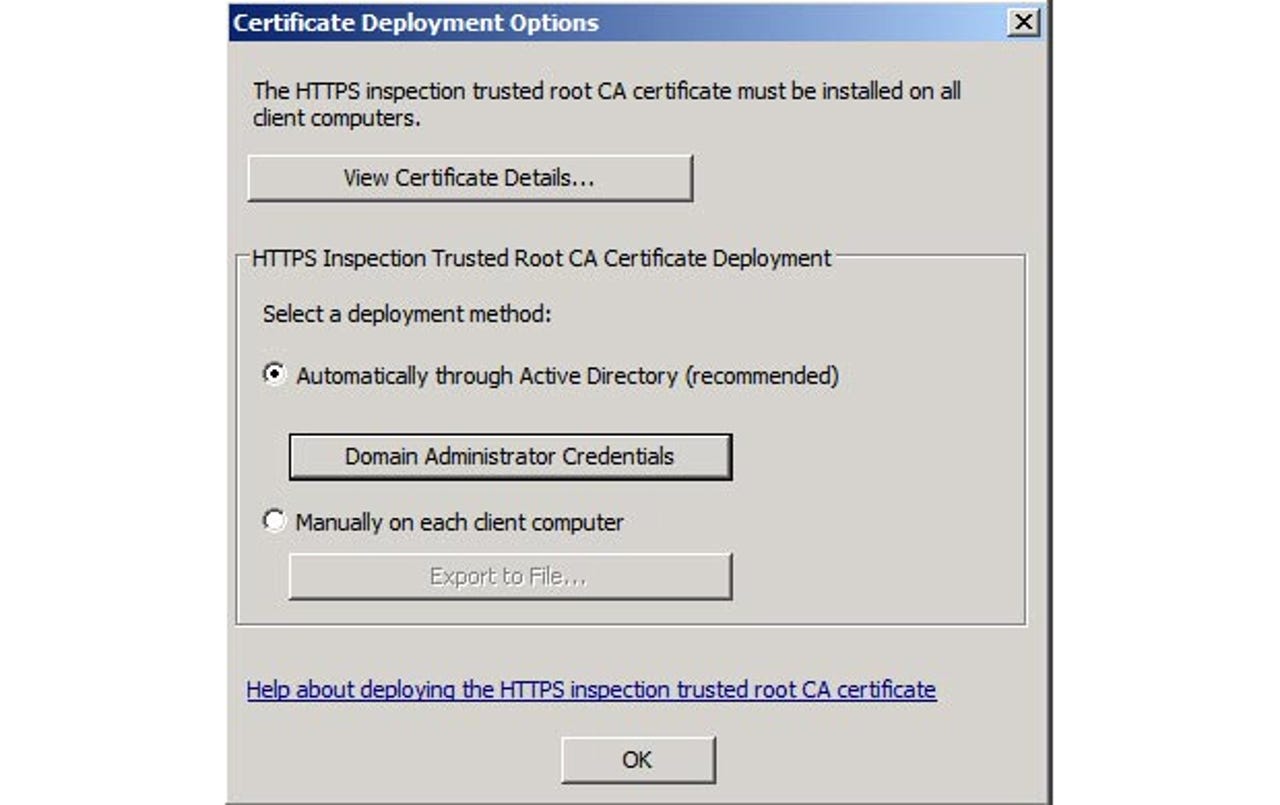
For Outbound HTTPS inspection to work each internal client computer needs to have a self-signed certificate for the TMG server installed
Malware beware
Malware scanning wasn't available in ISA server except through third-party add-ons, and was one of the most requested features for TMG. Anti-malware is now built into TMG via a subscription licence called TMG Web Protection Service, which is purchased either through the Forefront Protection Suite or the Enterprise CAL on a per-user basis.
Settings for the anti-malware component
Having anti-malware scanning of the data stream coming from (and going to) the internet is ideal, as malware is blocked right at the edge of your network rather than being routed to servers or clients before it's scanned. If a large file is scanned, TMG will inform the client of the delay through pop-ups from the firewall client.
