Microsoft: COVID-19 malware attacks were barely a blip in total malware volume

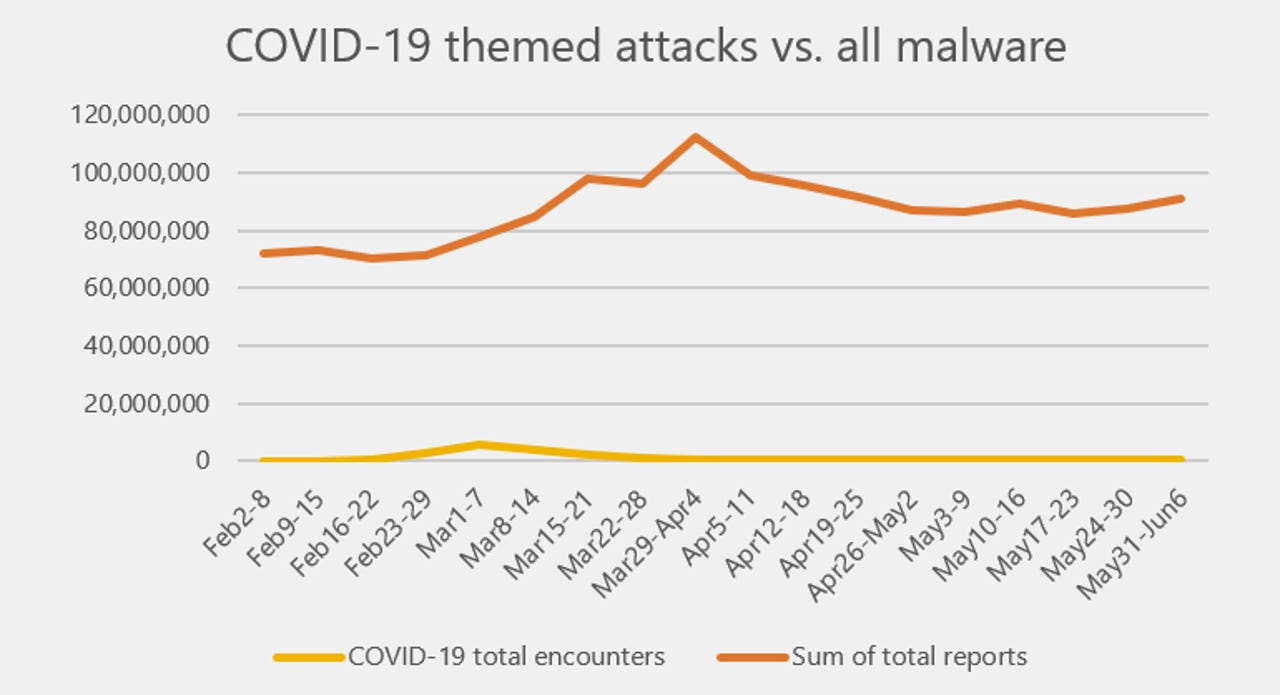
Microsoft says that despite all the media headlines over the past few months, malware attacks that abused the coronavirus (COVID-19) theme have barely been a blip in the total volume of threats the company sees each month.
These COVID-19 attacks included emails carrying malicious file attachments (also referred to as malspam) and emails containing malicious links that redirect users to phishing sites or malware downloads.
According to Microsoft's Threat Protection Intelligence Team, the first attacks abusing a COVID-19 lure started after the World Health Organization (WHO) declared COVID-19 a global pandemic on January 30.
As the world yearned to learn more about this new disease, attacks intensified, and they peaked in March when most of the world's countries enforced stay-at-home measures.
"The week following [the WHO] declaration saw these attacks increase eleven-fold," Microsoft said. "By the end of March, every country in the world had seen at least one COVID-19 themed attack."
However, Microsoft says that attacks plateaued soon after, as the public interest died down and as malware operations settled into a "new normal."
Microsoft's security team says that most of the COVID-19 campaigns they tracked were highly localized. Malware campaigns usually targeted users in a specific country and weaponized local news and local developments to increase the attack's chances of success.
"They preyed on our concern, confusion, and desire for resolution," Microsoft said, referencing the old adage that hackers will never let a good crisis go to waste.
Furthermore, as major players like Lokibot, Emotet, and TrickBot joined the attacks, Microsoft says that malware groups didn't put particular effort into exploiting the COVID-19 theme.
Just like Proofpoint reported before it, Microsoft says that criminal groups repurposed old attack infrastructure and continued to deploy the same malware they used before. The only change they made was to update old email templates to exploit the new crisis, as the new COVID-19 subject lines had a higher chance to pique victims' interest.
Currently, Microsoft says that COVID-19-themed malware attacks have gone down, but they are still higher than what the company saw in early February when the attacks started, so they haven't died out for good just yet.
However, going forward, Microsoft believes they'll persist as long as COVID-19 persists.
Nevertheless, Microsoft says COVID-19 is just an outlier in the general threat landscape, where most attacks continue to be typical phishing and identity compromise patterns.