Microsoft details the most clever phishing techniques it saw in 2019

Earlier this month, Microsoft released a report on this year's malware and cyber-security trends. Among the few trends highlighted in the report was that phishing was one of the few attack vectors that saw a rise in activity over the past two years.
Microsoft said that phishing attempts grew from under 0.2% in January 2018 to around 0.6% in October 2019, where 0.6% represented the percentage of phishing emails detected out of the total volume of emails the company analyzed.
While phishing attacks increased, the number of ransomware, crypto-mining, and other malware infections went down, the company said at the time.
In a blog post published today, the Redmond-based tech giant reviewed three of the more clever phishing attacks it seen this year.
Hijacking search results
The first is a multi-layered malware operation through which a criminal gang poisoned Google search results. The scheme went as follows:
- Crooks funneled web traffic hijacked from legitimate sites to websites they controlled
- The domains became the top Google search result for very specific terms
- Phishers sent emails to victims linking the Google search result for that specific term
- If the victim clicked the Google link, and then the top result, they'd land on an attacker-controlled website
- This website would then redirect the user to a phishing page
One might think that altering Google search results takes a gigantic amount of effort, but this was actually pretty easy, as attackers didn't target high-traffic keywords, but instead focused on gibberish like "hOJoXatrCPy."
Furthermore, Microsoft said "the campaign was made even stealthier by its use of location-specific search results."
"When accessed by users in Europe, the phishing URL led to the redirector website c77684gq[.]beget[.]tech, and eventually to the phishing page. Outside Europe, the same URL returned no search results," the company said.
Abusing 404 error pages
Another clever trick used by phishers this year was first spotted in a phishing campaign Microsoft detected back in August and documented in this Twitter thread.
The 404 Not Found page tells you that you’ve hit a broken or dead link – except when it doesn’t. Phishers are using malicious custom 404 pages to serve phishing sites. A phishing campaign targeting Microsoft uses such technique, giving phishers virtually unlimited phishing URLs.
— Microsoft Security Intelligence (@MsftSecIntel) August 13, 2019
This campaign is deviously clever.
While most phishing emails include a link to the phishing URL they want to lure users on, for this campaign, attackers included links that pointed to non-existent pages.
When Microsoft's security systems would scan the link, they'd receive a 404 error back (because the link didn't exist), and Microsoft would deem the link safe.
However, if a real user accessed the URL, the phishing site would detect the user and redirect them to an actual phishing page instead of the server's standard 404 error page.
Microsoft said that when this trick was coupled with techniques like subdomain generation algorithms and changing the main domain at regular intervals, attackers could generate "virtually unlimited phishing URLs."
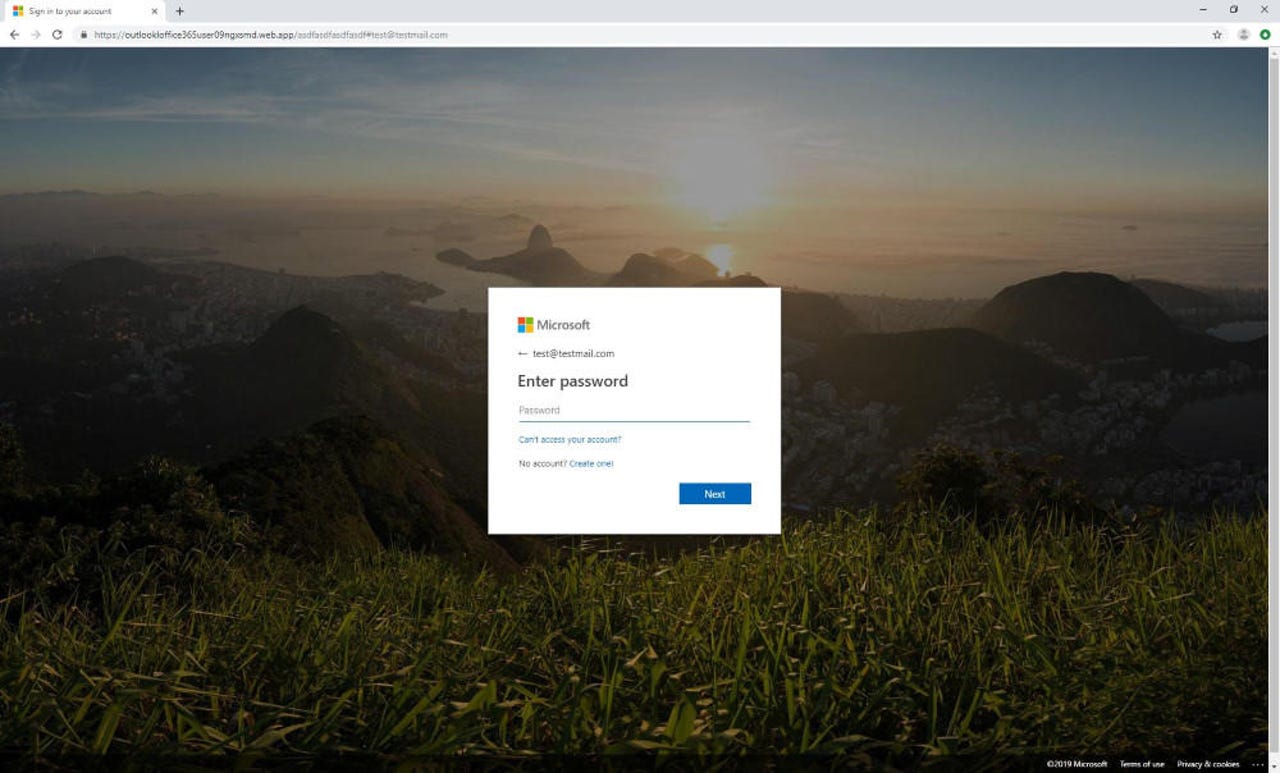
MitM-based phishing
A third phishing trick that Microsoft wanted to highlight as a clever phishing attack this year was one that made use of a man-in-the-middle (MitM) server. Microsoft explains:
"One particular phishing campaign in 2019 took impersonation to the next level. Instead of attackers copying elements from the spoofed legitimate website, a man-in-the-middle component captured company-specific information like logos, banners, text, and background images from Microsoft's rendering site. [...] The result was the exact same experience as the legitimate sign-in page, which could significantly reduce suspicion."
This MitM-based technique isn't perfect, though, as the phishing site's URL is still visible in the address bar, just like on any other phishing site.
This means that even if users could be tricked by the perfectly-looking login page, they can avoid disasters by closely inspecting the page's URL.