Microsoft's Windows warning: Hackers hijacked software updater with in-memory malware

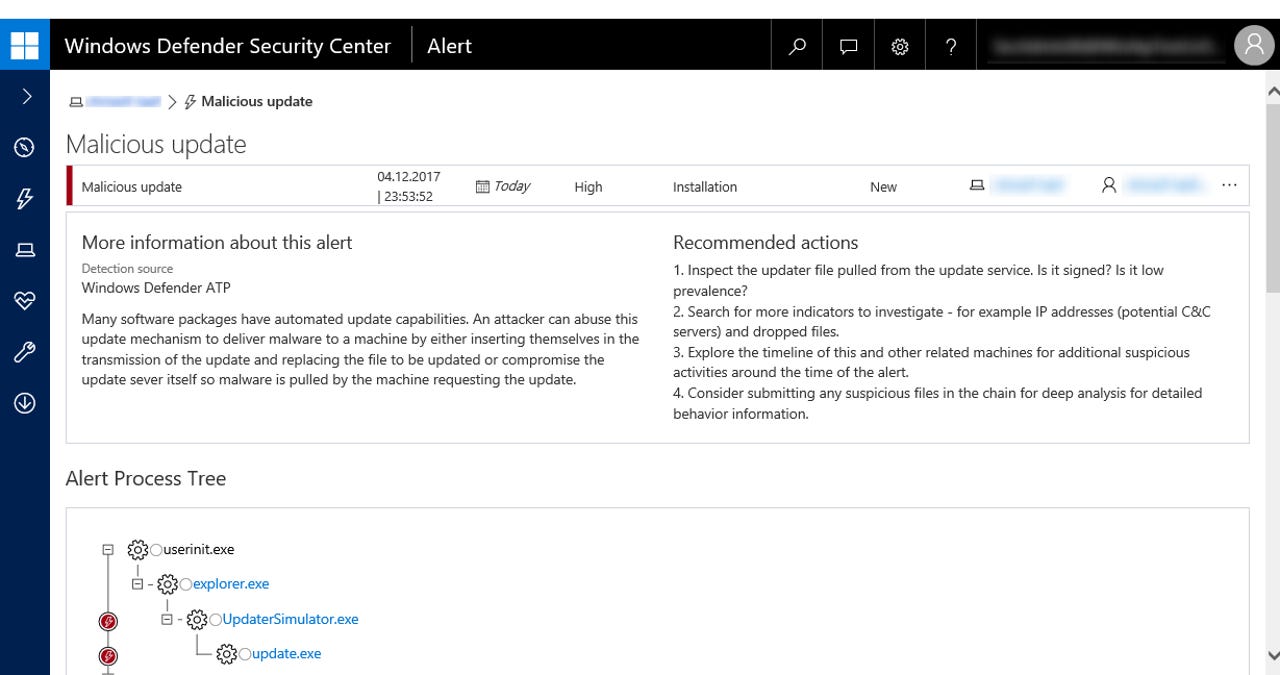
Microsoft has shown how Windows Defender ATP detected anomalous updater behavior.
Microsoft is warning software vendors to protect their updater processes after discovering a "well-planned, finely orchestrated" attack that hijacked an unnamed editing tool's software supply chain.
As Microsoft's threat response group explains, the attackers used the update mechanism of a popular but unnamed piece of editing software to gain a foothold in several high-profile technology and financial organizations. The software vendor itself was also under attack, it says.
The espionage campaign, dubbed WilySupply by Microsoft, is likely to be financially motivated and target updaters to reach mostly finance and payment-industry firms.
In this case, they used the updater to deliver an "unsigned, low-prevalence executable" before scanning the victim's network and establishing remote access.
Attacking the update process of trusted software is a nifty side door for attackers, since users rely on the mechanism to receive valid updates and patches.
Microsoft notes the same technique has been used in a number of attacks, such as a 2013 breach of several South Korean organizations via a malicious version of an installer from storage service SimDisk.
Attackers have the added benefit of access to free open-source pen-testing tools like Evil Grade, which helps exploit faulty update implementations to inject bogus software updates. As Microsoft notes, WilySupply did just this, shielding the attackers from attribution through unique tactics and tools.
The other pen-testing tool the attackers used was Meterpreter, the in-memory component of the Metaplsoit framework.
"The downloaded executable turned out to be a malicious binary that launched PowerShell scripts bundled with the Meterpreter reverse shell, which granted the remote attacker silent control. The binary is detected by Microsoft as Rivit," Microsoft notes.
Despite the reliance on commodity tools, Microsoft notes a few traits typical of advanced attackers, including the use of self-destructing initial binary, and a memory-only or fileless payload to evade antivirus detection.
Security firm Kaspersky in February reported a rise of in-memory malware attacks on banks across the globe, with attackers using Meterpreter and standard Windows utilities to carry out the attacks. As the company noted, the URL responsible for downloading Meterpreter was "adobeupdates.sytes[.]net".
Microsoft traced the source of infections at customer sites to the compromised updater with Windows Defender Advanced Threat Protection (ATP) console, its Windows 10 security feature for containing and investigating malware outbreaks.
"By utilizing the timeline and process-tree views in the Windows Defender ATP console, we were able to identify the process responsible for the malicious activities and pinpoint exactly when they occurred. We traced these activities to an updater for the editing tool," says Microsoft.
"Forensic examination of the Temp folder on the affected machine pointed us to a legitimate third-party updater running as service. The updater downloaded an unsigned, low-prevalence executable right before malicious activity was observed."
Read more on Windows security
- Latest Windows 10 'Redstone 3' test build adds container-based browser isolation
- Microsoft finally fixes 'critical' Windows security flaw after patch delay
- Microsoft fixes 'critical' Office Word security flaw under active attack
- Users tell Microsoft to scrap 'pain in butt' Security Update Guide, bring back old bulletins