Russian malware controls hiding in plain sight -- on Britney Spears' Instagram page

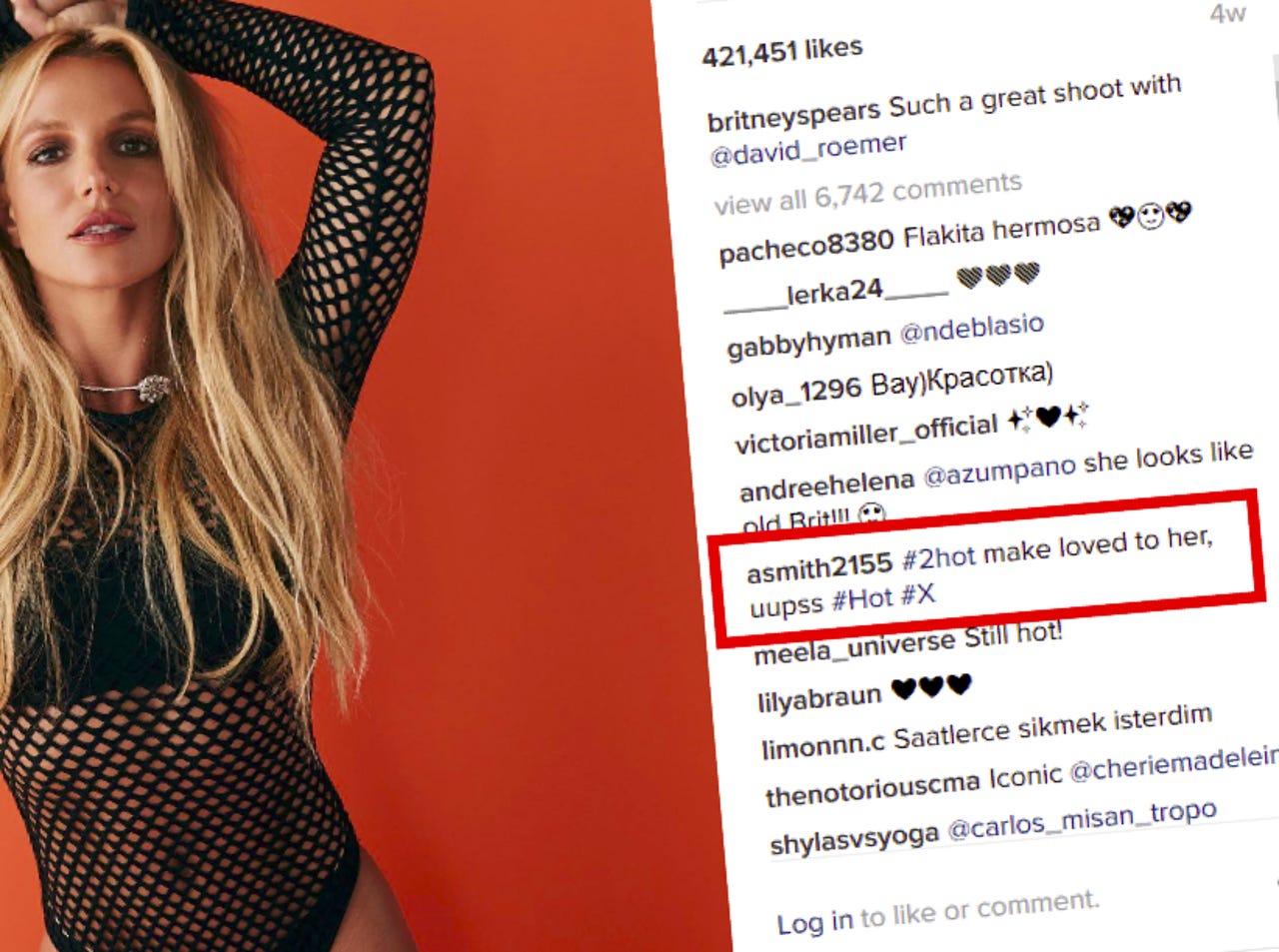
A notorious hacking group is using a novel (albeit not new) approach to commanding and controlling malware it uses to launch attacks against governments and militaries -- by leaving specially crafted comments on Britney Spears' Instagram account.
Security researchers at Eset found that the hacking group, known as Turla, is leveraging recently discovered backdoor found in a fake Firefox extension by leaving social media comments for everyone to see. The comments, left on the Instagram account, may appear benign to most people, but are crafted in such a way that allows the malware to learn the location of the roving command server without rousing suspicion.
Security
Once the comment is left, the backdoored extension knows where to look on the internet to look for instructions of what to do next -- such as to deliver ransomware or steal passwords, for example.
This is the latest hacking endeavor of Turla, a decade-old advanced persistent threat group thought to be associated with Russian hackers, with a penchant for targeting foreign embassies. To date, the group has infected hundreds of networks systems in the past few years across dozens of countries, including China, Vietnam, the US -- and even Russia.
But the group was faced with a challenge. In order to avoid detection, the command server can't stay in one spot for too long, but the malware still needs to know where to find it. Rather than hard-coding the address of the command server into the malware, the extension will calculate the address of the command server using a formula.
The researchers explained:
"The extension uses a bit.ly URL to reach its [server], but the URL path is nowhere to be found in the extension code. In fact, it will obtain this path by using comments posted on a specific Instagram post," the researchers said.
"The one that was used in the analyzed sample was a comment about a photo posted to the Britney Spears official Instagram account," they added. "The extension will look at each photo's comment and will compute a custom hash value."
In other words, the malware looks for a particular unsuspecting comment on an Instagram post, which when converted to a cryptographic hash, can be converted into the web address where the command server is located.
"The fact that the Turla actors are using social media as a way to obtain its [command servers] is quite interesting," the researchers said. "This behavior has already been observed in the past by other threat crews such as the Dukes."
The researchers added that it makes it difficult to spot, firstly because the traffic looks like anybody else's, and secondly because of the flexibility of changing the address to the command server, and erasing any trace of it.
At the time of initial publication, the bit.ly link had just 17 clicks, which the researchers say "might indicate that it was only a test run."
"While we believe this to be some type of test, the next version of the extension -- if there is one -- is likely to be very different. There are several APIs that are used by the extension that will disappear in future versions of Firefox," the researchers said.