Google, Twitter, Tumblr fix bug exposing users to data-stealing Flash attack

A new "weaponised exploit" that abuses Adobe Flash has forced Google, Twitter, Tumblr, and others to fix a well-known weakness in widely-used web tools that allow an attacker to extract sensitive data from users' devices.
The attack tool, dubbed Rosetta Flash by Google researcher Michele Spagnuolo, affects popular websites that rely on JSON with padding or JSONP, which is used by web programmers to get around browser restrictions on sites sharing data between different domains.
Rosetta Flash abuses a weakness in Flash (.swf) files to run a forged cross-site request forgery (CSRF) exploit and steal data from a machine visiting a particular site. The attack is notable since it isn't specific to a particular browser or operating system.
Tech Pro Research
Google services that were vulnerable to the attack included Accounts, google.com, Maps, and others, however the company had fixed the issue before Spagnuolo published details the "weaponised exploit".
Twitter and Tumblr have implemented fixes for the vulnerability too, but Instagram and eBay were also vulnerable, according to Spagnuolo. It's not known if either has implemented a fix. (We've asked both sites for comment and will update the story if any is forthcoming.)
A Facebook spokesman told ZDNet that Instagram has also rolled out a fix for this issue. He added that Instagram user data was not at risk from the bug since it doesn't store user data at that hostname.
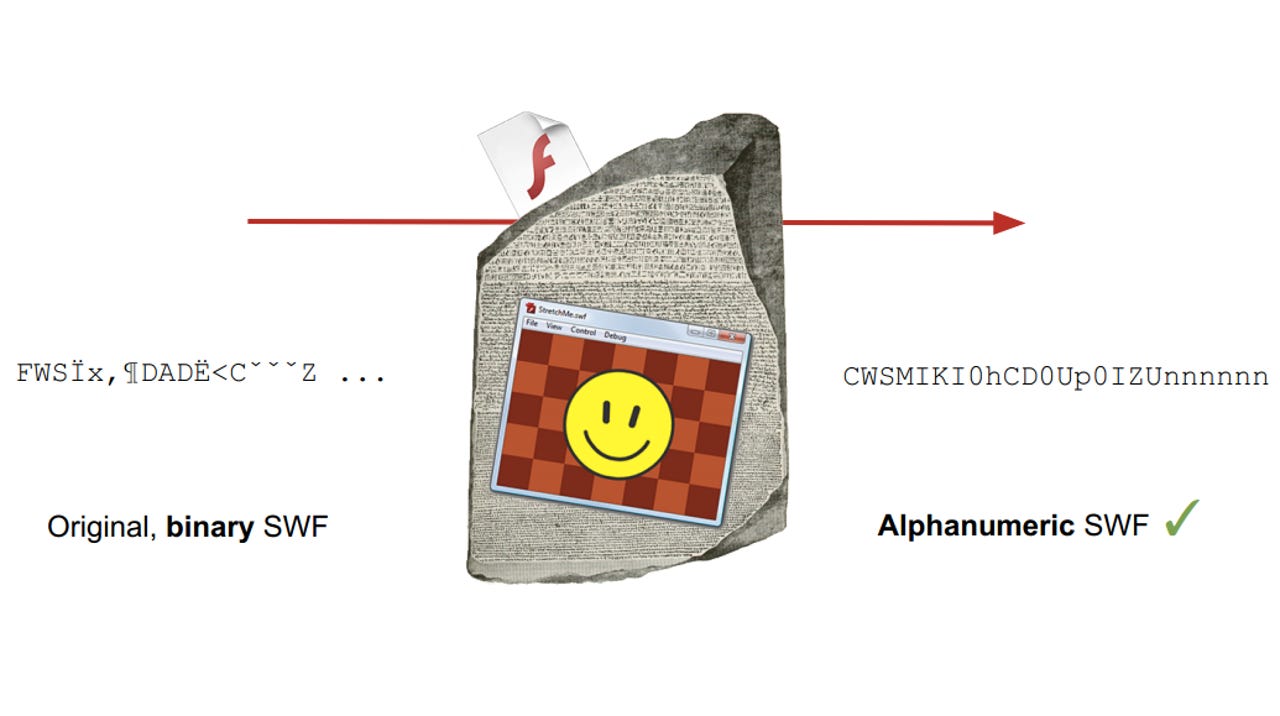
To exploit the weakness, the researcher devised a tool that converts "any SWF file to one composed of only alphanumeric characters in order to abuse JSONP endpoints. The exploit forces a victim to "perform arbitrary requests to the domain with the vulnerable endpoint and exfiltrate potentially sensitive data, not limited to JSONP responses, to an attacker-controlled site".
The attack bypasses the Same Origin Policy restrictions incorporated into all browsers to effectively host a rigged Flash file on the vulnerable domain.
Spagnuolo notes that the JSONP weakness is a well-known issue among security researchers that's been largely ignored by the web industry in the absence of a credible proof of concept.
For its part, Adobe released a security update on Tuesday addressing the weakness that allowed the researcher to create a malicious Flash file.
The attack has three key components that take advantage of permitted actions within Flash and websites that rely on JSONP. "With Flash, a SWF file can perform cookie-carrying GET and POST requests to the domain that hosts it, with no crossdomain.xml check. This is why allowing users to upload a SWF file on a sensitive domain is dangerous: by uploading a carefully crafted SWF, an attacker can make the victim perform requests that have side effects and exfiltrate sensitive data to an external, attacker-controlled, domain," notes Spagnuolo.
Rosetta Flash is configured with alphanumeric characters to bypass typical restrictions websites place on JSONP call backs.
"JSONP, by design, allows an attacker to control the first bytes of the output of an endpoint by specifying the callback parameter in the request URL. Since most JSONP callbacks restrict the allowed charset to [a-zA-Z], _ and ., my tool focuses on this very restrictive charset, but it is general enough to work with different user-specified allowed charsets.
"SWF files can be embedded on an attacker-controlled domain using a Content-Type forcing <object> tag, and will be executed as Flash as long as the content looks like a valid Flash file," Spagnuolo adds.