Potential data breaches make up 14% of Commonwealth incidents reported to ACSC

The first installation of a new report into Canberra's cyber readiness has been tabled, with The Commonwealth Cyber Security Posture in 2019 prepared by the Australian Signals Directorate (ASD).
During the last year, the Australian Cyber Security Centre (ACSC) responded to 427 cyber incidents against Commonwealth entities, 65% of which were self-reported, and the rest were picked up through ACSC investigations, reports from third parties, and analysis of a variety of classified and open-source material, the report said.
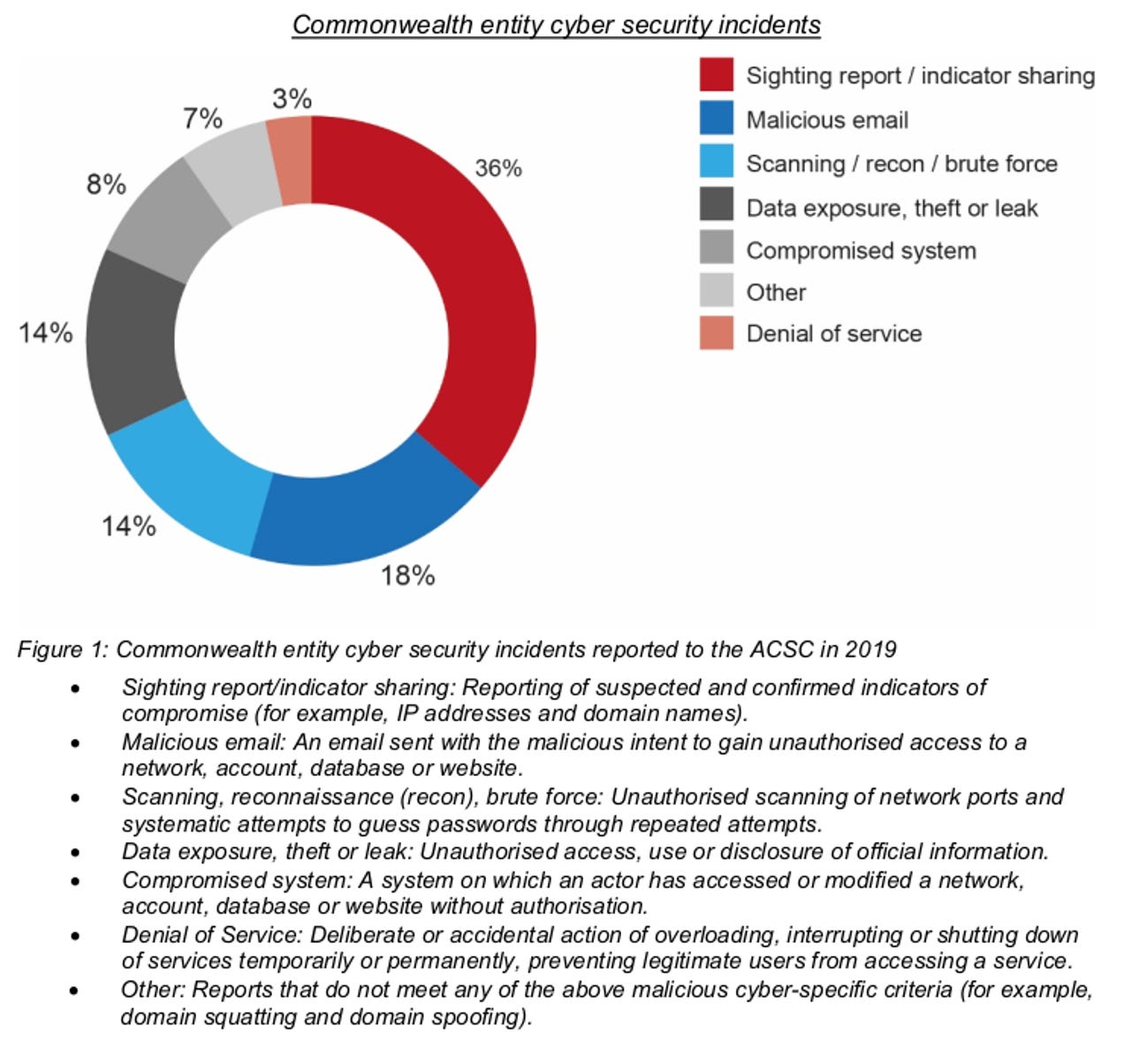
Breaking down the incidents, the report said 36% were sighting reports and indications of compromise; 18% were sparked by malicious emails; 14% were classed as data exposure, theft, or leak; a further 14% were due to network scanning or brute force attacks; 8% involved a potentially compromised system; 3% were classed as denial of service; and 7% were placed in the other category.
