Secure ripping from "episodic DVDs" described in just-published Microsoft patent app

A major new Microsoft Patent application entitled DVD identification and managed copy authorization describes and illustrates a secure manner in which DVDs could be enabled for "ripping" of selected sections of media.
In other words, and as Paragraph 44 of this app describes:
For example, the use of Chapter Information enables specific television programming episodes from an episodic DVD to be identified and then copied using a managed copy process.
Readers, let us jump into this one by hitting this Patent's Abstract:
A "managed copy" capability is provided that is both sanctioned and supervised by a service provider so that multimedia content distributed on optical media such as DVD can be copied and used by a client in a controlled manner.
In an illustrative example, a content provider generates a fingerprint using heuristics and/or other data that uniquely identifies a multimedia release, like a feature film, as being authorized for copying according to defined usage rules. A managed copy service authorizes the client to make a copy of a source DVD if that source is found to match a stored fingerprint.
An identification response, which may include encoding parameters and usage rules, provides confirmation to the client that content on the source DVD is authorized to be copied.
The client copies content from the source to another medium in compliance with the identification response.
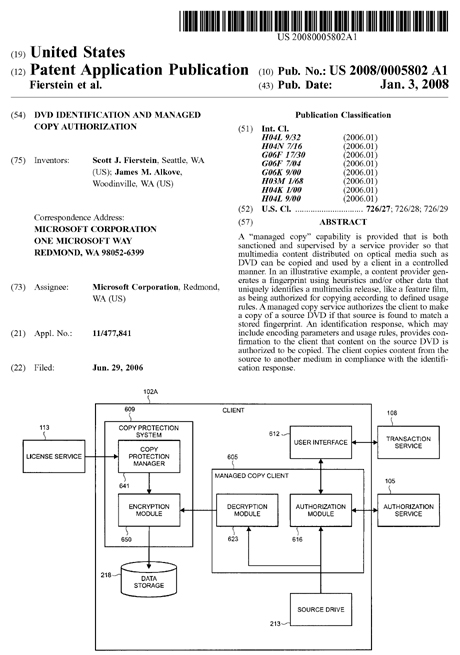
Figures 9-12 from this Patent app's literature describe what is being proposed here. I will now show you this art, and supply the descriptions for each.
FIG. 9 is a simplified pictorial illustration of a user interface window 900 that is displayed by user interface 612 (FIG. 6). In this illustrative example, user interface window is implemented using a media player application that runs on PC 102A (FIG. 2). Shown is the screen that is displayed by the media player application when the "Rip" button 902 is activated by a consumer.
User interface window 900 shows that a DVD having the feature film "The Microsoft Movie" is loaded in drive D: (i.e., the source drive 213 in FIG. 2) as indicated by reference numeral 903. An illustration 907, which typically includes DVD cover art or other graphical elements, is provided by user interface window 900. Some background information 911 is also provided.
Illustration 907 and background information 911 are examples of information that is provided from the multimedia content provider 121 (FIG. 1) to the authorization service 105 (FIG. 1) in the fingerprint 404 (FIG. 4) or response information 407 (FIG. 4). Authorization service 105 provides the information to the managed copy client 605 (FIG. 6) for display on the user interface window 900.
A plurality of DVD managed copy options are provided in user interface window 900 as drop down lists, as indicated by reference numeral 916. The number of managed copy options can vary according to specific requirements.
Not all options are necessarily made available to consumers depending on the parameters defined by the multimedia content provider 121 in the fingerprint 404. For example, the region menu option is "grayed out" in FIG. 9 which indicates that no user selection may be made.
In the illustrative example shown in FIG. 9, an activation code field 923 is provided. Alternatively, a user interface screen or set of screens (not shown) are used to implement a payment transaction where the consumer enters credit card information, or uses other types of payment options such as commercial payment services. As noted above, in some settings no transaction is required by the multimedia content provider 121.
It is contemplated that the activation code is obtained by a consumer in a variety of ways. An activation code may be included with the DVD retail packaging and used to implement a product registration or activation paradigm in which the multimedia content provider 121 is afforded an opportunity to collect for example, user data, interests, product preferences, or other pertinent demographic information to assist in preventing unlicensed copying and use of multimedia content.
Such activation paradigms are commonly implemented to reduce piracy of software. Here, the multimedia content provider 121 offers the consumer an authorization to make managed copies in exchange for the consumer's sending of the activation code. The number and quality of the copies that the user can make may be included in the specific terms of the multimedia content provider's offer among other such terms. Thus, the activation code on the retail package operates as an electronic coupon that is redeemable for one or more managed copies of the multimedia content purchased on the DVD.
Activation codes may also be distributed using traditional or electronic advertising. For example, codes entitling a consumer to make managed copies of a rented DVD may be included as part of DVD multimedia release tie-in.
In addition, the user interface screen 900 includes a link 925 that the consumer can follow to gain additional information about obtaining a managed copy activation code. Such link 925 may be provided, for example, by the URI contained in the identification response 723 as described above in the text accompanying FIG. 7.
