PyPI, GitLab dealing with spam attacks

Spammers have inundated the Python Package Index (PyPI) portal and the GitLab source code hosting website with garbage content, flooding both with ads for shady sites and services.
The attacks were unrelated to each other.
PyPI flooded with more than 10,000 listings
The biggest of the two attacks took place on PyPI, the official package repository for the Python programming language, and a website that hosts tens of thousands of Python libraries.
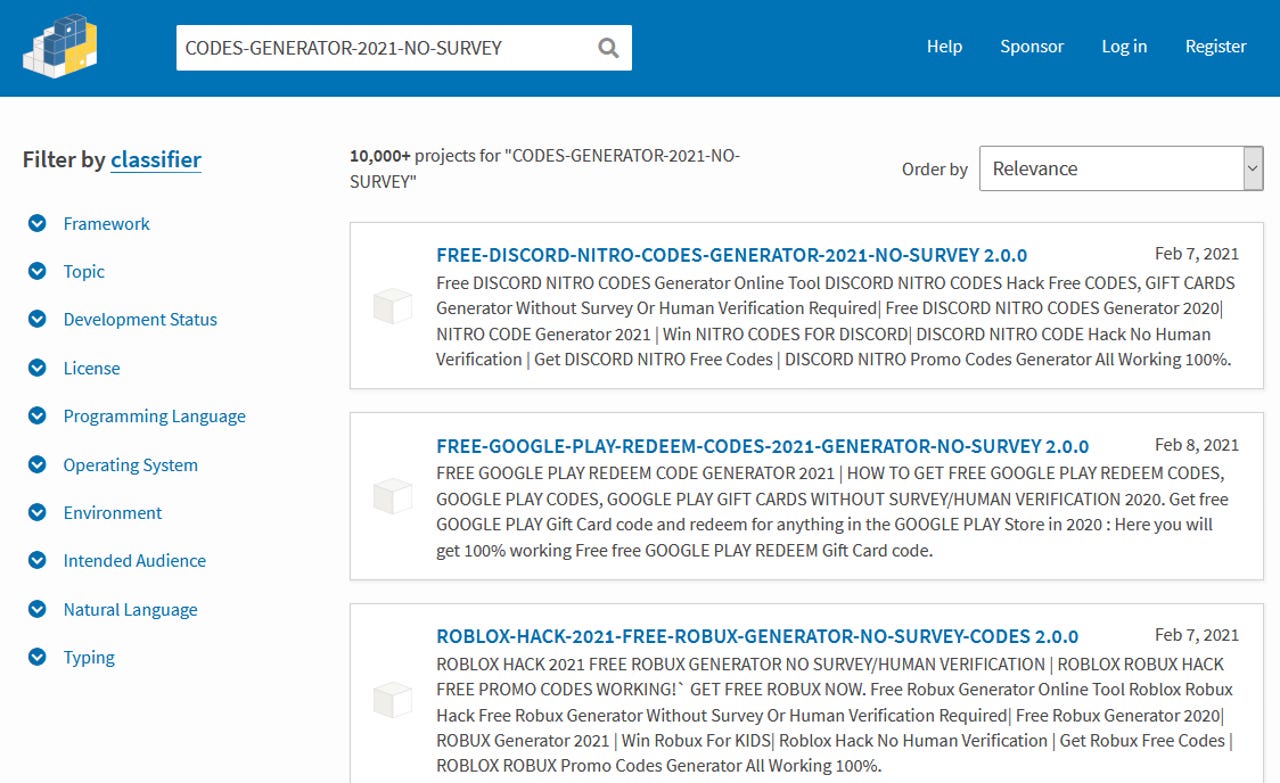
For the past month, spammers have been abusing the fact that anyone can create entries on the PyPI website to generate pages for non-existent Python libraries that basically served as giant SEO ads for various shady sites.
The pages usually contained a soup of search-engine-friendly keywords for various topics, ranging from gaming to porn and from movie streaming to giveaways, and a shortened link at the bottom, often leading to a site trying to obtain payment card data, according to ZDNet's tests.
I was checking on the #falco malware pipeline @snaveen @jw_sec and I have been working on in @theopenssf, and noticed some weird stuff being uploaded to PyPI: https://t.co/XUJNzIc8qL
— Dan Lorenc (@lorenc_dan) February 7, 2021
There are a bunch of these:https://t.co/pzJWprjlxr
Is it just some SEO play?
TIL that pypi (the #python package manager) has a *ton* of free movie spamhttps://t.co/fCQYXl1gTq
— Fernando (@fmc_sea) January 14, 2021
Reached out comment earlier today, the PyPI team said it was aware of the SEO spam flood.
"Our admins are working to address the spam," Ewa Jodlowska, Executive Director of the Python Software Foundation, told ZDNet in an email on Monday.
"By the nature of pypi.org, anyone can publish to it so it is relatively common," she added.
Shortly after the exec's email, many of the spam listings created on the PyPI portal began to be removed, an operation that appears to be still underway.
GitLab project owners spammed via email
But while the spam attack on PyPI appears to have been going on for at least a month, a new one was detected at GitLab, a website that allows developers and companies to host and sync work on source code repositories.
An unknown threat actor appears to have spammed the Issues Tracker for thousands of GitLab projects with spam content on Sunday and Monday that, each, triggered an email to account holders. Just like the spam on PyPI, these comments also redirected users to shady sites.
Spamming source code repositories appears to be a new tactic for spam groups, which in previous years have usually focused on blogs, forums, and news portals, which have often seen their comment sections flooded with shady links.
GitLab was obviously not prepared for this kind of attack because its email system was overwhelmed and slowed down, with legitimate emails being delayed and queued, according to an incident status report the company published on Monday.
We confirmed that mail latency was caused by a user’s spam attack. Mitigation is in progress, as we drain the offending job processing queues. https://t.co/FRkUs3EQOU
— GitLab.com Status (@gitlabstatus) February 8, 2021
Things are back to normal now, but both incidents show the dangers of leaving systems open and unprotected on the internet.
While spam is not a sexy attack vector, many companies will often fail to secure servers, web apps, and subdomains and will often have these resources abused to either host or participate in spam attacks.
For example, Microsoft, one year later, still has a problem with spam groups hijacking subdomains on its official microsoft.com site to host shady content.