LockerGoga bug crashes ransomware before encrypting files

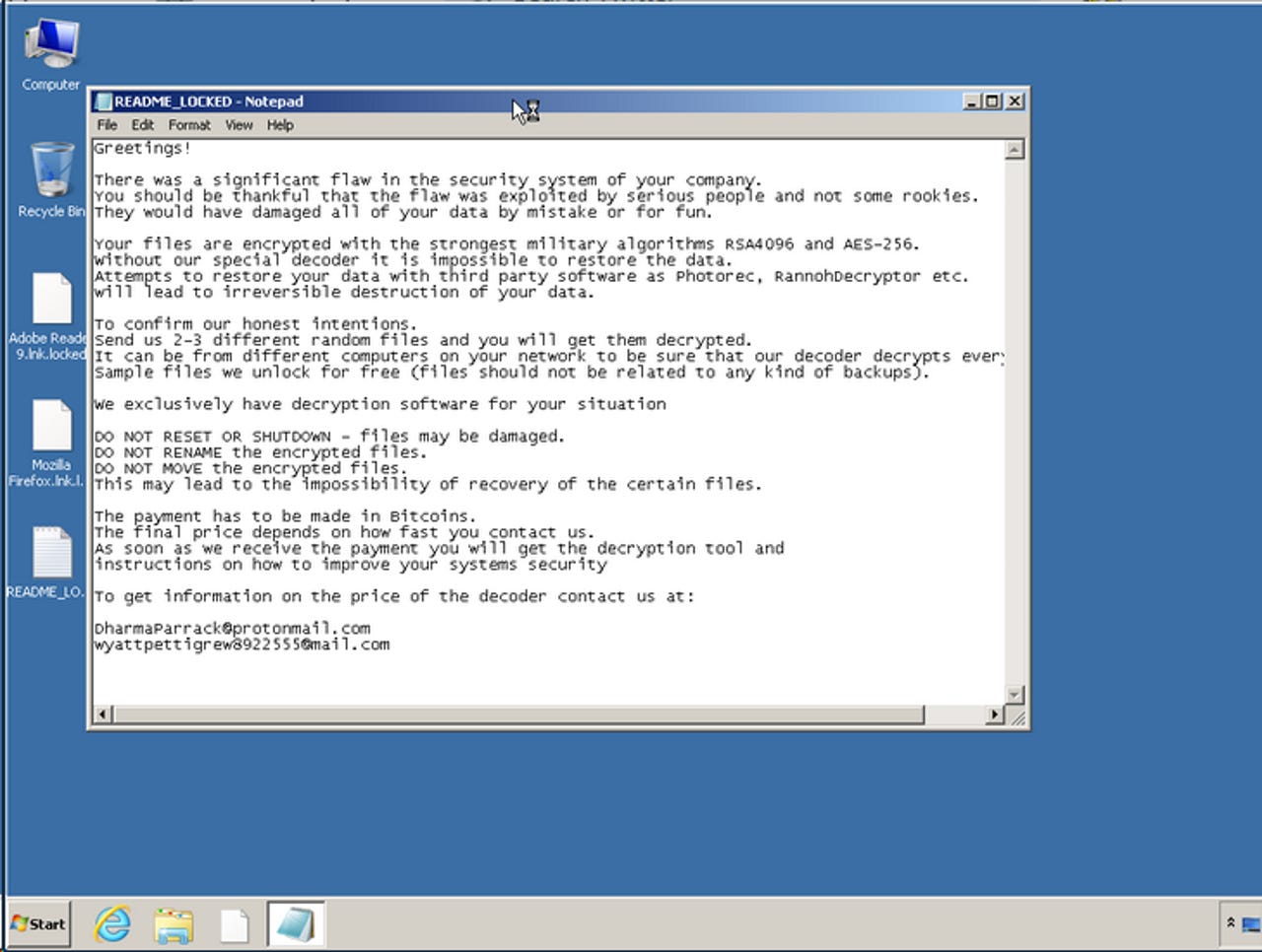
LockerGoga, the ransomware that hit Norsk Hydro and two US chemical companies over the past month, contains a bug in its code that may allow victims to "vaccinate" their PCs and crash the ransomware before it encrypts any local files.
Security
The bug, discovered by security researchers at Alert Logic, is located in a LockerGoga subroutine that executes before the encryption process begins.
The subroutine is a basic scan of all files on the victim's system, so the ransomware knows what files to encrypt and what to skip.
Alert Logic researchers say that if LockerGoga encounters an LNK (shortcut) file that contains an invalid path, the ransomware's process crashes without performing the subsequent encryption.
"We have identified two conditions for the '.lnk' file which would allow it to halt the ransomware in its tracks," the Alert Logic team said. "The '.lnk' file has been crafted to contain an invalid network path. The '.lnk' file has no associated RPC endpoint."
This trick may allow antivirus vendors to create what they call a "vaccine" --an app that creates malformed LNK files on users' computers that prevent LockerGoga from running.
However, this bug only offers temporary relief. The LockerGoga ransomware group is also bound to found out about it and patch it in a future version.
Two new LockerGoga victims emerge
LockerGoga is one of today's most dangerous ransomware strains. For the past three months, the ransomware has been deployed as part of highly targeted attacks against high-profile targets.
Hackers breach large companies, and after they gain access to internal networks, they deploy LockerGoga to as many workstations as they can for maximum damage.
French engineering firm Altran, Norwegian aluminum provider Norsk Hydro, and two US chemical firms, Hexion and Momentive, have reported infections so far --with news of the last two companies being hit emerging over the weekend.
While Norsk Hydro said it wouldn't pay the ransom and instead restore infected computers from old backups, things haven't been rosy at Momentive.
The company is said to have ordered new computers to replace the ones encrypted by LockerGoga, according to a Motherboard report citing an employee.
The 15 top malware threats facing you and your organisation
More ransomware coverage:
- Georgia county pays a whopping $400,000 to get rid of a ransomware infection
- Ransomware: An executive guide to one of the biggest menaces on the web
- PewDiePie fans keep making junk ransomware
- Aluminum producer switches to manual operations after ransomware infection
- Police Federation hit by ransomware attack
- Norsk Hydro will not pay ransom demand and will restore from backups
- New ransomware demands payment over WeChat Pay in China CNET
- Ransomware: A cheat sheet for professionals TechRepublic