Dodgy sites beware
The second most requested feature for TMG was probably URL scanning. The ability to block certain web sites or categories of web sites is necessary in large businesses. This new feature relies on Microsoft Reputation Services (MRS), which aggregates information from Internet Explorer 8 Smart Screen, Marshall 86 and Brightcloud, as well as Hotmail. There are over 70 categories of URLs and it's easy to create a rule to block particular categories. There's an interface for entering a URL to find out which category it's in, as well as the option to report wrongly categorised URLs. This feature is also part of the TMG Web Protection Service subscription, as the list is dynamically updated (checked every 15 minutes by default).
Control over what sites your users are allowed to visit is important
Intrusion detection and prevention
ISA's ability to detect intrusion was very rudimentary; TMG comes to the party with a full-fledged intrusion prevention system called Network Inspection System (NIS). Relying on a Microsoft Research development called Generic Application Protocol Analyzer (GAPA), NIS inspects all network traffic, looking for signs of Windows exploits. TMG will also participate in Security Assessment and Response, and aggregate information from NIS back to the Forefront Protection Manager central console if it's installed. NIS is also unique in that it identifies malware based on the signature of a vulnerability, rather than the signature of the exploit. Other intrusion detection systems need a signature for each variant of the exploit.
The main value of NIS is that it'll give network nodes quick protection against new exploits — it's much faster for Microsoft to write a signature for NIS than it is to build and test a patch.
More requested improvements
Many Exchange 2007/2010 deployments take advantage of the Edge server role to provide message hygiene and anti-spam; TMG can be installed alongside the Edge role, providing all the features in one server. Forefront Security for Exchange can also run on the same server, providing for a true one-stop shop for your edge protection.
As internet connectivity becomes more crucial for businesses, TMG offers seamless failover between two ISP links, either as a load balanced set-up where both links are in use, or with one link as a backup if the primary link fails.
Use two links to the internet, either for aggregated bandwidth or failover
Network Access Protection (NAP) is a new feature of Windows Server 2008, providing baseline health criteria for client computers before they're allowed access to the network. Checks include seeing if the antivirus is enabled and up-to-date, the host firewall turned on, patches are updated and so forth. TMG fully supports NAP when acting as a VPN server.
If you're using VoIP in your network, you'll be happy to know that TMG understands the SIP protocol and its secondary connections, and helps VoIP traffic traverse the firewall. In scenarios where multiple mail servers are published behind a firewall, other mail servers on the internet are likely to do reverse DNS look-ups to determine if the published mail servers are spam hosts. In ISA, each server would have the same IP address thus not matching the DNS records. TMG offers enhanced Network Address Translation (NAT) and allows allocation of specific IP addresses to each published server.
Secure Sockets Tunneling Protocol (SSTP) is a new type of VPN in Windows Server 2008 and Vista, providing easy connectivity from client computers connecting from locations where traditional VPN ports (1723 etc) are blocked, as it connects over port 443. TMG fully supports acting as the VPN endpoint for SSTP VPN clients.
TMG works well as a secure VPN server
Three flavours
Just like ISA server, TMG comes in Standard and Enterprise editions. The Standard version supports up to four CPUs and 2GB of RAM, while Enterprise has no limitations. Enterprise also adds the ability to create load balanced arrays of TMG servers, sharing caching through Cache Array Routing Protocol and supporting the management of all TMG servers through a central console. Unlike ISA server, where an array had to be planned in detail before deployment, an array in TMG can be built incrementally, adding one server after another as required.
What's new is that the Standard edition TMG (in a branch office for instance) can be managed from the Enterprise console.
The third flavour of TMG, Medium Business Edition (MBE) comes as part of Microsoft's Essentials Business Server (EBS), which is aimed at medium-sized businesses with up to 300 users. It can also be purchased separately.
The sum of all parts
Missing from TMG is support for Direct Access, the new type of VPN provided in Windows Server 2008 R2 and Windows 7, and although full support and enhancement of this feature is provided in Forefront Universal Access Gateway (UAG), it would have been good to have it in TMG.
NIS only inspects for Microsoft flaws at the moment; if another application on your network is vulnerable, it won't spot it, something Microsoft is aware of and working on. But overall, TMG has some great enhancements over ISA server, turning a good firewall into a true Universal Threat Management (UTM) solution, with support for secure web access from the inside, secure publishing of resources to the outside, and anti-malware built in.
See Microsoft's web site for Forefont TMG 2010 pricing and licensing.