Malicious Counter-Strike 1.6 servers used zero-days to infect users with malware

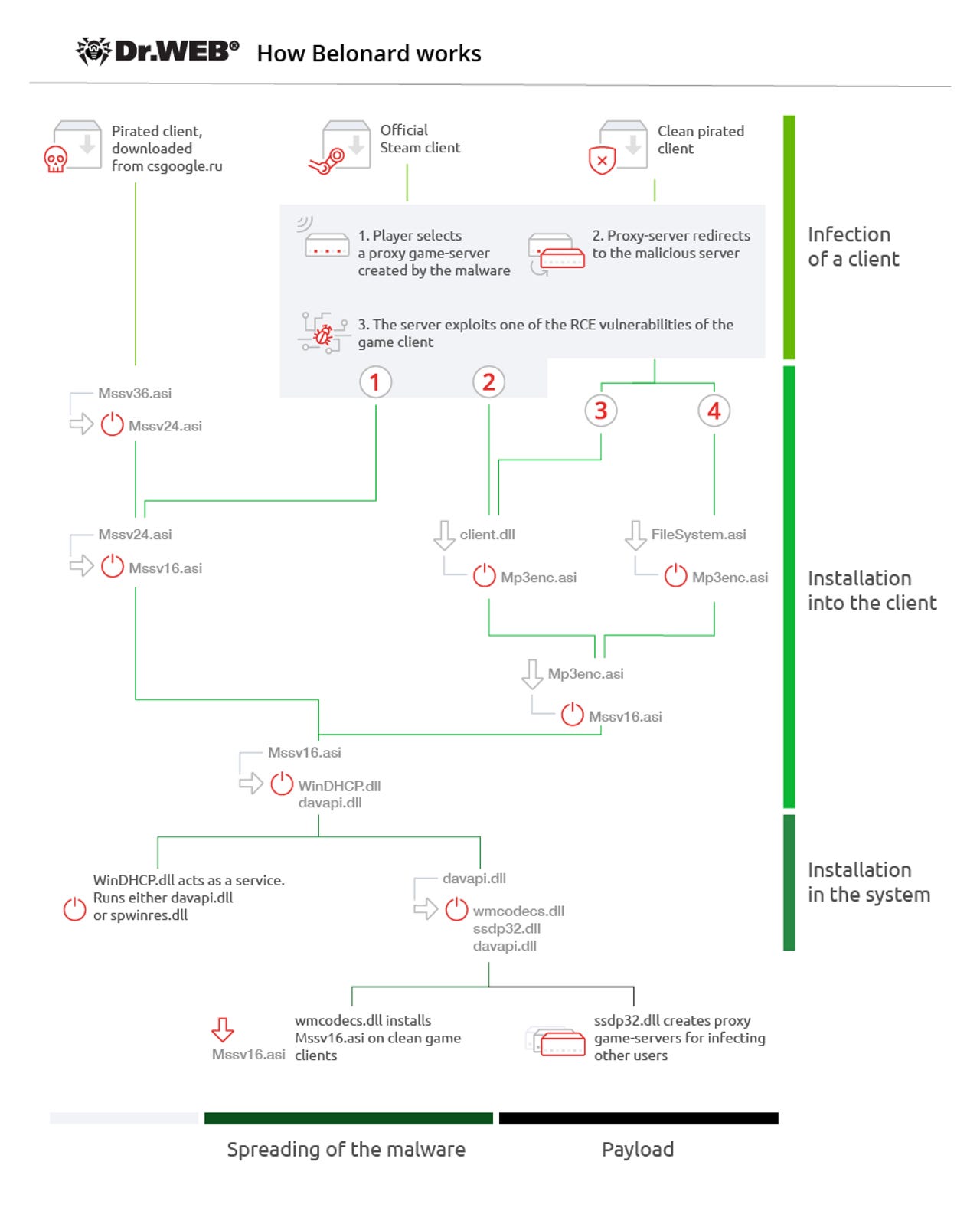
Security researchers have discovered a network of malicious Counter-Strike 1.6 multiplayer servers that exploited remote code execution (RCE) vulnerabilities in users' gaming clients to infect them with a new malware strain named Belonard.
The network has been shut down, researchers from Russian antivirus firm Dr.Web said in a report published on Monday.
The entire operation relied on proxy multiplayer servers that enticed users to connect to them because of low ping values.
When CS1.6 gamers connected to these proxy servers, they'd be redirected to malicious ones that used one of four RCEs (two in the official CS1.6 game and two in a pirated version) to execute code and plant the Belonard malware on their PCs.
The computers infected with Belonard were all added to a botnet-like structure.
Belonard would promote ads and CS1.6 servers for a fee
According to Dr. Web security researcher Ivan Korolev, the person behind the botnet would then use the Belonard malware to make modifications to users' CS1.6 clients and show ads inside users' games.
"When a player starts the game, their nickname will change to the address of the website where an infected game client can be downloaded, while the game menu will show a link to the VKontakte CS 1.6 community with more than 11,500 subscribers," Korolev said.
But above all, the trojan was primarily used to promote legitimate CS1.6 multiplayer servers by adding them to the users' available server list, which the Belonard developer would do for a fee.
Belonard victims would also help infect others users
To make sure that the Belonard botnet grew and remained active, the malware's author also had another trick down their sleeve.
According to Korolev, the Belonard malware would also create proxy servers running on users' computers.
These servers would then appear in the main CS1.6 multiplayer server list, which other users would see and connect, thinking they were legitimate servers.
However, these proxy servers would redirect gamers to malicious servers hosting the four RCEs, infecting new gamers, and boosting the Belonard botnet's ranks.
According to Korolev, the Belonard network of proxy servers grew to reach 1,951 servers, which accounted for 39 percent of all the CS1.6 multiplayer servers available at the time.
The Dr.Web researcher says they worked with the REG.ru domain registrar to take down all the domain names that the Belonard crew was using to operate their botnet.
After taking over the domains, Dr.Web said that 127 game clients tried to connect to the sinkholed domain, but the number of infected hosts is most likely much larger.
Korolev told ZDNet that he notified Valve, CS1.6's maker, about the two zero-days. The company promised a patch, but declined to say when.
According to Korolev, users can recognize Belonard's proxy servers because of a bug in its code that displayed the server game type as "Counter-Strike 1," "Counter-Strike 2," or ""Counter-Strike 3" instead of the standard "Counter-Strike 1.6."
Photos: Retro computer games that Eastern Europe played as Iron Curtain fell
More vulnerability reports:
- Apple, Google, GoDaddy misissued TLS certificates with weak serial numbers
- Microsoft March Patch Tuesday comes with fixes for two Windows zero-days
- Google: Chrome zero-day was used together with a Windows 7 zero-day
- WDS bug lets hackers hijack Windows Servers via malformed TFTP packets
- Vulnerability in Swiss e-voting system could have led to vote alterations
- Cisco tells Nexus switch owners to disable POAP feature for security reasons
- DJI fixes vulnerability that let potential hackers spy on drones CNET
- Top 10 app vulnerabilities: Unpatched plugins and extensions dominate TechRepublic