Betting giant BetVictor leaked a list of its own internal systems passwords

(Image: ZDNet)
A popular betting platform left a password list for its internal systems on its website for anyone to find.
BetVictor, a Gibraltar-based betting site, has since removed the two-page document containing a list of links to back office systems, including usernames and passwords.
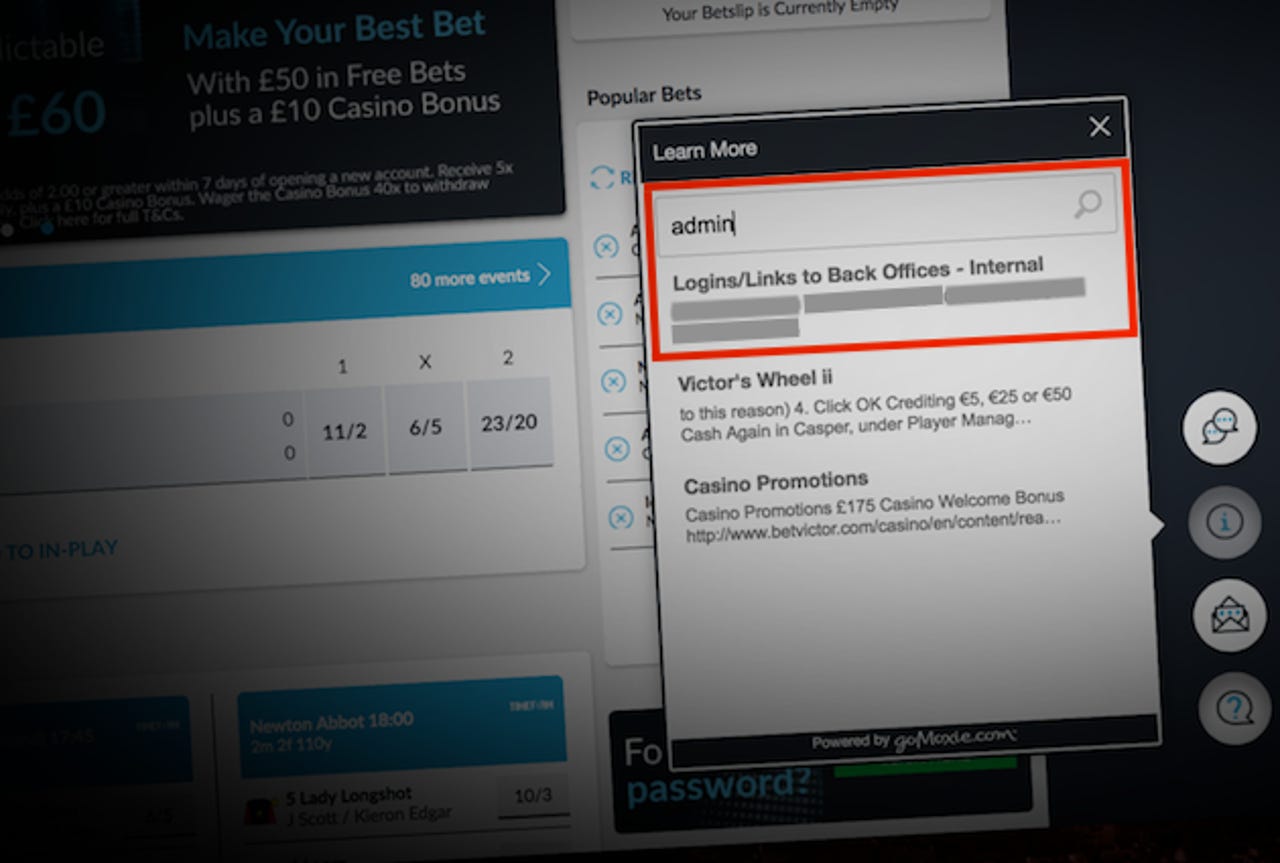
Chris Hogben found the document through the customer support search box on the company's homepage. The customer support pop-up allowed users to search the site's knowledge base of questions and answers.
"Logins/Links to Back Offices - Internal," read the document's title, which contained over two-dozen passwords to the company's trading platform, ticketing system, and Experian's identity verification service, Hogben told ZDNet.
The documents contained weak and easy-to-guess passwords, said Hogben. He found 11 passwords were in the Pwned Passwords dataset, a service offered by Troy Hunt's Have I Been Pwned site, which reveals passwords that have been exposed in data breaches.
Many of the systems were accessible externally -- though, none of the credentials were tested to avoid breaking computer hacking laws.
It's not known how long the document was left online. Hogben said the document dated back to 2015.
Hogben, who also blogged about the security issue, said that other internal documents were accessible through the public-facing customer support box.
"With access to any of these systems, it may be possible to access sensitive company information and potentially even user-specific data," he warned.
Scott Helme, a security researcher, helped responsibly disclose the security lapse.
"Of the documents found there were two that contained extensive combinations of usernames and passwords for what looked like various back-end and administrative systems used by the company," said Helme. "All it would have taken was someone malicious to scoop up these credentials and start logging in to systems as the URL for each system was also present."
"Who knows what access this would have granted them, what data would have been available and what damage could have been done," he warned.
After informing BetVictor of the exposure, the company quickly pulled the customer support system offline.
"We are still investigating this matter with our third party suppliers and cannot answer any specific questions at this point in time," said a spokesperson.
The company did not comment further, or respond to our questions -- such as if the company had changed any of its passwords.