One of the incidents ACSC looked into was the February 2019 hack of the Australian Parliament network, which later encompassed the nation's political party networks as well.
That attack was later pinned on a sophisticated state actor.
"The activity was detected by security and intelligence agencies who rapidly responded, mitigating the threat and remediating the affected systems," the report said.
Read more: Aussie Parliament's sad cyber espionage saga is a salient lesson for others
The report states that the Cyber Uplift program had made improvements to the security of all Commonwealth entities, but the end result was still lacking when compared to the Essential Eight criteria.
"Levels of cybersecurity maturity vary across the Australian government. While the cybersecurity posture of Commonwealth entities continues to improve, entities remain vulnerable to cyber threats," the report said.
"Additional work is required for Commonwealth entities to reach a mature and resilient cybersecurity posture that meets the evolving threat environment."
Before the uplift, a number of agencies previously had inadequate visibility of systems and data holdings, had obsolete and unsupported operating systems and applications, needed to upgrade hardware to more easily put in security controls, misunderstood and inconsistently applied the Essential Eight, and had ineffective risk management practices.
"In 2018, most respondents to the ACSC Cyber Security Survey were unable to provide data on cybersecurity events or incidents observed in their entity's environment," the report said.
"In 2019, the majority of respondents reported experiencing hundreds of cybersecurity events or incidents per day, with only 10% unable to provide data."
In the course of its 2018-19 Protective Security Policy Framework reporting, ASD said 13% of non-corporate Commonwealth entities had the lowest rating of ad-hoc, 60% were a step above at the rank of developing, 24% were self-reported as managing, and only 2% said they had the highest rating of embedded.
Against this, only 67% of non-corporate Commonwealth entities said they needed to improve against the Top 4 part of the Essential Eight, which consists of application whitelisting, patching applications, restricting administrative privileges, and patching operating systems.
An example of the increasing posture was given in the increased use of the Sender Policy Framework (SPF) and Domain-based Message Authentication, Reporting and Conformance (DMARC) records to fight against spam and malicious emails.
On 19 December 2018, only 4.5% of Commonwealth entities had implemented SPF, while 22.5% had DMARC records. By the start of February 2020, those numbers had jumped to 40.5% and 55.5%, respectively.
During the uplift, ACSC began a trial of 10,000 host-based sensors with two unnamed entities.
"These sensors provided the ACSC and the entities themselves with data to identify malicious cyber activities, generate threat indicators, and contribute to the development of mitigation strategies," the report said.
"In addition, the Digital Transformation Agency developed a suite of Microsoft Office 365 productivity tools, including secure desktops and workspaces, with enhanced security arrangements."
The report also said Australia's Cyber Incident Management Arrangements were activated three times in 2019: Once for the parliamentary hack, another time when BlueKeep exploit surfaced, and the final time for when Emotet botnet became active.
The ASD pointed out that the report was only based on information available to it and the ACSC.
"The findings in this Report are, therefore, limited to information obtained through the ACSC Cyber Security Survey and the 2018-19 PSPF maturity reporting, combined with the results of the whole-of-government Cyber Uplift for Federal Government Systems and for the 2019 Federal Election Budget measure (Cyber Uplift) and cybersecurity incident reporting and investigations," it said.
"Some of the information is self-reported and, therefore, cannot be independently verified."
Shadow Assistant Minister for Cyber Security Tim Watts said the report was an indictment of the Abbott, Turnbull, and Morrison governments over the past seven years, adding that the report provided no transparency or accountability for the failures to implement the Essential Eight.
"Today's report supposedly implements the Morrison government's commitment to provide the Parliament with 'increased transparency in cybersecurity reporting'," he said.
"Despite this, all data provided in the report is 'anonymised and provided in aggregate'.
"The Australian public has no way to hold the Ministers overseeing Commonwealth agencies, who have failed to implement these basic cybersecurity measures, accountable."
Updated at 16:59 pm AEST, 14 April 2020: Added Labor comments.
Related Coverage
- Australia on the cyber offence to bring down COVID-19 scammers
- Labor wonders how Australia would handle a cyber-corona outbreak
- Australian government advice on how to avoid coronavirus-related scams and cyber threats
- Department of Parliamentary Services gives itself cyber tick of approval
- Australian cyber policymakers to face Audit Office probe