This fake security email tries to make your PC part of a botnet

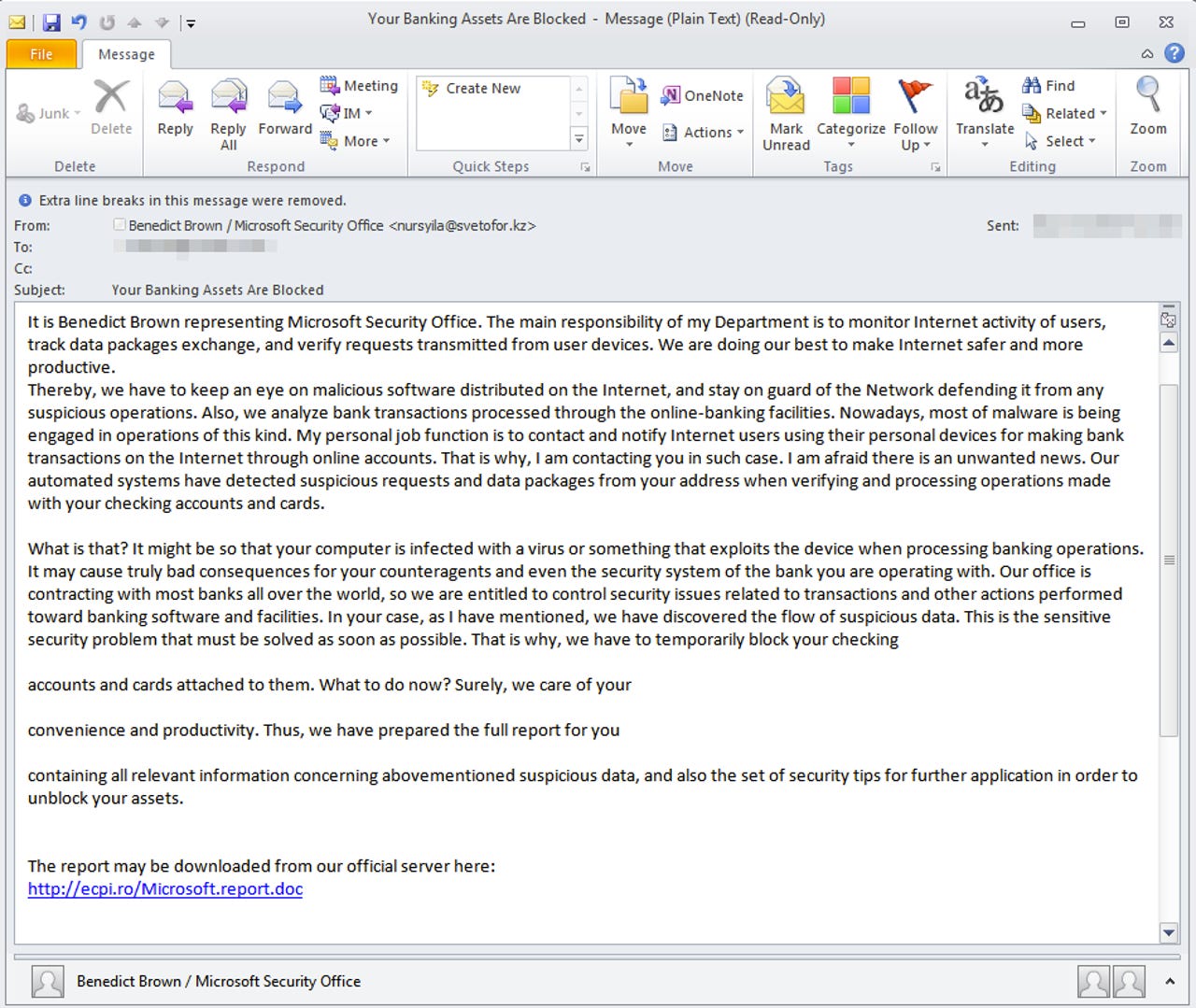
The scam emails claims to be from the fake 'Microsoft Security Office'
A new email scam campaign by cybercriminals purporting to be from 'Microsoft Security Office' is infecting its victims with Neutrino exploit kit malware. The email warns the recipients that their bank accounts are being used for suspicious activity as a result of a virus.
Neutrino bot malware can be used for various nefarious criminal means, including data theft via capturing keystrokes, form grabbing and taking screenshots, performing DDoS attacks, making spoof DNS requests, and downloading additional malware onto the infected machine. The latest Neutrino campaign has been spotted by cybersecurity researchers at Malwarebytes.
Victims are sent a spam email, claiming to be from 'Benedict Brown representing Microsoft Security Office', which falsely informs them that their banking assets have been blocked due to suspicious requests from their address.
The phony email from the non-existent department -- sent from a Kazakhstan address which doesn't even contain the word Microsoft within it -- suggests that the victim might already be infected with bank-data stealing computer virus.
At the bottom of the message, the target is invited to download what's claimed to be a report containing information about the supposed suspicious activity. If opened, the document will infect the machine with exactly the sort of malware the message warns against.
Rather than ask the victim to download an infected Word document attached to the email, they're asked to download it from what's dubbed an 'official server'. However, this is actually one of the perpetrator's malicious servers, each of which is live for a short amount of time.
Once downloaded, the infected document will ask the user to enable macros, so it can launch the malicious code which delivers Neutrino bot. The infected computer will remain in contact with a command and control server, which is used to trigger malicious activities including taking screenshots, keylogging, and recruiting the infected machine into a botnet.
Researchers note thatthe latest iteration of Neutrino appears to have undergone code improvements which enable attackers to gain more control over the execution of malicious instructions.
Neutrino is a popular tool amongst cybercriminals because it can be used by wannabes with little experience coding malicious software. The exploit kits within Neutrino target browsers and applications known to contain vulnerabilities, with previous targets including Adobe Reader, Java Runtime Environment, and Adobe Flash Player, all of which suffer from regular security troubles.
Users can attempt to avoid being exploited by Neutrino by being wary of any unexpected messages containing documents claiming to contain invoices or reports and by not enabling macros.
Read more on cybercrime
- This data-stealing Trojan is the first to also infect you with ransomware
- Spying is the new hacking: Here's how to fight back
- Infographic: How to identify and avoid phishing attacks [TechRepublic]
- Cybercrime Inc: How hacking gangs are modeling themselves on big business
- Phishing-as-a-service is making it easier than ever for hackers to steal your data