Once the relevant DVD options 916 are selected and the managed copy activation code is entered in field 923, then the consumer is ready to invoke the methods performed by the managed copy client 605 (FIG. 6) by activating the "Rip" button 930 on user interface window 900.
Now to Figure 10.
Turning now to FIG. 10, a flowchart is provided of an illustrative method 1000 for a service to provide a managed copy service to a client. Method 1000 is capable of being performed by the elements shown in FIGS. 1-9 and described in the accompanying text.
The method starts at block 1005. At block 1012, the authorization service 105 receives fingerprint 404 from the multimedia content provider 121 that uniquely identifies a particular multimedia release such as a video, music, software or game. Fingerprint 404 is typically stored in data storage 315 along with other fingerprints associated with other multimedia release so that the authorization service 105 is able to maintain a list (i.e., a database) of all the multimedia releases that are authorized to be copied, as indicated by block 1017.
At block 1022, the authorization service 105 receives a managed copy request 715 from the authorization module 616 in the managed copy client 605. The identification of the source DVD held in source drive 213 is contained in the managed copy request 715 received by the authorization service 105.
At block 1025 the authorization service 105 attempts to authorize the managed copy request 715 from the managed copy client 605 by comparing the source DVD identification against the fingerprints 404 stored in data storage 315.
If at decision block 1030 a matching fingerprint is located and the managed copy is authorized, then control is passed to block 1043. If a matching fingerprint is not located by the authorization service 105, then the managed copy is not authorized and the managed copy process is terminated at block 1035. Illustrative method 1000 then ends at block 1039.
At block 1043, the authorization service 105 creates the identification response 723 and transmits it to the managed copy client 605. Optionally, at block 1046, the authorization service invokes a method performed by transaction service 108.
Here, a prompt for a payment or activation code is transmitted from the transaction service 108 to the user interface 612 in the managed copy client 605. This step is performed in cases when the multimedia content provider 121 is seeking the completion of a transaction prior to enabling the managed copy to be performed.
Alternatively, an offer is generated and transmitted that is more comprehensive in terms of the information provided to the consumer. Such offer is typically constructed using the information contained in the response information 407 that the multimedia content provider 121 provides to the authorization service.
The authorization service 105 provides the offer information to the transaction service 108 using the optional connection 142 shown in FIG. 1.
At block 1048 in FIG. 10, the transaction service 108 confirms receipt of the payment or activation code in the optionally utilized transaction process.
Upon the completion of any applicable transaction, then authorization service 105 completes the authorization process at block 1055 so that the managed copy client 605 is thus able to perform the managed copy in accordance with the parameters contained in the identification response 723.
At block 1057, updates are made to databases in data storage 315 in the authorization service 105 to reflect the granted authorization to the managed copy request. For example, the number of copies authorized, the extent of offers accepted by consumers, and other statistical, usage, or demographic data may be collected during the managed copy authorization process by the authorization service 105 which may then be passed back to the multimedia content provider 121, for example. Method 1000 ends at block 1062.
If you've stuck w/me all the way so far, you know Figure 11 is next. Actually that'd be Figure 11A and 11B, with combined annotation.
FIG. 11 is a flowchart of an illustrative method 1100 for implementing a managed copy process at a client. Method 1100 is capable of being performed by the elements shown in FIGS. 1-9 and described in the accompanying text. The method starts at block 1102.
At block 1107, a consumer selects a source DVD to be copied (i.e., "ripped"), typically by inserting the DVD into the source drive 213. In some applications of DVD identification and managed copy authorization, the managed copy client 605 is arranged to auto-launch upon DVD insertion.
This allows user interface 612 to expose a user interface (e.g., user interface window 900) to provide the consumer with managed copy features and options. In other applications, the managed copy functions are reachable using commands provided by an operating system operating on PC 102A or through software applications including copy utilities and media players.
At block 1112, once launched, the managed copy client 605 contacts the authorization service 105, typically through an Internet connection, and sends the managed copy request 715.
At block 1116, the managed copy client 605 receives the source DVD fingerprint from the source drive 213 and transmits the source DVD fingerprint to the authorization service 105. If the authorization service 105 does not grant authorization for the managed copy at decision block 1121, the managed copy process is terminated at block 1124. Method 1100 then ends at block 1126.
If the authorization service 105 grants authorization at decision block 1121 in FIG. 11, then control is passed to block 1129 where the authorization module 616 receives the identification response 723 from the authorization service 105. In some applications of DVD identification and managed copy authorization, the authorization service 105 supplies license information (e.g., usage rules or policies, or a DRM license such as license information 506 in FIG. 5) with the identification response that is received by the authorization module 616 in the managed copy client 605.
In this case, the managed copy client 605 is arranged to pass the license information to the copy protection system 609. In alternative arrangements, the copy protection manager 641 in copy protection system 609 receives the license information from the license service 113.
At block 1133, using the identification response, the managed copy client 605 determines whether the optionally utilized transaction is necessary. If so, then at block 1137 the managed copy client 605 displays a prompt through the user interface 612 for a payment or entry of an activation code (e.g., as shown in activation code field 923 in FIG. 9).
