Ukrainian police arrest hacker who infected over 2,000 users with DarkComet RAT

Ukrainian police have arrested a 42-old-man on charges of infecting over 2,000 users across 50 countries with the DarkComet remote access trojan (RAT).
The man was arrested this week after police executed a search warrant at his residence in the city of Lviv, in Western Ukraine.
In a press release published today, Ukrainian police said they found a modified administrator panel for the DarkCommet RAT on the man's computer, along with the malware's installation files, and screenshots of infected victims' computers.
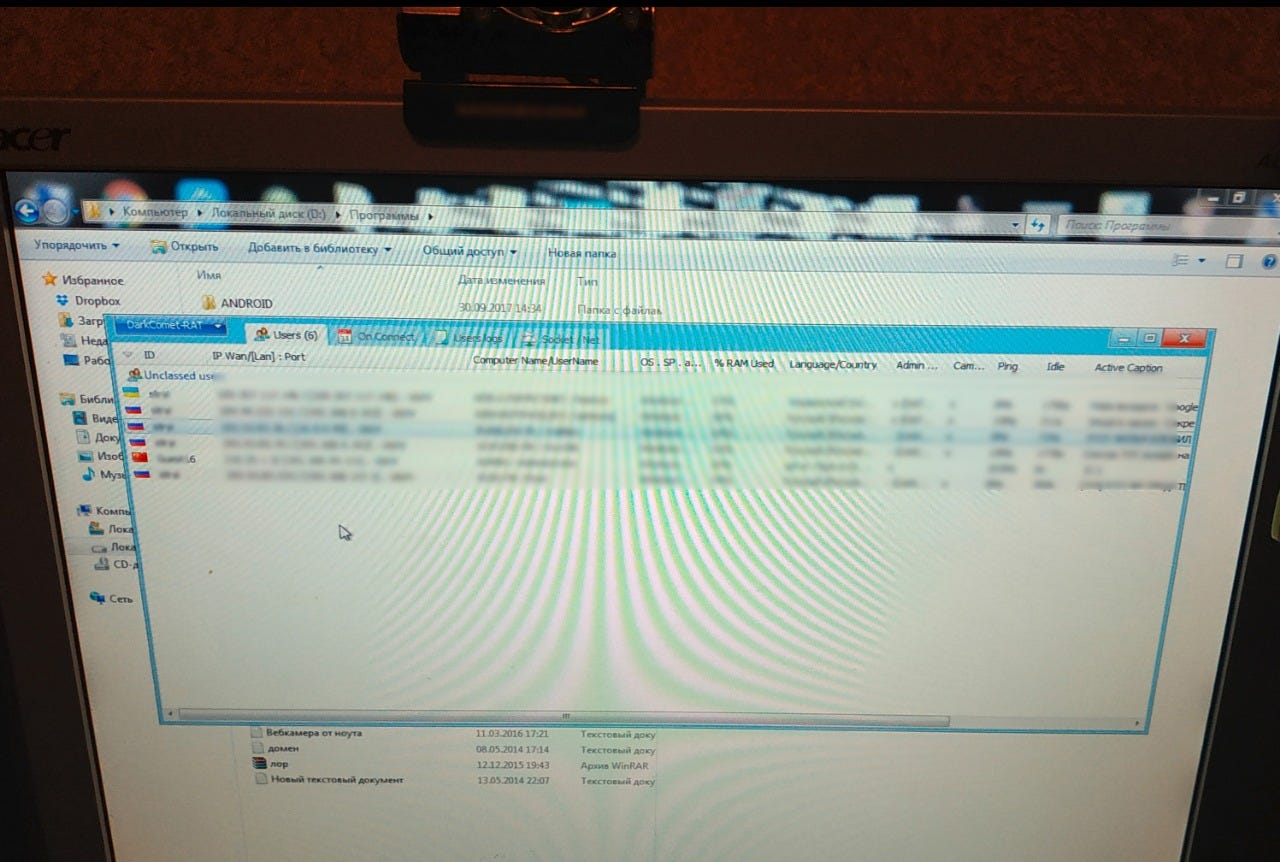
Image of the suspect's DarkComet admin panel opened on his home computer.
DarkComet was first released in 2008 and was initially advertised as a legitimate remote administration toolkit. Because of its intrusive spying capabilities, the tool was quickly adopted by malware developers, becoming a popular RAT within months [1, 2].
The tool's author, French software developer Jean-Pierre Lesueur, stopped developing the tool in 2012 after it became evident that most of the tool's use cases were for cybercrime and after reports surfaced that Syrian authorities had been using it to crack down on dissidents [1, 2].
Despite this, DarkComet development was picked up by other unofficial developers, and the RAT continued to plague users even to this day[1, 2], being recently spotted even in the arsenal and operations of North Korean government-backed hackers.
DarkCommet works as all your typical RATs, and is comprised of "clients" that are installed on infected computers, which send data back to a "server" module --the administration panel.
The RAT clients can take screenshots of users' screens, log keystrokes, steal documents, install additional malware on victims' computers, disable OS features, and steal passwords stored inside other local apps --just to name a few of its many features.
How to determine if you've been infected
Ukrainian police did not release the name of the suspect they arrested this week, but they did publish instructions on how to detect if users have been infected by this man's DarkComet campaign. The instructions are as follows:
- Press the Windows + R keys to open a Run dialog.
- Type "cmd" and press Enter.
- In the command prompt type "netstat -nao" and press Enter.
- In the list of current connections search for one trying to connect to a foreign IP address of 193.53.83.233, on port 1604 or 81.
If users find that their computer is trying to connect to such an IP address, then they've been infected by this particular DarkComet RAT campaign. At this point, victims should either wipe and reinstall their operating systems; use an antivirus program to remove the DarkComet malware; or contact a professional to do these things for them.
If you're a company, then you should contact your legal department first, as they might want to work with your IT staff to investigate and determine what data might have been stolen.
Ukrainian police are also interested in hearing from victims, most likely to build a better case against the suspect and determine the extent of the damage he caused.
Poor OpSec led to the man's arrest
But while Ukrainian police didn't reveal any details about the suspect or how they've tracked him down, it's pretty clear how they've done it to an external observer.
Searching for the IP address of 193.53.83.233 on Shodan, a search engine for Internet-connected devices, we found a listing for this IP that was marked as a "DarkComet trojan" command-and-control server.
The most obvious detail is that the IP address hosting this DarkComet administration panel wasn't assigned to the infrastructure of a data center, but to a regular residential internet service provider, meaning the suspect was most likely hosting the DarkComet server on his home computer.
Because of this operational security (OpSec) mistake, tracking the suspect's real-world identity was most likely a piece of cake for Ukrainian police, who only needed to send a formal request to the ISP to get the man's real name and home address.
How to discover and destroy spyware on your smartphone (in pictures)
More security coverage:
- City of Valdez, Alaska admits to paying off ransomware infection
- Magecart group hilariously sabotages competitor
- Atlanta ransomware attack hit 'mission critical' systems CNET
- Hackers use Drupalgeddon 2 and Dirty COW exploits to take over web servers
- Emotet malware runs on a dual infrastructure to avoid downtime and takedowns
- This remote access trojan just popped up on malware's most wanted list
- IE scripting engine becomes North Korean APT's favorite target in 2018
- Banking trojans, not ransomware, are the biggest threat now TechRepublic