Android stalkerware detection rates surged over 2020

Android stalker and spyware detection surged by 48% over the past year, and not only do these apps invade user privacy, vendors do not appear to care about tackling vulnerabilities found in their creations.
This week, ESET researcher Lukas Stefanko released telemetry data focused on Android stalkerware detection, revealing that usage of these dubious apps began to climb in 2019 -- with a five-fold increase reported in comparison to 2018 -- and this trend continued in 2020, highlighting their ongoing popularity.
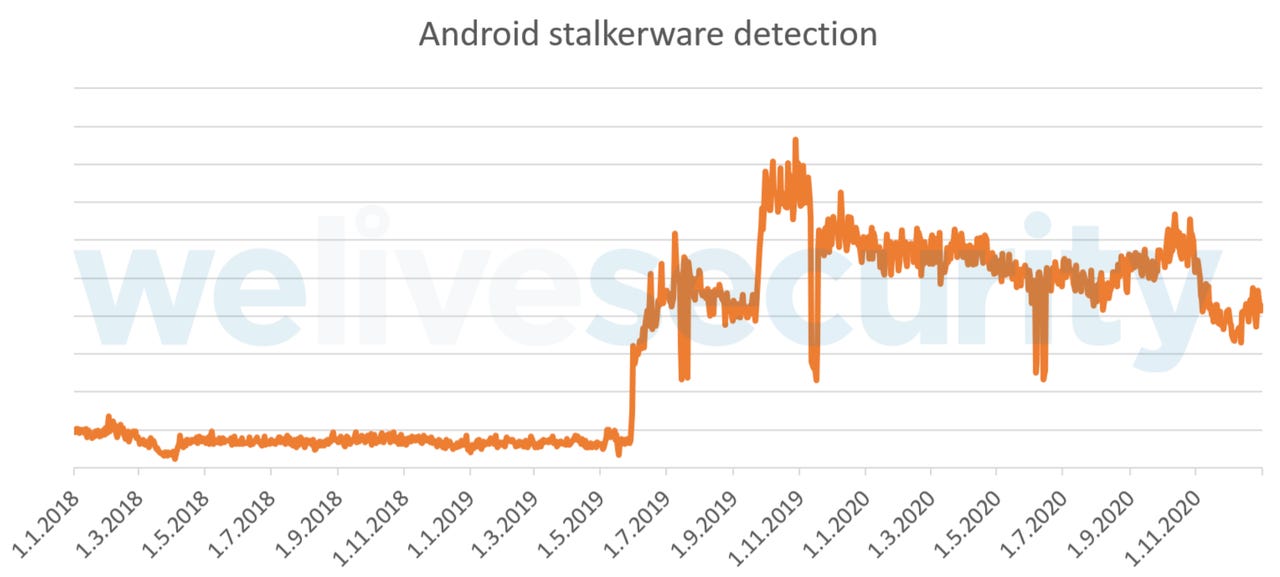
ESET's findings are corroborated by past research from Kaspersky, which found that stalkerware infections grew by 40% in 2019.
Stalkerware is a term coined to describe the most invasive types of spyware that are often paid for, and used, by people close to home rather than unknown threat actors.
These types of software can be covertly installed on a PC or mobile device and will track a user's activities in a deep violation of privacy, with data gathered including their GPS location (where available), call logs, contact lists, SMS communication, social media usage, browser history, and more.
Data harvested by these apps are then sent to an operator.
In the case of mobile stalkerware, the operator often needs to have obtained physical access to side-load the malware, and so users tend to be close family, spouses, or parents. They may also be used by businesses to monitor employees.
While many of these apps are marketed as a way to monitor children in the interest of safety, the invasive nature of these apps is generally thought to make them unethical. Just because something is marketed as a safety net for minors does not mean it cannot be used to track a spouse, for example -- and in either case, despite the age of the one being stalked, rights to privacy may be abused.
According to Stefanko, a recent analysis of stalkerware available for the Google Android mobile platform revealed many vendors tout their wares as a means to protect not only children, but also employees and women.
The vendors producing them for financial gain also do not appear to care that inherent -- and expansive -- security vulnerabilities contained in their apps are also risking 'users,' and customers, in other ways.
"If nothing else, stalkerware apps encourage clearly ethically questionable behavior, leading most mobile security solutions to flag them as undesirable or harmful," the researcher says. "However, given that these apps access, gather, store, and transmit more information than any other app their victims have installed, we were interested in how well these apps protected that amount of especially sensitive data."
In short, they didn't.
An examination of 58 Android stalkerware apps, provided by 86 vendors, revealed a total of 158 security issues (.PDF). These included the insecure transmission of sensitive data, command injection flaws, data leaks, information left on servers after accounts were deleted, and both source code and admin credentials exposure.
Not only was the victim's data mishandled in many cases, but the bugs also impacted the security of the vendors themselves and their stalker customers.
The vulnerabilities were reported to the affected vendors, but only six developers have fixed their software, seven have made promises to patch that are yet to be kept, and 44 did not respond at all to ESET's disclosure.
"The research should serve as a warning to potential future clients of stalkerware to reconsider using software against their spouses and loved ones, since not only is it unethical, but also might result in revealing the private and intimate information of their spouses and leave them at risk of cyberattacks and fraud," Stefanko commented.
Previous and related coverage
- The ultimate guide to finding and killing spyware and stalkerware on your smartphone
- Stalkerware detection rates are improving across antivirus products
- Google bans stalkerware ads
Have a tip? Get in touch securely via WhatsApp | Signal at +447713 025 499, or over at Keybase: charlie0