This Android malware hides as a System Update app to spy on you

A new, "sophisticated" Android spyware app disguising itself as a software update has been discovered by researchers.
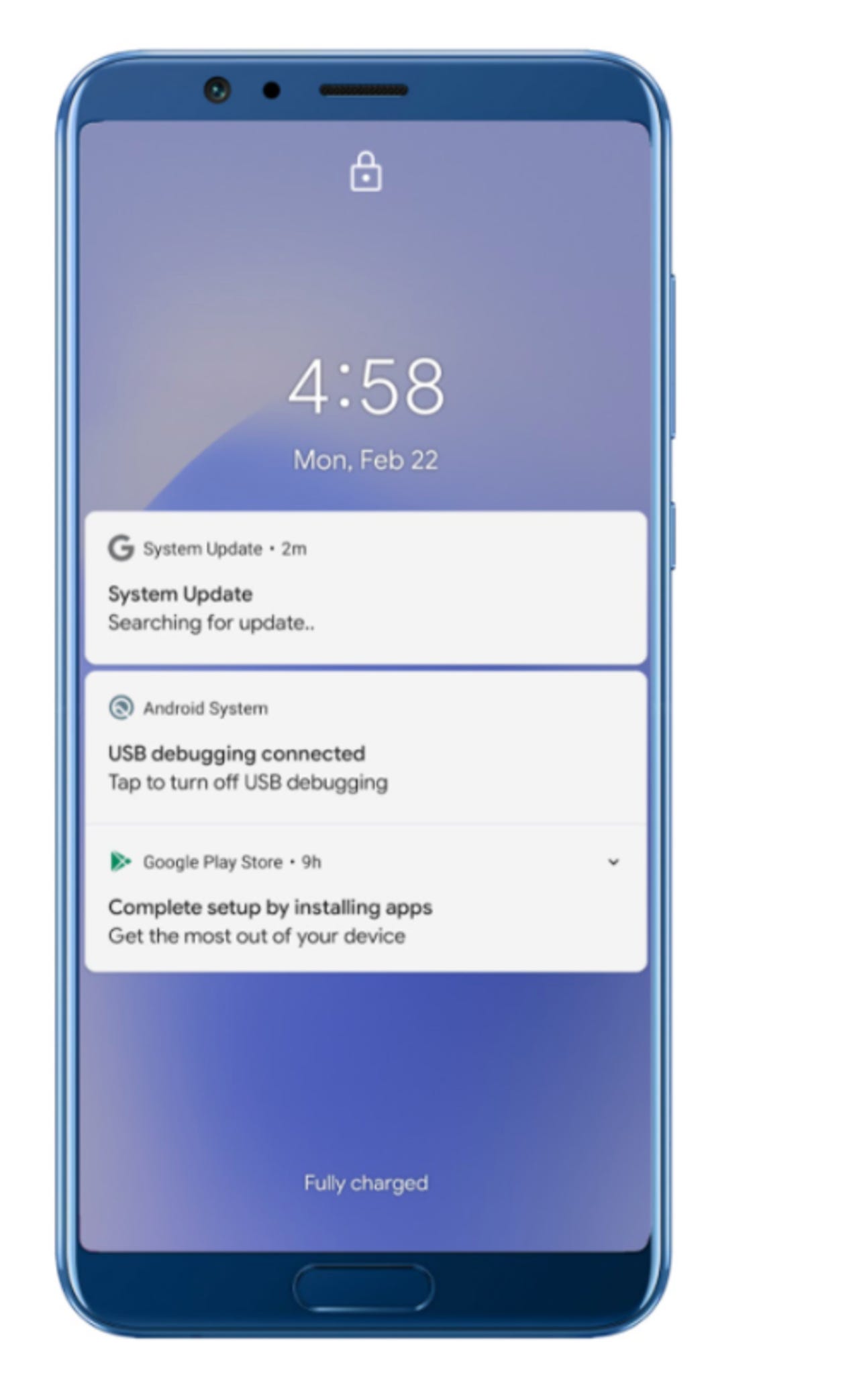
According to Zimperium zLabs, the malware masquerades as a System Update application while quietly exfiltrating user and handset data.
It should be noted that the sample app detected by the team was found on a third-party repository and not the official Google Play Store.
Once installed, the victim's device is registered with a Firebase command-and-control (C2) server used to issue commands while a separate, dedicated C2 is used to manage data theft.
The team says that data exfiltration is triggered once a condition has been met, including the addition of a new mobile contact, a new app is installed, or on receipt of an SMS message.
The malware is a Remote Access Trojan (RAT) and able to steal GPS data and SMS messages, contact lists, call logs, harvest images and video files, covertly record microphone-based audio, hijack a mobile device's camera to take photos, review browser bookmarks and histories, eavesdrop on phone calls, and steal operational information on a handset including storage statistics and lists of installed applications.
Instant messenger content is also at risk as the RAT abuses Accessibility Services to access these apps, including WhatsApp.
If the victim device has been rooted, database records can also be taken. The app can also search specifically for file types such as .pdf, .doc, .docx, .xls, and .xlsx.
Security
The RAT will also attempt to steal files from external storage. However, considering some content -- such as videos -- can be too large to steal without impacting connectivity, thumbnails alone are exfiltrated.
"When the victim is using Wi-Fi, all the stolen data from all the folders are sent to the C2, whereas when the victim is using a mobile data connection, only a specific set of data is sent to C2," the researchers note.
Limiting the use of mobile connectivity is a way to prevent users from suspecting their device has been compromised. In addition, as soon as information has been packaged up and sent to the C2, archive files are deleted in an effort to stay undetected.
To make sure only relevant and recent data is taken, the RAT's operators have imposed time limits on content -- such as the newest GPS records, which are stolen time and time again if stolen data records contain values that are over five minutes in the past. Photos, too, are set to 40 minutes timers.
Zimperium describes the malware as part of a "sophisticated spyware campaign with complex capabilities."
Earlier this month, Google pulled a number of Android apps from the Play Store that contained a dropper for banking Trojans. The utility applications, including a virtual private network (VPN) service, recorder, and barcode scanner, were used to install mRAT and AlienBot.
Previous and related coverage
- Hundreds of fleeceware apps earn dubious iOS, Android developers over $400 million
- Mimecast reveals source code theft in SolarWinds hack
- SolarWinds-linked hacking group SilverFish abuses enterprise victims for sandbox tests
Have a tip? Get in touch securely via WhatsApp | Signal at +447713 025 499, or over at Keybase: charlie0