Alternatively, user interface 612 is configured to display a more comprehensive offer made by the authorization service 105. At block 1139, the user interface 612 transmits the transaction information or activation code to the transaction service 108. At block 1142, upon conclusion of the transaction, the managed copy client 605 receives the completed authorization from the authorization service 105.
The decryption module 623 in the managed copy client 605 in this illustrative example is arranged to both decrypt and decode encrypted multimedia content read from the source DVD in source drive 213 at block 1145. In some applications of DVD identification and managed copy authorization, the multimedia content on the source DVD in source drive 213 is encrypted using CSS copy-protection.
Alternatively, the source DVD is encrypted using other copy-protection methodologies, for example, one of AACS (Advanced Access Content System), Helix DRM, SPDC (Self-Protecting Digital Content), FairPlay, xCP (Extended Copy Protection), OpenMG, Marlin DRM, OMA (Open Mobile Alliance) DRM, Windows Media DRM, or CPRM/CPPM (Content Protection for Recordable Media and Pre-Recorded Media).
At block 1150, decryption module 1150 transmits the decrypted multimedia content to the encryption module 650 in copy protection system 609. The encryption module 650 optionally re-encrypts the multimedia content, at block 1154, responsively to the license information 506 that typically sets limits on the consumer's use of the managed copy.
The encryption methodology used in this step may be CSS, for example, or one of the alternatives listed in the description of block 1145. Encryption by encryption module 650 is optional as there may be applications of DVD identification and managed copy authorization where media content is desired by a multimedia content provider to be furnished in the clear, or perhaps with only a watermark, rather than be subject to more restrictive encryption.
In addition to optionally re-encrypting the multimedia content, the encryption module 650 includes an encoder which encodes the multimedia content into a format that is usable by the consumer's media player. Current DVDs are encoded in a manner that is compliant with the MPEG-2 (Moving Pictures Expert Group) standard.
Encryption module 650 may thus be arranged to re-encode the multimedia content using this same MPEG-2 coding scheme since many media players and portable media players can play MPEG-2 encoded video either through native support or by use of a plug-in MPEG codec (coder/decoder).
Alternatively, depending on the requirements of a specific application of DVD identification and managed copy authorization, encryption module 650 is arranged to transcode multimedia content from a first format to a second format.
That is, the client 102 is arranged so that multimedia content encoded in a first one of a variety of encoding formats is decoded by decryption module 623 and then re-encoded into a second one of the variety of encoding formats by encryption module 650.
Such transcoding may be used, for example, to optimize the encoding of the multimedia content to a particular player such as a portable media device such a handheld game, video-capable mobile phone or PDA. With both re-encoding and transcoding, the particular encoding scheme selected and the parameters used may be specified by the encoding parameters contained in the identification response 723 or license information 506.
Table 1 below lists common encoding formats that are usable in various arrangements of DVD identification and managed copy authorization. The first column in Table 1 lists the encoding format (which is also commonly referred to as a container format) and the second column lists the corresponding file extension.
TABLE-US-00001 TABLE 1 Format File Extension Advanced Streaming Format, Advanced Systems Format .asf Audio Video Interleaved .avi DivX Media Format .divx DVD Video Object .vob Quicktime .mov, .qt MPEG-2 (Moving Pictures Expert Group) .mpg, .mpeg MPEG-4 .mp4 RealVideo .rm, .ram 3GP .3gp, .3g2 Windows Media Video .wmv
At block 1158, the re-encrypted and encoded (or transcoded) multimedia content is written to a medium. In typical applications in which a PC is the client device (e.g., PC 102A in FIG. 2), the multimedia content is written to data storage such as the PC's hard disk drive for playback using a media player application running on the PC.
In other applications, the multimedia content is written to an external device such as a portable media player 232 accessed via the external device interface 225. The multimedia content is also sharable over network 238, for example.
The re-encrypted and encoded multimedia content is also writable to another optical medium such as a CD, DVD or next generation DVD format. When the client is a PC, such task is typically accomplished using multiple optical drives.
Alternatively, when the client is a consumer electronic device having multiple optical drives (e.g., consumer electronic device 102B in FIG. 3), the managed copy may be performed by reading from the source drive 313 and writing the re-encrypted and encoded multimedia content to the target drive 321. Method 1100 ends at block 1163.
When I show you Figure 12- which I am about to do- this will all start to come together for you.
FIG. 12 is a flowchart of an illustrative method 1200 for providing fingerprints and response information from a multimedia content provider to a managed copy service. Method 1200 is capable of being performed by the elements shown in FIGS. 1-9 and described in the accompanying text. The method starts at block 1205.
At block 1212, multimedia content provider 121 generates fingerprint 404 to uniquely identify a multimedia release. Fingerprint 404 is based on heuristics captured from the multimedia release and typically includes identifying information. At block 1225, multimedia content provider 121 generates response information 407 that is related to a specific fingerprint. Response information typically includes encoding parameters, usage rules, polices and/or DRM licenses.
Multimedia content provider 121 transmits the fingerprint 404 and response information 407 to the managed copy service 135 at blocks 1228 and 1232, respectively. Method 1200 ends at block 1236.
And there you have it, pretty much, anyway.